
Industry 4.0 has introduced a new level of integration between IT and operations technology (OT) in modern industrial automation systems. This integration has led to higher demands on IT security because any security risks in the OT world can impact the IT world and vice versa. This blog post proposes an open source solution called xSPM (extensible security posture management) that can help organizations manage the security and compliance of their complete infrastructure, including on-premises, cloud, and SaaS services. In this post, we will discuss the benefits of xSPM and how it can help secure Industry 4.0.
Programmable logic controllers (PLCs)
Programmable logic controllers (PLCs) are industrial computers used in Industry 4.0 to control manufacturing processes. They are reliable, precise, and scalable, making them a suitable control solution for modern industrial automation systems. The new generation of PLCs have replaced classical manufacturing automation technology which was often proprietary and limited in scope.
The need for security in Industry 4.0
In today's manufacturing automation technology world, all participants must dynamically exchange data with each other across systems and company boundaries. This has resulted in higher demands on IT security. Even a single disruption in the IT or OT world can lead to massive downtime and production losses. Therefore, it is essential to ensure that security is integrated into all aspects of an organization’s infrastructure, from code creation to runtime.
What is xSPM
xSPM is an open-source solution that provides a set of best practices and tools to help organizations manage the security and compliance of their complete infrastructure.
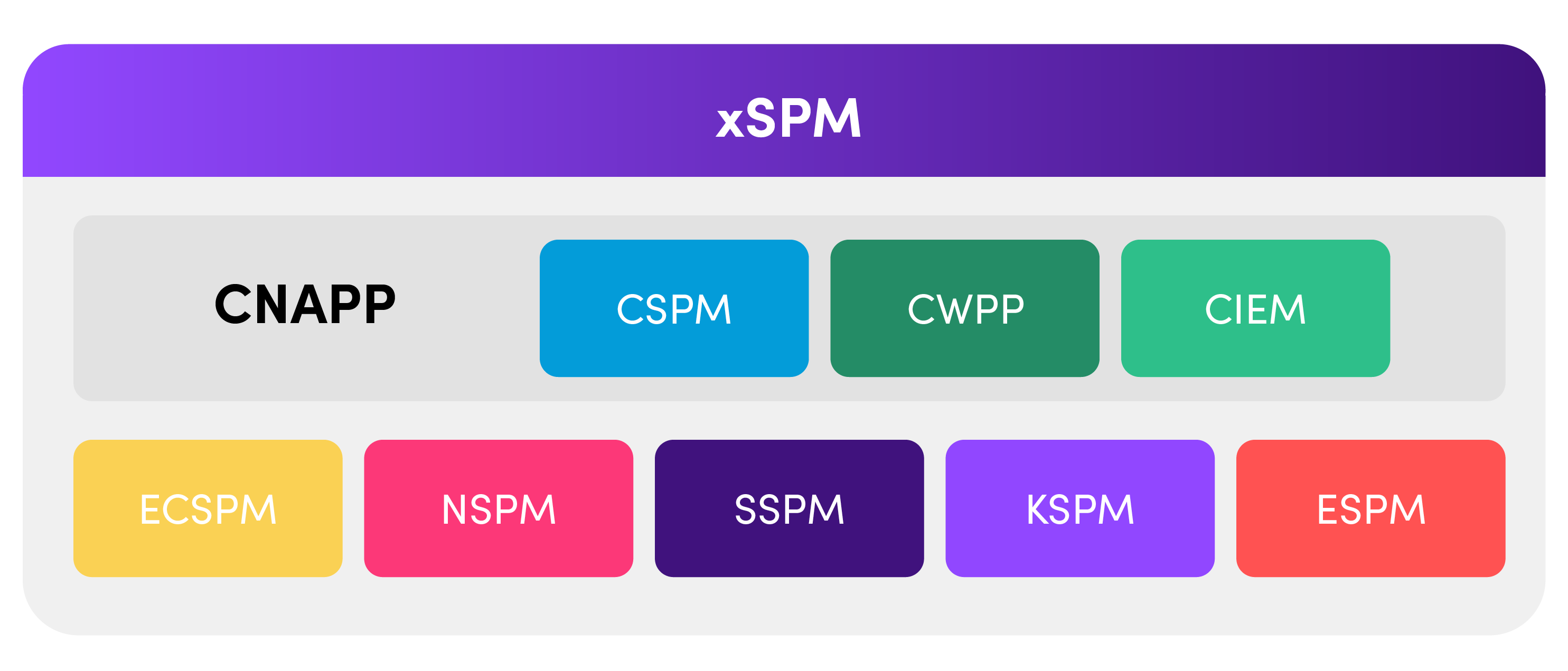
It includes several key components, such as cloud-native application protection (CNAPP), cloud security posture management (CSPM), cloud workload protection platforms (CWPP), cloud infrastructure entitlement management (CIEM), Kubernetes security posture management (KSPM), SaaS security posture management (SSPM,) and edge computing security posture management (ECSPM). Each component plays a crucial role in ensuring the overall security and compliance of the infrastructure.
