What is patch management?
Patch management is the process of distributing and applying updates to software, such as operating systems (OS), platforms, and applications. It involves identifying out-dated software within your infrastructure, applying patches to that software, and validating the installation of those patches. These patches are often necessary to fix errors in the software, which are often referred to as vulnerabilities or bugs.
Why is patch management important?
Patch management is important for three main reasons:
- Security: Patch management fixes vulnerabilities in your software (OS, platform, application) that are susceptible to exploitation. It helps your organization to reduce the risk of cyberattacks.
- Compliance: Organizations are often required by regulators to follow strict guidelines because of the constant increase in cyberattacks. Patch management is a necessary part of complying to certain standards, such as PCI-DSS, HIPAA, SOC2, ISO27001, or BSI.
- System uptime: Patch management ensures your software is kept up-to-date and running smoothly without errors causing system downtime.
Finding missing patches with Mondoo
As a part of its full-stack security solution, Mondoo identifies what important patches are missing from your systems. For this blog post, I set up some vagrant Linux machines with out-of-date operating systems. I’ll use them to walk through some different ways that Mondoo shows you the patches needed.
config.vm.define "win2016" do |win2016|
win2016.vm.box = "gusztavvargadr/windows-server-standard"
win2016.vm.box_version = "1607.0.2108"
win2016.vm.network "private_network", ip: '192.168.56.252'
end
config.vm.define "win2019" do |win2019|
win2019.vm.box = "gusztavvargadr/windows-server"
win2019.vm.box_version = "1809.0.2112"
win2019.vm.network "private_network", ip: '192.168.56.230'
end
config.vm.define "win2022" do |win2022|
win2022.vm.box = "gusztavvargadr/windows-server"
win2022.vm.box_version = "2102.0.2112"
win2022.vm.network :private_network, ip: "192.168.56.236"
end
config.vm.define "win10" do |win10|
win10.vm.box = "gusztavvargadr/windows-10"
win10.vm.network "private_network", ip: '192.168.56.249'
end
Prerequisite: Please create a free account on console.mondoo.com.
Mondoo offers different options for scanning a Linux vagrant system:
Option 1: Install Mondoo Client on the Windows system
Option 2: Use vagrant transporter
Option 3: Use SSH transporter
Option 1: Find missing patches with Mondoo
1. Login to the vagrant Windows 2016 system via Remote Desktop Protocol (RDP):
atomic111: ∅> xfreerdp /u:vagrant /v:192.168.56.252:3389 /h:2048
/w:2048 /p:'vagrant'
Open a Windows PowerShell as an administrator:
