The Center for Internet Security (CIS) recently released an updated 2.0 version of their workstation and server benchmarks for Windows 10, 11, 2016, 2019, and 2022. These new releases come with significant changes, including new security recommendations and the removal of outdated practices.
About the Center for Internet Security (CIS)
CIS is a nonprofit that develops IT system benchmarks to enhance cybersecurity readiness. Collaborating with various stakeholders, CIS continuously updates its benchmarks to respond to evolving security threats.
Windows CIS Benchmarks 2.0: The Changes
CIS benchmark updates typically include improvements to detection and remediation documentation, plus a few new security recommendations. However, the new 2.0 release broke tradition by introducing a whopping 35 new recommendations and removing two outdated ones.
Out with the old
The following previous recommendations have been scrapped::
18.5.4 Ensure 'Configure DNS over HTTPS (DoH) name resolution' is set to 'Enabled: Allow DoH'
This recommendation was added to all Windows CIS Benchmarks in 2022, but it was later determined that this feature could only be applied to Windows 11/2022, so it’s been removed from the Windows 10/2016/2019 benchmarks.
2.3.1 Ensure 'Accounts: Administrator account status' is set to 'Disabled'
If you've been administering Windows systems for a while, you might recognize this as one of the original security recommendations for Windows servers. In fact, it has been recommended for longer than the existence of the Center for Internet Security. However, times have changed and now it is suggested to configure the locking out of administrative accounts on authentication failures, rather than removing the account altogether.
In with the new
With 35 new security recommendations, there are too many to cover each in detail, but there are a few important changes in this list.
18.4 (L1) Ensure 'LSA Protection' is set to 'Enabled' (10/2016/2019)
Local Security Authority in Windows sits at the heart of local and remote user authentication in Windows and enabling LSA protection provides a critical layer of security against remote code injections against the LSA process.
Workstation Workstation Workstation