Benefits of xSPM
The traditional security tools and approaches are limited in their scope, either designed for on-premises data centers or cloud-native applications, but not both. With an xSPM solution, organizations have a comprehensive solution that provides a unified view of their infrastructure security, allowing for continuous monitoring and the identification of potential security threats and vulnerabilities.By implementing xSPM, organizations can:
- Detect configuration drifts and minimize the risk of successful attacks and data breaches
- Ensure the security and compliance of their complete infrastructure, from code creation to runtime
- Have a comprehensive solution that provides a unified view of their infrastructure security, allowing for continuous monitoring and the identification of potential security threats and vulnerabilities.
Using cnspec to find old firmware and misconfigurations
As an example, let's take the PLCNext AXC F 2125 from Phonix Contact, which is based on the ARM Cortex-A9 processor and has an IEC 61131 runtime system. Cnspec is an open source tool that offers different options for scanning the Linux-based PLCNext device to detect old firmware and misconfigurations.There are two ways to scan the PLCNext using cnspec: via SSH provider or cnspec running on the PLCNext itself. In this guide, we will provide step-by-step instructions for both methods.
Scanning PLCNext via SSH provider
1. Install cnspec on your notebook2. Test the connection and establish a cnspec shell to the PLCNext by running the following command:
cnspec shell ssh admin@192.168.1.10 --ask-passfile("/etc/plcnext/arpversion").content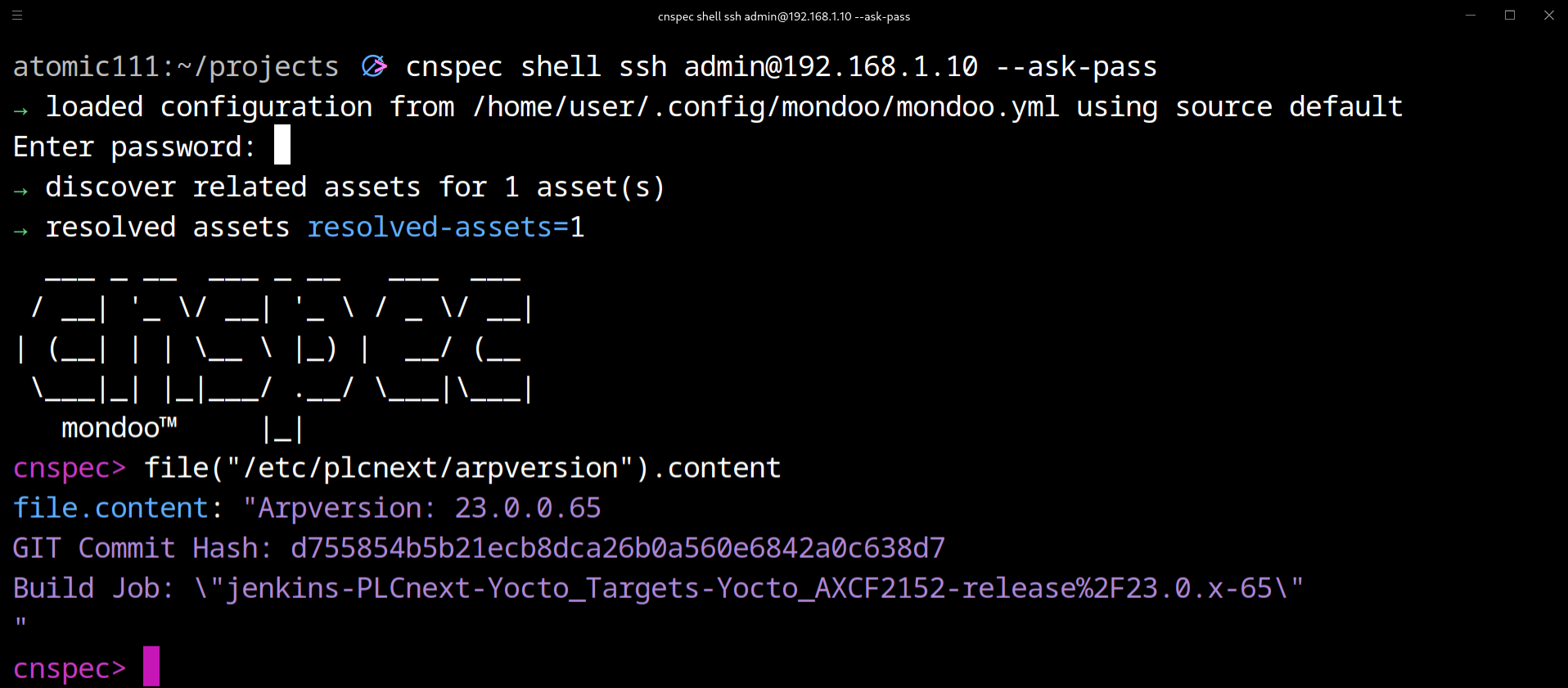
As we can see, we were able to connect via SSH to the PLCNext and were able to execute the first MQL command.