2. Install Mondoo Client:
A. Log into your account at console.mondoo.com
B. Go to the Integrations tab and select Windows
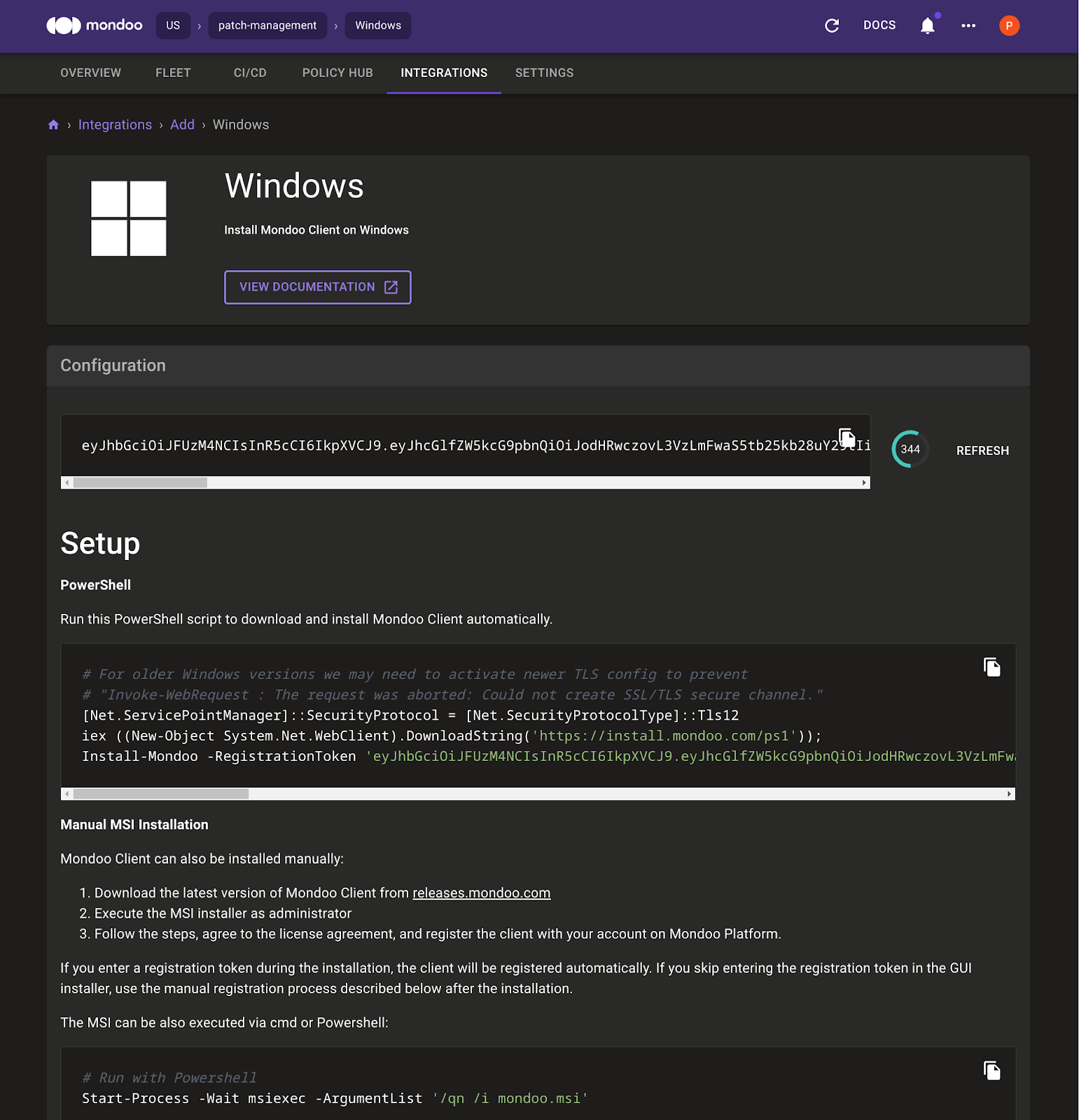
C. Set the PowerShell execution policy:
Set-ExecutionPolicy RemoteSigned -scope CurrentUser
D. Copy the CLI commands that Mondoo provides and paste them in the Windows 2016 PowerShell.
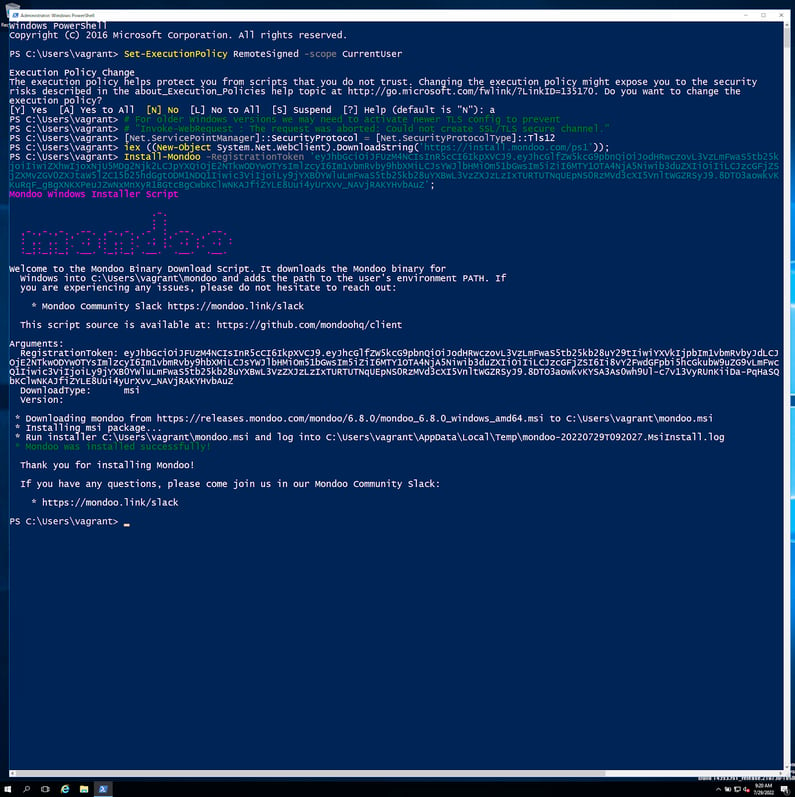
E. After the Mondoo Client installation finishes, add the Mondoo path and type `mondoo status` to verify that Mondoo Client is registered and working. It should look like this:
PS C:\Users\vagrant> $env:Path = 'C:\Program Files\Mondoo\;'
+ $env:Path
PS C:\Users\vagrant> mondoo status
→ loaded configuration from C:\ProgramData\Mondoo\mondoo.yml
using source default
→ Hostname: WIN-UO68HGC3S3I
→ IP: 10.0.2.15
→ Platform: windows
→ Release: 14393
→ Time: 2022-07-29T09:22:09Z
→ Version: 6.8.0 (API Version: 6)
→ API ConnectionConfig: https://us.api.mondoo.com
→ API Status: SERVING
→ API Time: 2022-07-29T09:22:15Z
→ API Version: 6
→ Space: //captain.api.mondoo.app/spaces/determined-yonath
-835445
→ Client: //agents.api.mondoo.app/spaces/determined-yonath
-835445/agents/2Cc0CvGWW9SlxWG2JbqsTxfgmEB
→ Service Account: //agents.api.mondoo.app/spaces/determined
-yonath-835445/serviceaccounts/2Cc0Ctf346RDy9WwWd6KK9ggM6j
→ client is registered
→ client authenticated successfully
PS C:\Users\vagrant>
After a Windows restart, the installation path is automatically added to the PowerShell path variable.
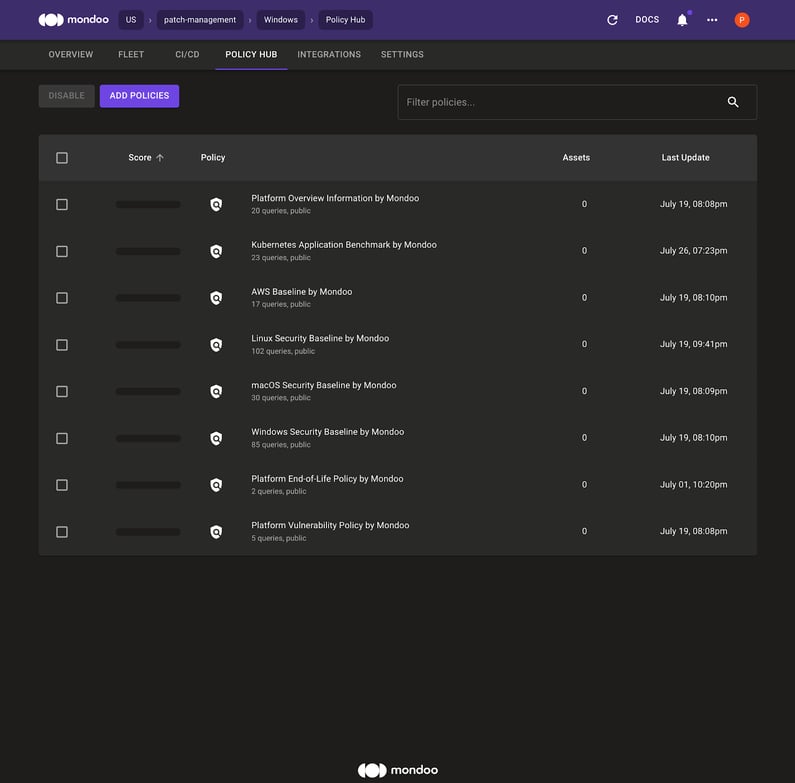
F. Quickly verify that the following policies are enabled for your space:
- Platform End-of-Life Policy by Mondoo
- Platform Vulnerability Policy by Mondoo
Your Policy Hub should look like this:
3. Run the Mondoo scan in PowerShell:
mondoo scan local
Mondoo Client connects to the Mondoo backend and downloads the enabled policies. After the scan, Mondoo Client reports results back to the Mondoo backend.
PS C:\Users\vagrant> mondoo scan local
→ Mondoo 6.8.0 (Space: "//captain.api.mondoo.app/spaces/determined-yonath-835445", Service Account: "2Cc0Ctf346RDy9WwWd6KK9ggM6j", Managed Client: "2Cc0CvGWW9SlxWG2JbqsTxfgmEB")
→ loaded configuration from C:\ProgramData\Mondoo\mondoo.yml using source default
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=1
→ establish connection to asset WIN-UO68HGC3S3I (baremetal)
███████████████████████████████████████████████████████████████████████████ 100% WIN-UO68HGC3S3I
→ send all results asset=WIN-UO68HGC3S3I
→ scan took 3m13.2810456s
Data queries:
platform.arch: "64-bit"
os.hostname: "WIN-UO68HGC3S3I"
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "KB5008207"
Mrn: "//vadvisor.api.mondoo.app/advisories/KB5008207"
cves: [
0: {
ID: "CVE-2021-43235"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2021-43235"
cvss: [
... 1979 more lines ...