Perhaps the most impressive aspect of these new CIS benchmarks is the increased focus on securing Windows workstations. With the shift towards remote work as the new norm, it is more important than ever to secure employee workstations. The addition of 32 new workstation-only recommendations in these new benchmarks provides organizations with the security recommendations they need to keep these systems secure.
New Workstation and Server Recommendations
- 1.2 (L1) Ensure 'Allow Administrator account lockout' is set to 'Enabled' (10/11/2016/2019/2022)
- 18.4 (L1) Ensure 'LSA Protection' is set to 'Enabled' (10/2016/2019)
- 18.4 (L1) Ensure 'Configure RPC packet level privacy setting for incoming connections' is set to 'Enabled' (10/11/2016/2019/2022)
- 18.6.4 (L1) Ensure 'Configure NetBIOS settings' is set to 'Enabled: Disable NetBIOS name resolution on public networks' (10/11/2016/2019/2022)
- 18.7 (L1) Ensure 'Configure RPC over TCP port' is set to 'Enabled: 0' (10/11/2016/2019/2022)
- 18.7 (L1) Ensure 'Manage processing of Queue-specific files' is set to 'Enabled: Limit Queue-specific files to Color profiles' (10/11/2016/2019/2022)
- 18.7 (L1) Ensure 'Configure RPC listener settings: Authentication protocol to use for incoming RPC connections' is set to 'Enabled: Negotiate' or higher (10/11/2016/2019/2022)
- 18.7 (L1) Ensure 'Configure RPC listener settings: Protocols to allow for incoming RPC connections' is set to 'Enabled: RPC over TCP' (10/11/2016/2019/2022)
- 18.7 (L1) Ensure 'Configure RPC connection settings: Use authentication for outgoing RPC connections' is set to 'Enabled: Default' (10/11/2016/2019/2022)
- 18.7 (L1) Ensure 'Configure RPC connection settings: Protocol to use for outgoing RPC connections' is set to 'Enabled: RPC over TCP' (10/11/2016/2019/2022)
- 18.7 (L1) Ensure 'Configure Redirection Guard' is set to 'Enabled: Redirection Guard Enabled (10/11/2016/2019/2022)
- 18.9.25 (NG) Ensure 'Configures LSASS to run as a protected process' is set to 'Enabled: Enabled with UEFI Lock' (10/2022)
- 18.9.25 (L1) Ensure 'Allow Custom SSPs and APs to be loaded into LSASS' is set to 'Disabled' (10/11/2022)
- 18.10.17 (L1) Ensure 'Enable App Installer ms-appinstaller protocol' is set to 'Disabled' (10/11/2019/2022)
- 18.10.17 (L1) Ensure 'Enable App Installer Hash Override' is set to 'Disabled' (10/11/2019/2022)
- 18.10.17 (L1) Ensure 'Enable App Installer Experimental Features' is set to 'Disabled' (10/11/2019)
- 18.10.17 (L1) Ensure 'Enable App Installer' is set to 'Disabled' (10/11/2019/2022)