4. Download the PLCNext policy from the public cnspec-policies repository to perform a basic security check by running the following command:git clone https://github.com/mondoohq/cnspec-policies
Cloning into 'cnspec-policies'...
remote: Enumerating objects: 1075, done.
remote: Counting objects: 100% (149/149), done.
remote: Compressing objects: 100% (84/84), done.
remote: Total 1075 (delta 75), reused 115 (delta 61), pack-reused 926
Receiving objects: 100% (1075/1075), 699.81 KiB | 402.00 KiB/s, done.
Resolving deltas: 100% (690/690), done.cnspec scan ssh admin@192.168.1.10 -f cnspec-policies/community/mondoo-phoenix-plcnext-security.mql.yaml --ask-pass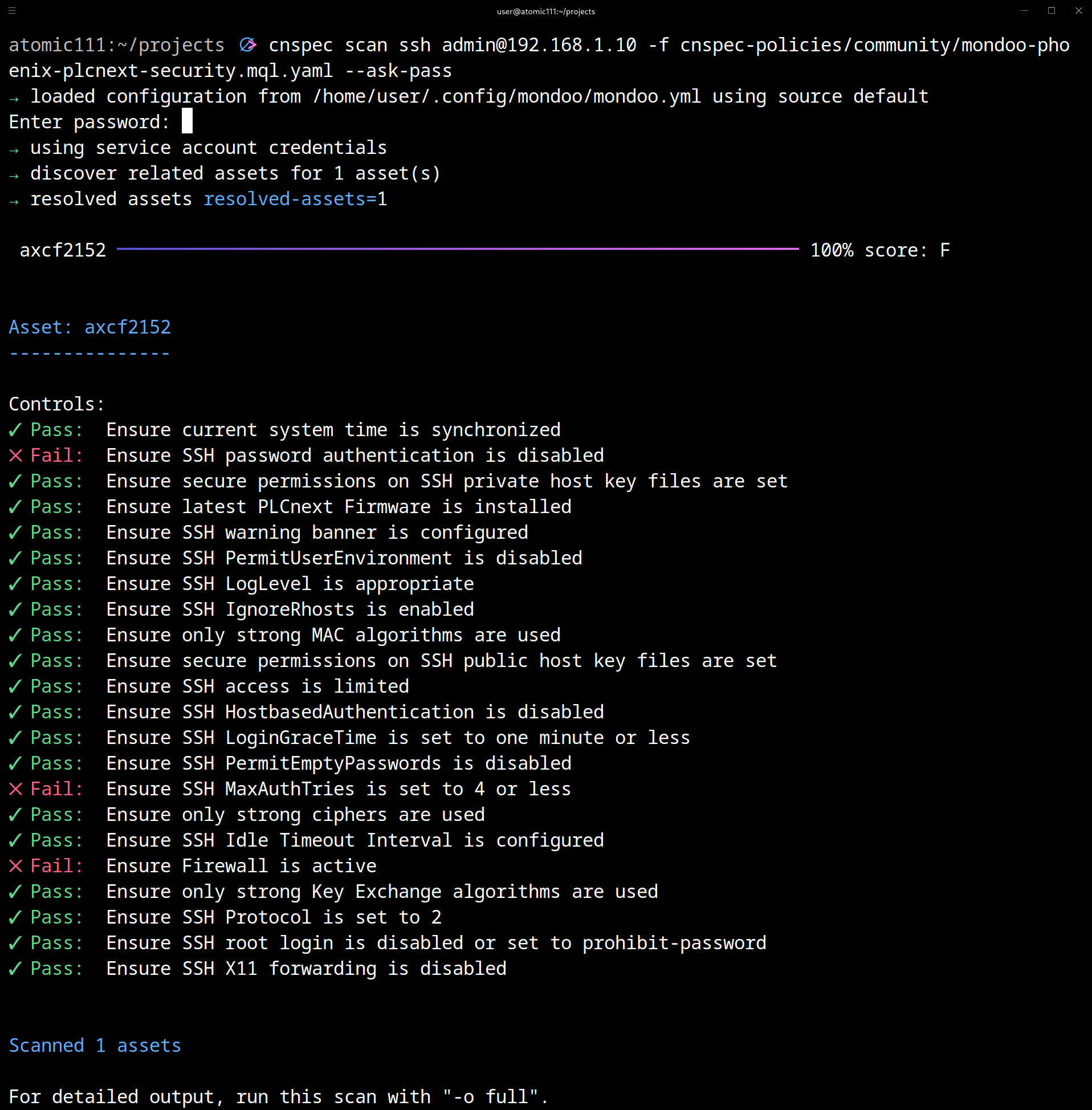
Scanning PLCNext via cnspec running on PLCNext
To scan the PLCNext via cnspec running on the PLCNext itself, follow these steps:
- Execute the following commands to install cnspec on the PLCNext:
# change working directory
admin@axcf2152:~$ cd /media/rfs/rw/
# create a mondoo directory
admin@axcf2152:/media/rfs/rw$ mkdir mondoo
# change directory to mondoo
admin@axcf2152:/media/rfs/rw$ cd mondoo