os.uptime: 16 minutes 59 seconds
packages.list.length: 20
platform.title: "Microsoft Windows Server 2016 Standard Evaluation"
mondoo.version: "6.8.0"
platform.eol.date: 2022-11-11 00:00:00 +0000 GMT
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
platform.release: "14393"
Controls:
✕ Fail: Ensure 'Audit Account Lockout' is set to include 'Failure'
✓ Pass: Ensure 'Audit: Shut down system immediately if unable to log security audits' is set to 'Disabled'
✕ Fail: Ensure 'Audit Other Logon/Logoff Events' is set to 'Success and Failure'
✓ Pass: Ensure 'Network access: Allow anonymous SID/Name translation' is set to 'Disabled'
! Error: Ensure 'Security: Specify the maximum log file size (KB)' is set to 'Enabled: 196,608 or greater'
✓ Pass: Ensure 'Audit Authentication Policy Change' is set to include 'Success'
! Error: Ensure 'Security: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✕ Fail: Ensure the platform is not End-of-Life
! Error: Ensure 'Application: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
✓ Pass: Ensure 'Enable Structured Exception Handling Overwrite Protection (SEHOP)' is set to 'Enabled'
✕ Fail: Ensure no known platform CVEs exist
✕ Fail: Ensure 'Audit Application Group Management' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Authorization Policy Change' is set to include 'Success'
! Error: Ensure 'Setup: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
! Error: Ensure 'Application: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✕ Fail: Ensure 'Audit Other Object Access Events' is set to 'Success and Failure'
✓ Pass: Ensure 'Audit Special Logon' is set to include 'Success'
✓ Pass: Platform is not end-of-life
✕ Fail: Ensure 'Audit Other Policy Change Events' is set to include 'Failure'
! Error: Ensure 'Do not allow LPT port redirection' is set to 'Enabled'
! Error: Ensure 'Require user authentication for remote connections by using Network Level Authentication' is set to 'Enabled'
! Error: Ensure 'Do not allow COM port redirection' is set to 'Enabled'
✕ Fail: Ensure 'Audit MPSSVC Rule-Level Policy Change' is set to 'Success and Failure'
! Error: Ensure 'Always prompt for password upon connection' is set to 'Enabled'
! Error: Ensure 'Network security: Allow Local System to use computer identity for NTLM' is set to 'Enabled'
✓ Pass: Ensure 'Audit Logon' is set to 'Success and Failure'
! Error: Ensure 'Relax minimum password length limits' is set to 'Enabled'
! Error: Ensure 'Allow users to connect remotely by using Remote Desktop Services' is set to 'Disabled'
! Error: Ensure 'Network security: Allow LocalSystem NULL session fallback' is set to 'Disabled'
! Error: Ensure 'Do not allow drive redirection' is set to 'Enabled'
! Error: Ensure 'Do not allow passwords to be saved' is set to 'Enabled'
✓ Pass: Ensure 'Audit Security Group Management' is set to include 'Success'
! Error: Ensure 'Network access: Restrict clients allowed to make remote calls to SAM' is set to 'Administrators: Remote Access: Allow'
✓ Pass: Ensure 'Audit Audit Policy Change' is set to include 'Success'
! Error: Ensure 'Turn off multicast name resolution' is set to 'Enabled'
✕ Fail: Ensure 'Audit File Share' is set to 'Success and Failure'
✓ Pass: Ensure 'Audit Logoff' is set to include 'Success'
✓ Pass: Ensure 'Network security: LDAP client signing requirements' is set to 'Negotiate signing' or higher
✕ Fail: Ensure 'Audit Credential Validation' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Sensitive Privilege Use' is set to 'Success and Failure'
! Error: Ensure 'Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings' is set to 'Enabled'
✓ Pass: Ensure 'Network access: Restrict anonymous access to Named Pipes and Shares' is set to 'Enabled'
! Error: Ensure 'Network security: Configure encryption types allowed for Kerberos' is set to 'AES128_HMAC_SHA1, AES256_HMAC_SHA1, Future encryption types'
✓ Pass: Ensure 'Maximum password age' is set to '365 or fewer days, but not 0'
✓ Pass: Ensure 'Network access: Let Everyone permissions apply to anonymous users' is set to 'Disabled'
! Error: Ensure 'NetBT NodeType configuration' is set to 'Enabled: P-node (recommended)'
✓ Pass: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts' is set to 'Enabled'
✕ Fail: Ensure 'Audit Group Membership' is set to include 'Success'
! Error: Ensure 'Network security: LAN Manager authentication level' is set to 'Send NTLMv2 response only. Refuse LM&NTLM'
