What is patch management?
Patch management is the process of distributing and applying updates to software, such as operating systems (OS), platforms, and applications. It involves identifying out-dated software within your infrastructure, applying patches to that software, and validating the installation of those patches. These patches are often necessary to fix errors in the software, which are often referred to as vulnerabilities or bugs.
Why is patch management important?
Patch management is important for three main reasons:
- Security: Patch management fixes vulnerabilities in your software (OS, platform, application) that are susceptible to exploitation. It helps your organization to reduce the risk of cyberattacks.
- Compliance: Organizations are often required by regulators to follow strict guidelines because of the constant increase in cyberattacks. Patch management is a necessary part of complying to certain standards, such as PCI-DSS, HIPAA, SOC2, ISO27001, or BSI.
- System uptime: Patch management ensures your software is kept up-to-date and running smoothly without errors causing system downtime.
Finding missing patches with Mondoo
As a part of its full-stack security solution, Mondoo identifies what important patches are missing from your systems. For this blog post, I set up some vagrant Linux machines with out-of-date operating systems. I’ll use them to walk through some different ways that Mondoo shows you the patches needed.
Prerequisite: Please create a free account on console.mondoo.com.
Find missing patches using Mondoo Client
Install and register Mondoo Client on Linux or Windows systems. Also, you can use the Mondoo VMware appliance. For this blog post, I will use the Mondoo VMware appliance.
1. Follow our documentation to deploy the Mondoo VMware appliance.2. Register Mondoo Client:
a. Log into your account at console.mondo.com.
b. Go to the INTEGRATIONS page, scroll to Cloud Security, and select VMware.
-2.png?width=1561&height=1600&name=unnamed%20(1)-2.png)
c. Find the Install Mondoo Client box. Copy the CLI commands Mondoo provides and paste them into the shell of the Mondoo VMware appliances.
mondoo@debian:~$ mondoo status
→ loaded configuration from /etc/opt/mondoo/mondoo.yml using source --config
→ Hostname: debian
→ IP: 192.168.5.48
→ Platform: debian
→ Release: 11.4
→ Time: 2022-08-04T13:56:57Z
→ Version: 6.9.0 (API Version: 6)
→ API ConnectionConfig: https://us.api.mondoo.com
→ API Status: SERVING
→ API Time: 2022-08-04T13:56:57Z
→ API Version: 6
→ Space: //captain.api.mondoo.app/spaces/infallible-brahmagupta-442759
→ Client: //agents.api.mondoo.app/spaces/infallible-brahmagupta-442759/agents/2Ct7sWRmFeamn9ybVS8LuoByZxW
→ Service Account: //agents.api.mondoo.app/spaces/infallible-brahmagupta-442759/serviceaccounts/2CtUXNVs80izzkbjcr7crgqXKlL
→ client is registered
→ client authenticated successfully
d. Quickly verify that the following policies are enabled for your space:
- Platform End-of-Life Policy by Mondoo
- Platform Vulnerability Policy by Mondoo
Your POLICY HUB should look like this:
3. Run the Mondoo scan
a. Scan a single ESXi host:
In the shell of the Mondoo VMware appliance, type:
mondoo scan vsphere root@<esxi ip> --ask-pass --discover host-machines
Mondoo Client connects to Mondoo Platform and downloads the enabled policies. After the scan, Mondoo Client reports results back to Mondoo Platform.
mondoo@debian:~$ mondoo scan vsphere root@192.168.5.21 --ask-pass --discover host-machines
Enter password:
→ Mondoo 6.9.0+7514 (Space: "//captain.api.mondoo.app/spaces/infallible-brahmagupta-442759", Service Account: "2CtUXNVs80izzkbjcr7crgqX
KlL", Managed Client: "2Ct7sWRmFeamn9ybVS8LuoByZxW")
→ loaded configuration from /etc/opt/mondoo/mondoo.yml using source --config
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=2
→ establish connection to asset 192.168.5.21 (VMware ESXi) (api)
███████████████████████████████████████████████████████████████████████████ 100% 192.168.5.21 (VMware ESXi)
→ send all results asset="192.168.5.21 (VMware ESXi)"
→ establish connection to asset localhost.localdomain (baremetal)
███████████████████████████████████████████████████████████████████████████ 100% localhost.localdomain
→ send all results asset=localhost.localdomain
→ scan took 4.568075867s
Data queries:
platform.eol.date: 2025-04-02 00:00:00 +0000 UTC
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
mondoo.version: "6.9.0+7514"
platform.vulnerabilityReport: {
platform: {
build: "19035710"
name: "vmware-vsphere"
release: "7.0.3"
title: "VMware ESXi 7.0.3 build-19035710, vSphere"
}
published: "2022-08-05T10:39:24Z"
stats: {
advisories: {}
... 5 more lines ...