# download the cnspec tool
admin@axcf2152:/media/rfs/rw/mondoo$ curl -L https://install.mondoo.com/package/cnspec/linux/armv7/tar.gz/latest/download -o cnspec.tar
.gz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 97 100 97 0 0 244 0 --:--:-- --:--:-- --:--:-- 245
100 51.4M 100 51.4M 0 0 3049k 0 0:00:17 0:00:17 --:--:-- 2553k
# decompress the cnspec tool
admin@axcf2152:/media/rfs/rw/mondoo$ tar xzf cnspec.tar.gz
# delete the compressed cnspec tool
admin@axcf2152:/media/rfs/rw/mondoo$ rm cnspec.tar.gz
# test if cnspec is working
admin@axcf2152:/media/rfs/rw/mondoo$ ./cnspec version
cnspec 7.18.1 (c0c039b, 2023-02-22T11:37:57Z)
./cnspec login --token 'eyJhbGciOiJFUzM4NCIsInR5cCI6IkpXVCJ9.eyJhcGlfZW5kcG9pbnQiOiJodHRwczovL3VzL
mFwaS5tb25kb28uY29tIiwiYXVkIjpbIm1vbmRvbyJdLCJjZXJ0X3ZhbGlkX3VudGlsIjoiOTk5OS0xMi0zMVQyMzo1OTo1OVoiLCJkZXNjIjoiIiwiZXhwIjoxNjc3MDc4NzU1
LCJpYXQiOjE2NzcwNzgxNTUsImlzcyI6Im1vbmRvby9hbXMiLCJsYWJlbHMiOm51bGwsIm5iZiI6MTY3NzA3ODE1NSwib3duZXIiOiIiLCJzcGFjZSI6Ii8vY2FwdGFpbi5hcGk