✕ Fail: Ensure 'Network access: Do not allow storage of passwords and credentials for network authentication' is set to 'Enabled'
✕ Fail: Ensure 'Minimum password length' is set to '14 or more character(s)'
✓ Pass: Ensure 'Audit Other System Events' is set to 'Success and Failure'
! Error: Ensure 'Setup: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
! Error: Ensure 'Require secure RPC communication' is set to 'Enabled'
✓ Pass: Ensure 'Audit System Integrity' is set to 'Success and Failure'
! Error: Ensure 'Set time limit for disconnected sessions' is set to 'Enabled: 1 minute'
! Error: Ensure 'System: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
✕ Fail: Ensure 'Apply UAC restrictions to local accounts on network logons' is set to 'Enabled'
✕ Fail: Ensure no known platform advisories exist
✕ Fail: Ensure 'Audit PNP Activity' is set to include 'Success'
! Error: Ensure 'WDigest Authentication' is set to 'Disabled'
✕ Fail: Ensure 'Enforce password history' is set to '24 or more password(s)'
✕ Fail: Ensure 'Audit Removable Storage' is set to 'Success and Failure'
✕ Fail: Ensure 'Configure SMB v1 client driver' is set to 'Enabled: Disable driver (recommended)'
✓ Pass: Ensure 'Network security: Do not store LAN Manager hash value on next password change' is set to 'Enabled'
! Error: Ensure 'Set client connection encryption level' is set to 'Enabled: High Level'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) servers' is set to 'Require NTLMv2 session security, Require 128-bit encryption'
✕ Fail: Ensure 'Audit IPsec Driver' is set to 'Success and Failure'
✕ Fail: Ensure 'Network access: Named Pipes that can be accessed anonymously' is set to 'None'
✕ Fail: Ensure 'Audit User Account Management' is set to 'Success and Failure'
! Error: Ensure 'Network access: Shares that can be accessed anonymously' is set to 'None'
✓ Pass: Ensure 'Audit Security State Change' is set to include 'Success'
✕ Fail: Ensure 'Audit Detailed File Share' is set to include 'Failure'
! Error: Ensure 'Do not delete temp folders upon exit' is set to 'Disabled'
! Error: Ensure 'Set time limit for active but idle Remote Desktop Services sessions' is set to 'Enabled: 15 minutes or less, but not Never (0)'
✕ Fail: Ensure 'Audit Security System Extension' is set to include 'Success'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) clients' is set to 'Require NTLMv2 session security, Require 128-bit encryption'
! Error: Ensure 'System: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✓ Pass: Ensure 'Store passwords using reversible encryption' is set to 'Disabled'
✕ Fail: Ensure 'Audit Process Creation' is set to include 'Success'
! Error: Ensure 'Do not allow supported Plug and Play device redirection' is set to 'Enabled'
✕ Fail: Ensure 'Minimum password age' is set to '1 or more day(s)'
✓ Pass: Ensure 'Password must meet complexity requirements' is set to 'Enabled'
! Error: Ensure 'Configure SMB v1 server' is set to 'Disabled'
✕ Fail: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts and shares' is set to 'Enabled'
! Error: Ensure 'Network Security: Allow PKU2U authentication requests to this computer to use online identities' is set to 'Disabled'
! Error: Ensure 'Require use of specific security layer for remote (RDP) connections' is set to 'Enabled: SSL'
✓ Pass: Ensure 'Network access: Sharing and security model for local accounts' is set to 'Classic - local users authenticate as themselves'
✕ Fail: secpol.privilegerights['SeDebugPrivilege'].length == null
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 7.2 KB5007192 14393/4583 14393/4770 KB5007192
■ 7.5 KB5008207 14393/4583 14393/4825 KB5008207
■ 10 KB5009546 14393/4583 14393/4886 KB5009546
Overall CVSS score: 10.0
Summary
========================
Target: WIN-UO68HGC3S3I
Score: C 34/100 (100% completed)
✓ Passed: ████ 25% (22)
✕ Failed: █████ 36% (32)
! Errors: ██████ 39% (35)
» Skipped: 0% (0)
Policies:
F 0 Platform Vulnerability Policy by Mondoo
. .. Platform Overview Information by Mondoo
C 42 Windows Security Baseline by Mondoo
B 60 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2Cc11UnUgMvE2QuiBhMXUiejrzM?spaceId=determined-yonath-835445
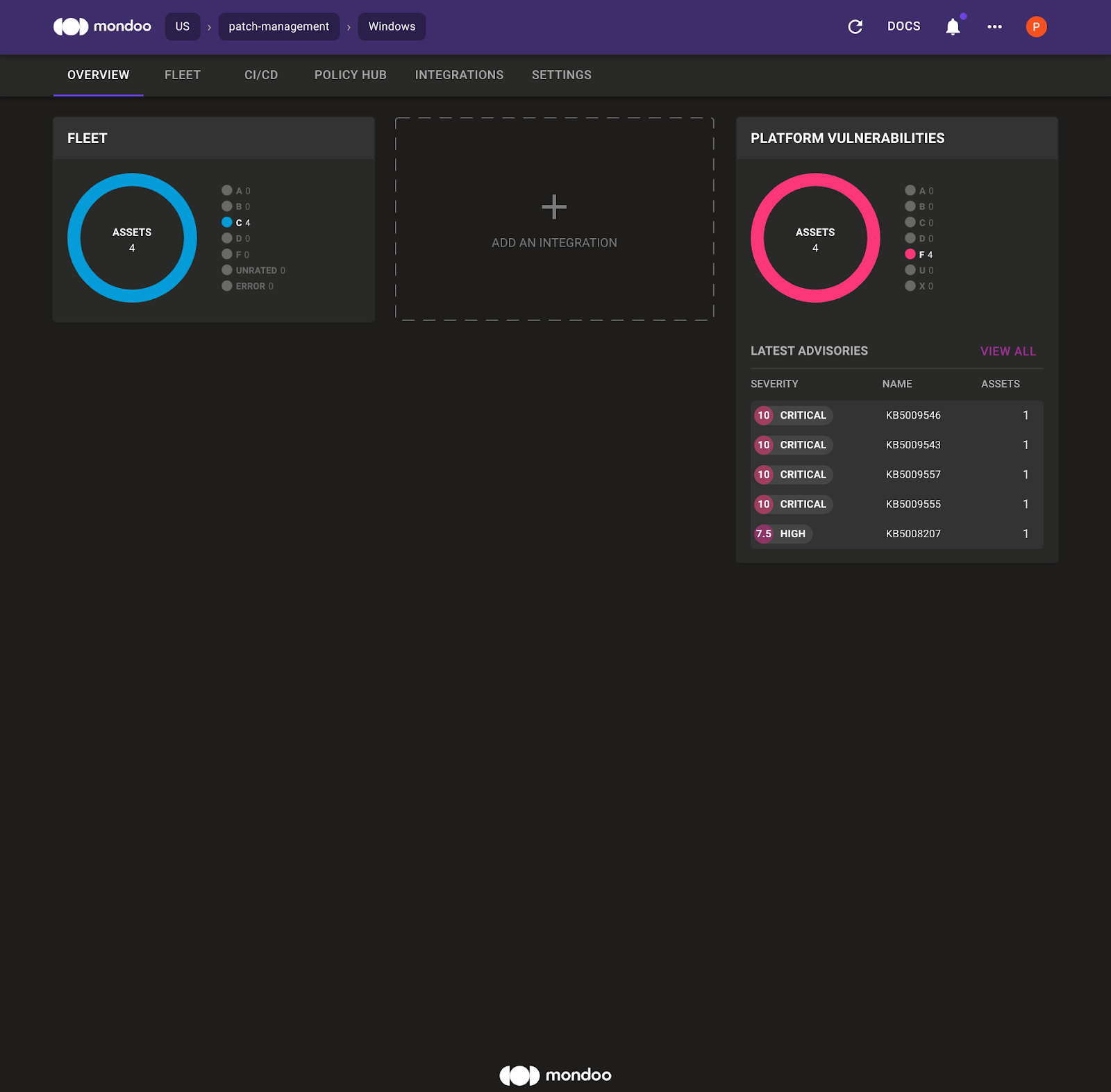
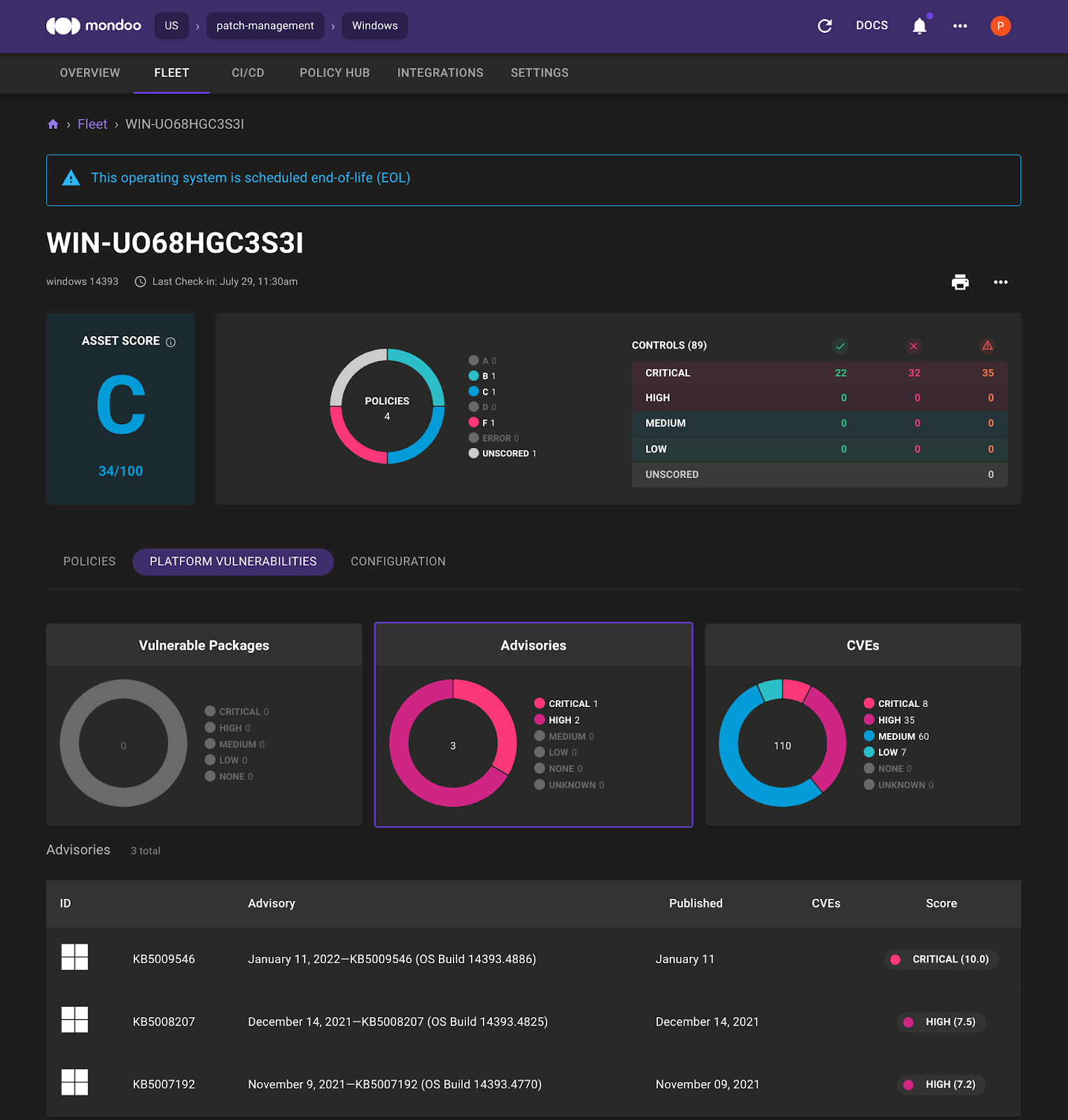
Click the report URL to open the Mondoo Space overview page, which shows the Windows 2016 asset and the top vulnerabilities within the Mondoo Space.