- 18.10.82 (L1) Ensure 'Enable MPR notifications for the system' is set to 'Disabled' (10/11/2022)
- 18.10.57.3.3 (L2) Ensure 'Do not allow WebAuthn redirection' is set to 'Enabled (10/11/2022)
- 18.10.59 (L2) Ensure 'Allow search highlights' is set to 'Disabled' (10/11/2016/2019/2022)
New Server only recommendations:
- 18.9.13 (L2) Ensure 'Turn off cloud optimized content' is set to 'Enabled' (2022)
- 18.9.47.5.1 'Configure Attack Surface Reduction rules' is set to 'Enable' (2016)
New Workstation only recommendations:
- 18.9.5 (L1) Ensure 'Turn On Virtualization Based Security: Kernel-mode Hardware-enforced Stack Protection' is set to 'Enabled: Enabled in enforcement Mode' (11)
- 18.9.25 (L1) Ensure 'Configures LSASS to run as a protected process' is set to 'Enabled: Enabled with UEFI Lock' (11)
- 18.9.39 (L1) 'Disable Internet Explorer 11 as a standalone browser' is set to 'Enabled: Always (10)
- 18.9.50.1 (L2) Ensure 'Enable Windows NTP Client' is set to 'Enabled' (10/11)
- 18.9.50.1 (L2) Ensure 'Enable Windows NTP Server' is set to 'Disabled' (10/11)
- 18.10.29 (L2) Ensure 'Turn off files from Office.com in Quick access view' is set to 'Enabled' (11)
- 18.10.57.2 (L2) Ensure 'Disable Cloud Clipboard integration for server-to-client data transfer' is set to 'Enabled' (11)
- 18.10.76.1 (L1) Ensure 'Notify Malicious' is set to 'Enabled' (11)
- 18.10.76.1 (L1) Ensure 'Notify Password Reuse' is set to 'Enabled' (11)
- 18.10.76.1 (L1) Ensure 'Notify Unsafe App' is set to 'Enabled' (11)
- 18.10.76.1 (L1) Ensure 'Service Enabled' is set to 'Enabled' (11)
- 18.10.79 (L1) Ensure 'Enable ESS with Supported Peripherals' is set to 'Enabled: 1’ (11)
Secure your Windows systems with Mondoo
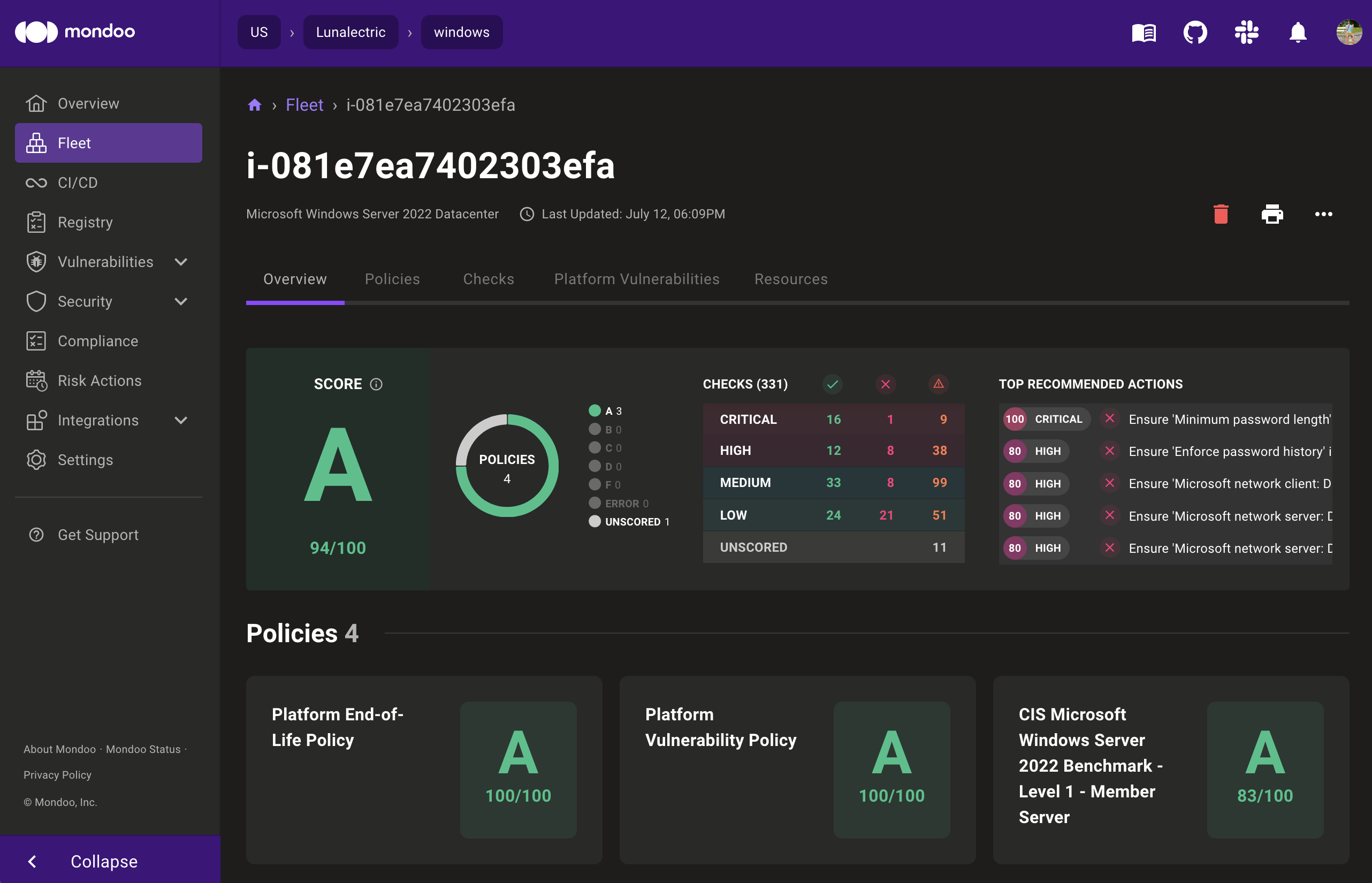
Staying compliant and secure in the face of changing benchmarks is a challenge. That's where Mondoo comes in. We offer comprehensive protection for your tech stack, helping you identify high-risk vulnerabilities and providing actionable solutions. Mondoo integrates with your applications from development to deployment, ensuring robust defense. We stay abreast of the latest CIS benchmarks, and our platform is updated accordingly to help your organization stay secure and compliant.
Ready to Enhance Your Security with Mondoo?
Don't let your infrastructure be an easy target. Get started with Mondoo for free today. Within minutes, scan your systems, identify vulnerabilities, and spot risky misconfigurations.