ubW9uZG9vLmFwcC9zcGFjZXMvZWFnZXItd2lsc29uLTc2NTg2OCIsInN1YiI6Ii8vY2FwdGFpbi5hcGkubW9uZG9vLmFwcC91c2Vycy8yMU1EU1EzalBKTUtEczFXd3FyOVZ5bV
hmUUsifQ.-wAvMWVhxLsnwOKKa-ok83tCKJFsyAZ3GjtdP1TPSgfGnDkfSH5BZTDrsmqM6rFtz8RKDpgXLTcRxt-TGYuuY0_ugVAeqUoZQD7q0Ca-ZGdi-ZeIMNVWQmNEEabRib
HM'
→ token will expire at Wed, 22 Feb 2023 15:12:35 UTC
→ saving config path=/opt/plcnext/.config/mondoo/mondoo.yml
→ config file does not exist, create a new one path=/opt/plcnext/.config/mondoo/mondoo.yml
→ client //agents.api.mondoo.app/spaces/eager-wilson-765868/agents/2M6CBInWv7K1OZJaeMkUebdu4Bh has logged in successfully
admin@axcf2152:/media/rfs/rw/mondoo$ ./cnspec scan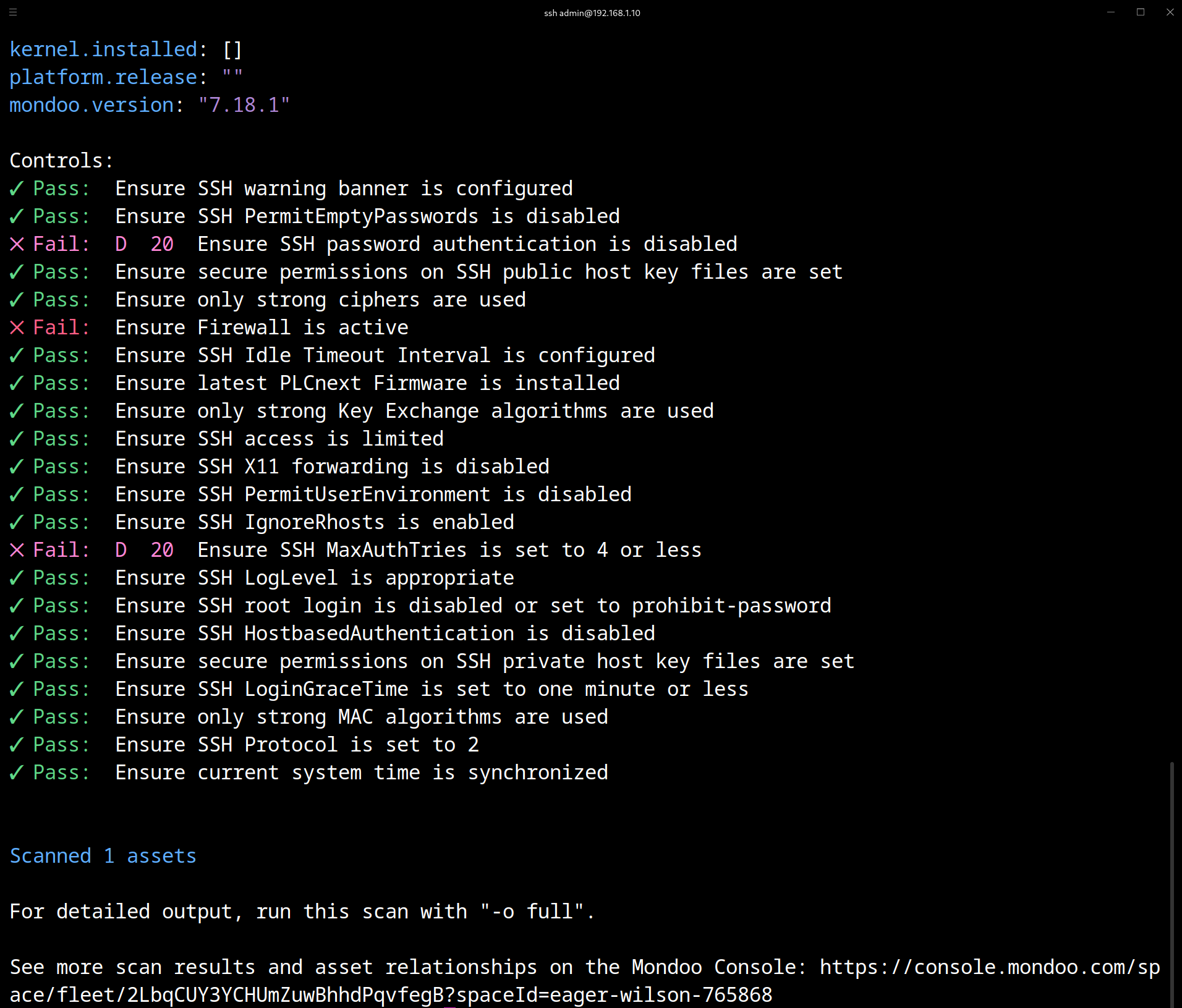
root@axcf2152:/media/rfs/rw/mondoo# cat /etc/cron.hourly/mondoo
#!/bin/sh
/media/rfs/rw/mondoo/cnspec scan --config /opt/plcnext/.config/mondoo/mondoo.ymlOnce the cnspec scan is completed, you can easily view the results by copying the link from the command line interface and visiting the Mondoo Dashboard. From there, you can see all of the identified vulnerabilities and receive recommendations on how to fix them.