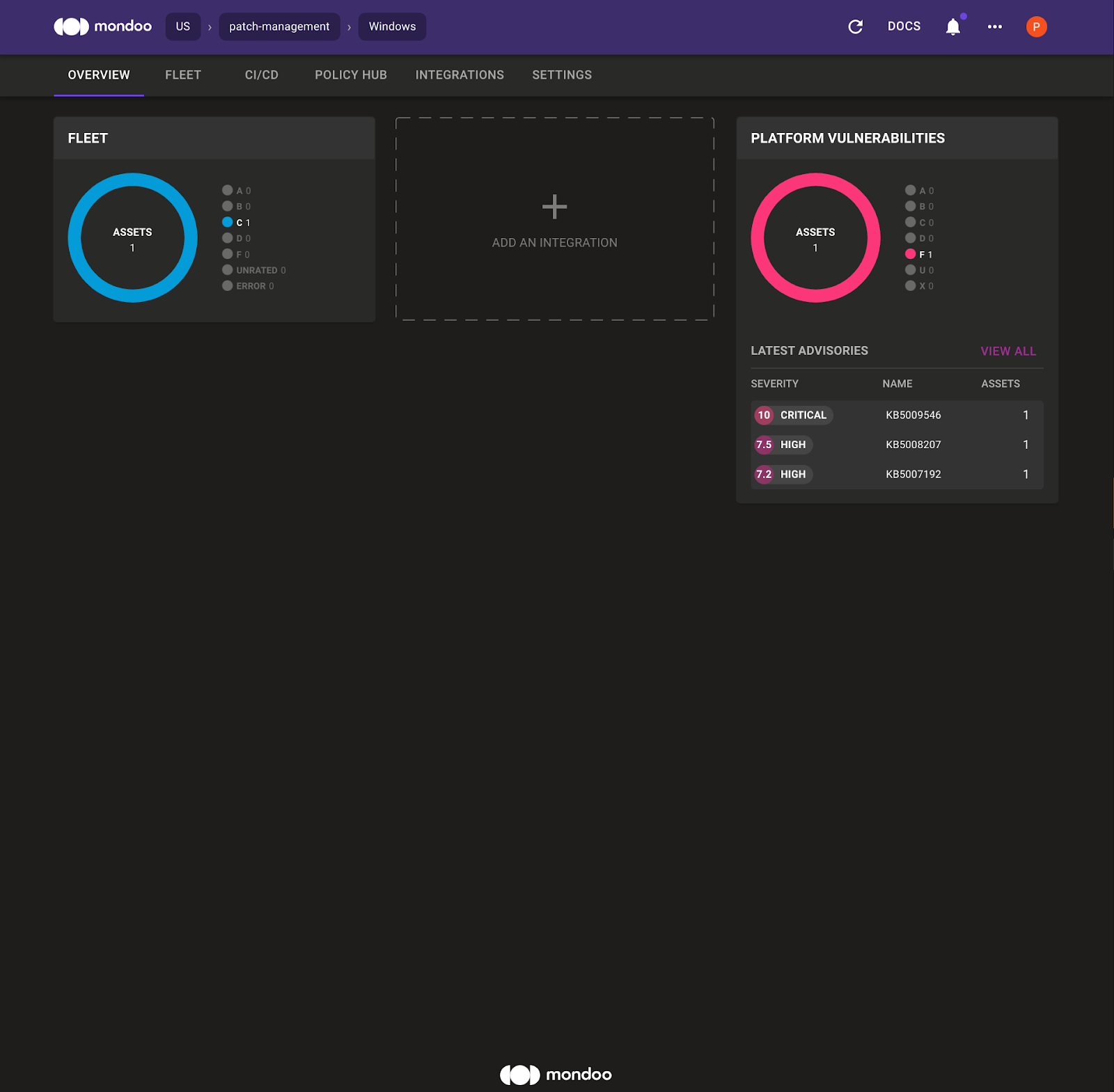
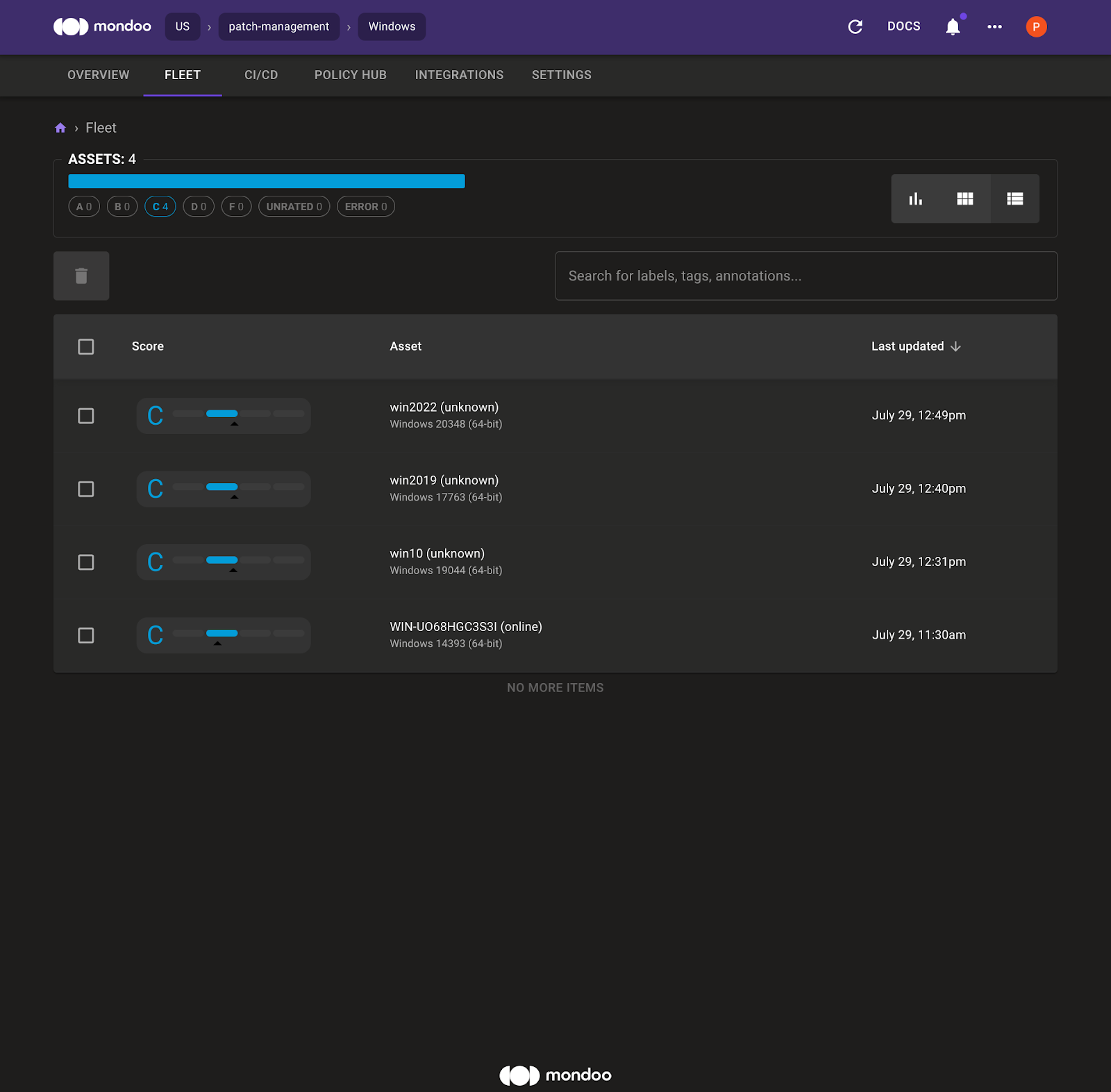
4. Select Fleet and then select the Windows asset to see the Mondoo asset overview page for the Windows 2016 system.
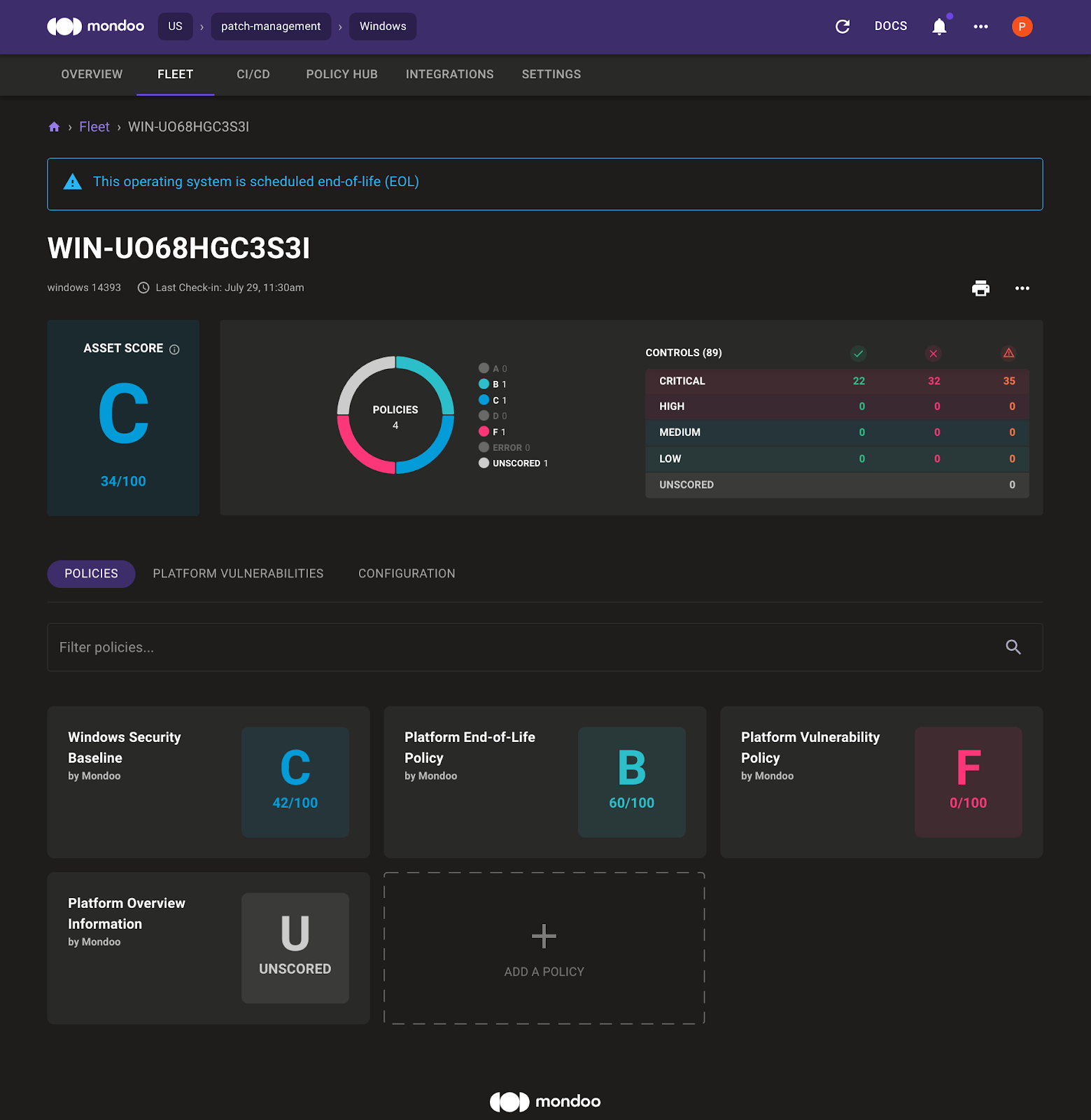
In the system overview, the Mondoo Dashboard highlights that the Windows 2016 operating system is close to the end-of-life date. By default there is also a Windows Security Baseline enabled. Select Platform Vulnerabilities to see the Advisories and CVE that affect this system. Mondoo shows:
- Which KB you must install to fix the vulnerability
- How critical the vulnerability is
- An overview of the advisories and CVEs
Option 2: Scan a Windows vagrant machine via vagrant transporter
1. Install and register Mondoo Client on your host system running the vagrant Windows 2016 system.
2. Run the following command:
atomic111: ∅> mondoo scan vagrant win2016
→ Mondoo 6.8.0 (Space: "//captain.api.mondoo.app/spaces/relaxed-poincare-384428", Service Account: "21jsOJLO853ISdwRv2KyhG3VGHu", Manag
ed Client: "21jrdvKi4dnW95pVsvoH3zfEFQU")
→ loaded configuration from /home/user/.config/mondoo/mondoo.yml using source default
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=1
→ establish connection to asset win2016 (virtualmachine)
███████████████████████████████████████████████████████████████████████████ 100% debian-9
→ send all results asset=win2016
→ scan took 2m14.065041897s
Data queries:
platform.eol.date: 2022-11-11 01:00:00 +0100 CET
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "KB5008207"
Mrn: "//vadvisor.api.mondoo.app/advisories/KB5008207"
cves: [
0: {
ID: "CVE-2021-43235"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2021-43235"
cvss: [
... 1979 more lines ...
Controls:
✕ Fail: Ensure 'Network access: Do not allow storage of passwords and credentials for network authentication' is set to 'Enabled'
! Error: Ensure 'Security: Specify the maximum log file size (KB)' is set to 'Enabled: 196,608 or greater'
✓ Pass: Ensure 'Network access: Restrict anonymous access to Named Pipes and Shares' is set to 'Enabled'
✕ Fail: Ensure 'Audit IPsec Driver' is set to 'Success and Failure'
! Error: Ensure 'Do not allow LPT port redirection' is set to 'Enabled'
✕ Fail: Ensure 'Audit Removable Storage' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Process Creation' is set to include 'Success'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) servers' is set to 'Require NTLMv
2 session security, Require 128-bit encryption'
✓ Pass: Ensure 'Password must meet complexity requirements' is set to 'Enabled'
✕ Fail: Ensure 'Audit PNP Activity' is set to include 'Success'
✕ Fail: Ensure 'Audit File Share' is set to 'Success and Failure'
✕ Fail: Ensure 'Enforce password history' is set to '24 or more password(s)'
✕ Fail: Ensure no known platform CVEs exist
✕ Fail: Ensure 'Apply UAC restrictions to local accounts on network logons' is set to 'Enabled'
✕ Fail: Ensure 'Audit Detailed File Share' is set to include 'Failure'
✓ Pass: Ensure 'Audit Authentication Policy Change' is set to include 'Success'
! Error: Ensure 'Require user authentication for remote connections by using Network Level Authentication' is set to 'Enabled'
! Error: Ensure 'Configure SMB v1 server' is set to 'Disabled'
! Error: Ensure 'Require secure RPC communication' is set to 'Enabled'
! Error: Ensure 'Do not allow passwords to be saved' is set to 'Enabled'
✓ Pass: Ensure 'Store passwords using reversible encryption' is set to 'Disabled'
✓ Pass: Ensure 'Audit System Integrity' is set to 'Success and Failure'
✓ Pass: Ensure 'Audit Logoff' is set to include 'Success'
✓ Pass: Ensure 'Audit Special Logon' is set to include 'Success'
✓ Pass: Ensure 'Audit Other System Events' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Other Logon/Logoff Events' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Application Group Management' is set to 'Success and Failure'
✓ Pass: Ensure 'Enable Structured Exception Handling Overwrite Protection (SEHOP)' is set to 'Enabled'
! Error: Ensure 'Allow users to connect remotely by using Remote Desktop Services' is set to 'Disabled'
✕ Fail: Ensure 'Audit Account Lockout' is set to include 'Failure'
✕ Fail: Ensure 'Audit Credential Validation' is set to 'Success and Failure'
✓ Pass: Platform is not end-of-life
! Error: Ensure 'Setup: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
! Error: Ensure 'Network security: Allow Local System to use computer identity for NTLM' is set to 'Enabled'
! Error: Ensure 'Network security: Configure encryption types allowed for Kerberos' is set to 'AES128_HMAC_SHA1, AES256_HMAC_SHA1, Futu
re encryption types'
✓ Pass: Ensure 'Maximum password age' is set to '365 or fewer days, but not 0'
✕ Fail: Ensure no known platform advisories exist
! Error: Ensure 'Do not delete temp folders upon exit' is set to 'Disabled'
! Error: Ensure 'Always prompt for password upon connection' is set to 'Enabled'
! Error: Ensure 'Network access: Restrict clients allowed to make remote calls to SAM' is set to 'Administrators: Remote Access: Allow'
✓ Pass: Ensure 'Audit: Shut down system immediately if unable to log security audits' is set to 'Disabled'
! Error: Ensure 'Require use of specific security layer for remote (RDP) connections' is set to 'Enabled: SSL'
✓ Pass: Ensure 'Network access: Sharing and security model for local accounts' is set to 'Classic - local users authenticate as themselves'
✕ Fail: Ensure 'Minimum password length' is set to '14 or more character(s)'
✕ Fail: Ensure 'Network access: Named Pipes that can be accessed anonymously' is set to 'None'
✓ Pass: Ensure 'Audit Security State Change' is set to include 'Success'
✓ Pass: Ensure 'Audit Security Group Management' is set to include 'Success'
! Error: Ensure 'Security: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✓ Pass: Ensure 'Audit Audit Policy Change' is set to include 'Success'
✕ Fail: Ensure 'Audit Authorization Policy Change' is set to include 'Success'
✓ Pass: Ensure 'Network security: Do not store LAN Manager hash value on next password change' is set to 'Enabled'
✕ Fail: Ensure 'Audit User Account Management' is set to 'Success and Failure'
! Error: Ensure 'Network Security: Allow PKU2U authentication requests to this computer to use online identities' is set to 'Disabled'
! Error: Ensure 'NetBT NodeType configuration' is set to 'Enabled: P-node (recommended)'
✓ Pass: Ensure 'Network access: Let Everyone permissions apply to anonymous users' is set to 'Disabled'
! Error: Ensure 'WDigest Authentication' is set to 'Disabled'
! Error: Ensure 'Application: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
! Error: Ensure 'Network access: Shares that can be accessed anonymously' is set to 'None'
✕ Fail: Ensure 'Configure SMB v1 client driver' is set to 'Enabled: Disable driver (recommended)'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) clients' is set to 'Require NTLMv
2 session security, Require 128-bit encryption'
! Error: Ensure 'Do not allow supported Plug and Play device redirection' is set to 'Enabled'
✕ Fail: Ensure the platform is not End-of-Life
✓ Pass: Ensure 'Network security: LDAP client signing requirements' is set to 'Negotiate signing' or higher
✕ Fail: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts and shares' is set to 'Enabled'
✓ Pass: Ensure 'Network access: Allow anonymous SID/Name translation' is set to 'Disabled'