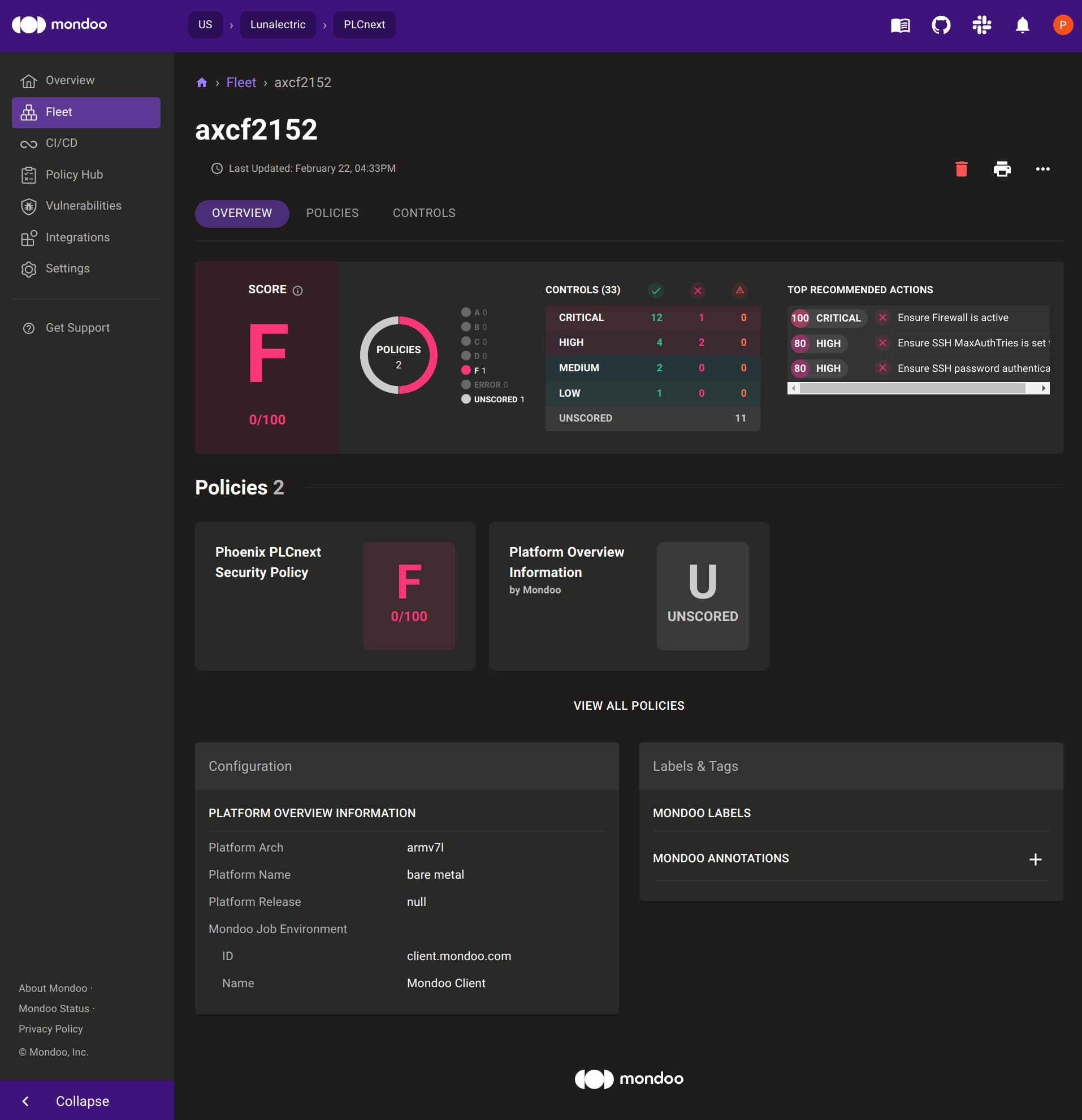
Mondoo’s security solution provides a comprehensive approach to identifying vulnerabilities and misconfigurations across both IT and OT systems. By regularly scanning your systems, you can proactively identify and fix potential security issues before they become a problem.
If you have questions or need help with the process, the Mondoo team is available to assist you on Slack. Don’t hesitate to reach out if you need support.