! Error: Ensure 'Set time limit for disconnected sessions' is set to 'Enabled: 1 minute'
! Error: Ensure 'Application: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
! Error: Ensure 'Set time limit for active but idle Remote Desktop Services sessions' is set to 'Enabled: 15 minutes or less, but not Never (0)'
! Error: Ensure 'Network security: LAN Manager authentication level' is set to 'Send NTLMv2 response only. Refuse LM&NTLM'
! Error: Ensure 'Do not allow drive redirection' is set to 'Enabled'
✕ Fail: Ensure 'Audit Sensitive Privilege Use' is set to 'Success and Failure'
! Error: Ensure 'Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings' is set to 'Enabled'
✕ Fail: secpol.privilegerights['SeDebugPrivilege'].length == null
✕ Fail: Ensure 'Audit Security System Extension' is set to include 'Success'
✕ Fail: Ensure 'Audit Other Policy Change Events' is set to include 'Failure'
! Error: Ensure 'Do not allow COM port redirection' is set to 'Enabled'
✕ Fail: Ensure 'Minimum password age' is set to '1 or more day(s)'
! Error: Ensure 'Setup: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
! Error: Ensure 'Set client connection encryption level' is set to 'Enabled: High Level'
✓ Pass: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts' is set to 'Enabled'
! Error: Ensure 'System: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
! Error: Ensure 'Network security: Allow LocalSystem NULL session fallback' is set to 'Disabled'
✕ Fail: Ensure 'Audit Group Membership' is set to include 'Success'
✓ Pass: Ensure 'Audit Logon' is set to 'Success and Failure'
! Error: Ensure 'Turn off multicast name resolution' is set to 'Enabled'
! Error: Ensure 'Relax minimum password length limits' is set to 'Enabled'
! Error: Ensure 'System: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✕ Fail: Ensure 'Audit MPSSVC Rule-Level Policy Change' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Other Object Access Events' is set to 'Success and Failure'
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 7.2 KB5007192 14393/4583 14393/4770 KB5007192
■ 7.5 KB5008207 14393/4583 14393/4825 KB5008207
■ 10 KB5009546 14393/4583 14393/4886 KB5009546
Overall CVSS score: 10.0
Summary
========================
Target: win2016
Score: C 34/100 (100% completed)
✓ Passed: ████ 25% (22)
✕ Failed: █████ 36% (32)
! Errors: ██████ 39% (35)
» Skipped: 0% (0)
Policies:
F 0 Platform Vulnerability Policy by Mondoo
C 42 Windows Security Baseline by Mondoo
B 60 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/23xDLIBGcBhR04w8iLEJNOZR5tF?spaceId=relaxed-poincare-384428
Option 3: Scan a Windows system remote via ssh transporter
1. Install and register Mondoo Client on your host system running the vagrant Windows 2016 system.
2. Run the following command:
atomic111:..vagrant-test-boxen ∅> mondoo scan ssh
vagrant@192.168.56.252 -p 'vagrant'
→ Mondoo 6.8.0 (Space: "//captain.api.mondoo.app/spaces/relaxed-poincare-384428", Service Account: "21jsOJLO853ISdwRv2KyhG3VGHu", Manag
ed Client: "21jrdvKi4dnW95pVsvoH3zfEFQU")
→ loaded configuration from /home/user/.config/mondoo/mondoo.yml using source default
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=1
→ establish connection to asset WIN-UO68HGC3S3I (unknown)
███████████████████████████████████████████████████████████████████████████ 100% WIN-UO68HGC3S3I
→ send all results asset=WIN-UO68HGC3S3I
→ scan took 1m55.625912032s
Data queries:
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "KB5009546"
Mrn: "//vadvisor.api.mondoo.app/advisories/KB5009546"
cves: [
0: {
ID: "CVE-2022-21913"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2022-21913"
cvss: [
... 1979 more lines ...
platform.eol.date: 2022-11-11 01:00:00 +0100 CET
Controls:
✕ Fail: Ensure 'Audit Credential Validation' is set to 'Success and Failure'
! Error: Ensure 'Network access: Restrict clients allowed to make remote calls to SAM' is set to 'Administrators: Remote Access: Allow'
✕ Fail: Ensure 'Audit IPsec Driver' is set to 'Success and Failure'
✕ Fail: Ensure no known platform advisories exist
✓ Pass: Ensure 'Network security: Do not store LAN Manager hash value on next password change' is set to 'Enabled'
✓ Pass: Ensure 'Audit Audit Policy Change' is set to include 'Success'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) clients' is set to 'Require NTLMv
2 session security, Require 128-bit encryption'
✕ Fail: Ensure 'Audit Sensitive Privilege Use' is set to 'Success and Failure'
! Error: Ensure 'Set client connection encryption level' is set to 'Enabled: High Level'
! Error: Ensure 'WDigest Authentication' is set to 'Disabled'
! Error: Ensure 'Security: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
! Error: Ensure 'Do not allow LPT port redirection' is set to 'Enabled'
✓ Pass: Ensure 'Network access: Allow anonymous SID/Name translation' is set to 'Disabled'
✕ Fail: Ensure 'Audit Other Object Access Events' is set to 'Success and Failure'
✓ Pass: Ensure 'Network access: Sharing and security model for local accounts' is set to 'Classic - local users authenticate as themselves'
! Error: Ensure 'Do not delete temp folders upon exit' is set to 'Disabled'
! Error: Ensure 'Set time limit for disconnected sessions' is set to 'Enabled: 1 minute'
✕ Fail: Ensure 'Audit Other Logon/Logoff Events' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Group Membership' is set to include 'Success'
! Error: Ensure 'Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings' is set to 'Enabled'
! Error: Ensure 'Require secure RPC communication' is set to 'Enabled'
! Error: Ensure 'Application: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
! Error: Ensure 'Security: Specify the maximum log file size (KB)' is set to 'Enabled: 196,608 or greater'
✕ Fail: Ensure the platform is not End-of-Life
✓ Pass: Ensure 'Audit Security Group Management' is set to include 'Success'
✕ Fail: Ensure 'Audit Security System Extension' is set to include 'Success'
✓ Pass: Ensure 'Audit Special Logon' is set to include 'Success'
! Error: Ensure 'System: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
✕ Fail: Ensure 'Audit Removable Storage' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit MPSSVC Rule-Level Policy Change' is set to 'Success and Failure'
✕ Fail: secpol.privilegerights['SeDebugPrivilege'].length == null
! Error: Ensure 'Network Security: Allow PKU2U authentication requests to this computer to use online identities' is set to 'Disabled'
✓ Pass: Ensure 'Network security: LDAP client signing requirements' is set to 'Negotiate signing' or higher
✕ Fail: Ensure 'Audit Detailed File Share' is set to include 'Failure'
! Error: Ensure 'Allow users to connect remotely by using Remote Desktop Services' is set to 'Disabled'
✕ Fail: Ensure no known platform CVEs exist
✓ Pass: Ensure 'Password must meet complexity requirements' is set to 'Enabled'
✓ Pass: Ensure 'Audit System Integrity' is set to 'Success and Failure'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) servers' is set to 'Require NTLMv
2 session security, Require 128-bit encryption'
✓ Pass: Ensure 'Audit Logon' is set to 'Success and Failure'
! Error: Ensure 'Network security: Configure encryption types allowed for Kerberos' is set to 'AES128_HMAC_SHA1, AES256_HMAC_SHA1, Future encryption types'
✓ Pass: Ensure 'Audit: Shut down system immediately if unable to log security audits' is set to 'Disabled'
! Error: Ensure 'Network security: Allow LocalSystem NULL session fallback' is set to 'Disabled'
✓ Pass: Ensure 'Store passwords using reversible encryption' is set to 'Disabled'
✓ Pass: Ensure 'Network access: Restrict anonymous access to Named Pipes and Shares' is set to 'Enabled'
! Error: Ensure 'Require use of specific security layer for remote (RDP) connections' is set to 'Enabled: SSL'
✓ Pass: Ensure 'Network access: Let Everyone permissions apply to anonymous users' is set to 'Disabled'
! Error: Ensure 'NetBT NodeType configuration' is set to 'Enabled: P-node (recommended)'
! Error: Ensure 'Network security: Allow Local System to use computer identity for NTLM' is set to 'Enabled'
✓ Pass: Ensure 'Maximum password age' is set to '365 or fewer days, but not 0'
✕ Fail: Ensure 'Audit Account Lockout' is set to include 'Failure'
✕ Fail: Ensure 'Audit Authorization Policy Change' is set to include 'Success'
! Error: Ensure 'Require user authentication for remote connections by using Network Level Authentication' is set to 'Enabled'
✕ Fail: Ensure 'Audit File Share' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit PNP Activity' is set to include 'Success'
✕ Fail: Ensure 'Minimum password length' is set to '14 or more character(s)'
! Error: Ensure 'System: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✓ Pass: Ensure 'Audit Authentication Policy Change' is set to include 'Success'
! Error: Ensure 'Always prompt for password upon connection' is set to 'Enabled'
✓ Pass: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts' is set to 'Enabled'
✕ Fail: Ensure 'Audit Application Group Management' is set to 'Success and Failure'
! Error: Ensure 'Setup: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
! Error: Ensure 'Do not allow supported Plug and Play device redirection' is set to 'Enabled'
✕ Fail: Ensure 'Audit Other Policy Change Events' is set to include 'Failure'
! Error: Ensure 'Turn off multicast name resolution' is set to 'Enabled'
✕ Fail: Ensure 'Apply UAC restrictions to local accounts on network logons' is set to 'Enabled'
✕ Fail: Ensure 'Network access: Named Pipes that can be accessed anonymously' is set to 'None'
✕ Fail: Ensure 'Enforce password history' is set to '24 or more password(s)'
✕ Fail: Ensure 'Audit Process Creation' is set to include 'Success'
! Error: Ensure 'Set time limit for active but idle Remote Desktop Services sessions' is set to 'Enabled: 15 minutes or less, but not Never (0)'
! Error: Ensure 'Configure SMB v1 server' is set to 'Disabled'
! Error: Ensure 'Application: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
✓ Pass: Ensure 'Audit Logoff' is set to include 'Success'
✕ Fail: Ensure 'Network access: Do not allow storage of passwords and credentials for network authentication' is set to 'Enabled'
✓ Pass: Ensure 'Enable Structured Exception Handling Overwrite Protection (SEHOP)' is set to 'Enabled'
✕ Fail: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts and shares' is set to 'Enabled'
✕ Fail: Ensure 'Configure SMB v1 client driver' is set to 'Enabled: Disable driver (recommended)'
! Error: Ensure 'Network access: Shares that can be accessed anonymously' is set to 'None'
! Error: Ensure 'Do not allow COM port redirection' is set to 'Enabled'
✕ Fail: Ensure 'Audit User Account Management' is set to 'Success and Failure'
! Error: Ensure 'Do not allow drive redirection' is set to 'Enabled'
! Error: Ensure 'Do not allow passwords to be saved' is set to 'Enabled'
! Error: Ensure 'Relax minimum password length limits' is set to 'Enabled'
✓ Pass: Ensure 'Audit Security State Change' is set to include 'Success'
✓ Pass: Platform is not end-of-life
! Error: Ensure 'Network security: LAN Manager authentication level' is set to 'Send NTLMv2 response only. Refuse LM&NTLM'
✓ Pass: Ensure 'Audit Other System Events' is set to 'Success and Failure'
✕ Fail: Ensure 'Minimum password age' is set to '1 or more day(s)'
! Error: Ensure 'Setup: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 7.2 KB5007192 14393/4583 14393/4770 KB5007192
■ 7.5 KB5008207 14393/4583 14393/4825 KB5008207
■ 10 KB5009546 14393/4583 14393/4886 KB5009546
Overall CVSS score: 10.0
Summary
========================
Target: WIN-UO68HGC3S3I
Score: C 34/100 (100% completed)
✓ Passed: ████ 25% (22)
✕ Failed: █████ 36% (32)
! Errors: ██████ 39% (35)
» Skipped: 0% (0)
Policies:
F 0 Platform Vulnerability Policy by Mondoo
C 42 Windows Security Baseline by Mondoo
B 60 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/23xDLIBGcBhR04w8iLEJNOZR5tF?spaceId=relaxed-poincare-384428
Scan other operating systems
You can also scan the Windows 2019/2022 and Windows 10/11 systems I set up for this article. Use the installed Mondoo Client, ssh transporter, or vagrant transporter.
Scan via vagrant transporter:
mondoo scan vagrant win 10
mondoo scan vagrant win2019
mondoo scan vagrant win2022
Scan via ssh transporter:
mondoo scan ssh vagrant@192.168.56.249 -p 'vagrant'
mondoo scan ssh vagrant@192.168.56.230 -p 'vagrant'
mondoo scan ssh vagrant@192.168.56.236 -p 'vagrant'
Don’t limit yourself to scanning the machines I set up for this exercise! You can follow the same steps to scan your own infrastructure.
Mondoo’s full-stack security solution identifies vulnerabilities and provides steps to fix the problems. Keep scanning and discover how you can harden your systems. If you have questions, we’d love to help.