vsphere.about[fullName]: "VMware ESXi 7.0.3 build-19035710"
platform.release: "7.0.3"
vsphere.about[osType]: "vmnix-x86"
platform.title: "VMware ESXi 7.0.3 build-19035710, vSphere"
platform.arch: ""
Controls:
✓ Pass: Ensure the platform is not End-of-Life
✓ Pass: Ensure no known platform CVEs exist
✓ Pass: Ensure no known platform advisories exist
✓ Pass: Platform is not end-of-life
Data queries:
esxi.host.properties[summary][config][product][osType]: "vmnix-x86"
platform.title: "VMware ESXi, vSphere Host"
platform.eol.date: 2025-04-02 00:00:00 +0000 UTC
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "VMSA-2022-0004"
Mrn: "//vadvisor.api.mondoo.app/advisories/VMSA-2022-0004"
cves: [
0: {
ID: "CVE-2021-22042"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2021-22042"
cvss: [
... 326 more lines ...
esxi.host.properties[hardware][systemInfo][uuid]: "fe664d56-f513-9098-0e12-4e5ffce68410"
platform.arch: ""
esxi.host.properties[hardware][biosInfo][biosVersion]: "VMW71.00V.18452719.B64.2108091906"
esxi.host.properties[summary][config][product][fullName]: "VMware ESXi 7.0.3 build-19035710"
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
mondoo.version: "6.9.0+7514"
platform.release: "7.0.3"
esxi.host.name: "localhost.localdomain"
Controls:
✕ Fail: Ensure no known platform advisories exist
✓ Pass: Ensure the platform is not End-of-Life
✕ Fail: Ensure no known platform CVEs exist
✓ Pass: Platform is not end-of-life
Vulnerabilities:
■ No advisories found (passed)
Overall CVSS score: 0.0
Summary
========================
Target: 192.168.5.21 (VMware ESXi)
Score: A 100/100 (100% completed)
✓ Passed: ███████████████ 100% (4)
✕ Failed: 0% (0)
! Errors: 0% (0)
» Skipped: 0% (0)
Policies:
. .. Platform Overview Information by Mondoo
A 100 Platform End-of-Life Policy by Mondoo
A 100 Platform Vulnerability Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2CvvR5ddjYP4pPWu1BbuPCy0vYW?spaceId=infallible-brahmagupta-442759
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 2.1 VMSA-2022-0016 7.0.3/19035710 7.0/19898904 ESXi70U3e-19898904 + KB88632
■ 5.6 VMSA-2022-0020 7.0.3/19035710 7.0/20036589 ESXi70U3sf-20036586
■ 6 VMSA-2022-0004 7.0.3/19035710 7.0/19193900 ESXi70U3c-19193900
■ 6.9 VMSA-2022-0001 7.0.3/19035710 7.0/19193900 ESXi70U3c-19193900
Overall CVSS score: 6.9
Summary
========================
Target: localhost.localdomain
Score: B 65/100 (100% completed)
✓ Passed: ████████ 50% (2)
✕ Failed: ████████ 50% (2)
! Errors: 0% (0)
» Skipped: 0% (0)
Policies:
. .. Platform Overview Information by Mondoo
C 31 Platform Vulnerability Policy by Mondoo
A 100 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2CvvR8OoxCLSncUlFrWHOkKulkQ?spaceId=infallible-brahmagupta-442759
b. Scan a complete VMWare cluster:
In the shell of your Mondoo VMware appliance, type:
mondoo scan vsphere <user>@vsphere.local@<vcenter ip> --ask-pass --discover host-machines
Mondoo Client connects to Mondoo Platform and downloads the enabled policies. After the scan, Mondoo Client reports results back to Mondoo Platform.
mondoo@debian:~$ mondoo scan vsphere readuser@vsphere.local@192.168.5.24 --ask-pass --discover host-machines
Enter password:
→ Mondoo 6.9.0+7514 (Space: "//captain.api.mondoo.app/spaces/infallible-brahmagupta-442759", Service Account: "2CtUXNVs80izzkbjcr7crgqX
KlL", Managed Client: "2Ct7sWRmFeamn9ybVS8LuoByZxW")
→ loaded configuration from /etc/opt/mondoo/mondoo.yml using source --config
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=4
→ establish connection to asset 192.168.5.24 (VMware vCenter Server) (api)
███████████████████████████████████████████████████████████████████████████ 100% 192.168.5.24 (VMware vCenter Server)
→ send all results asset="192.168.5.24 (VMware vCenter Server)"
→ establish connection to asset 192.168.5.21 (baremetal)
███████████████████████████████████████████████████████████████████████████ 100% 192.168.5.21
→ send all results asset=192.168.5.21
→ establish connection to asset 192.168.5.22 (baremetal)
███████████████████████████████████████████████████████████████████████████ 100% 192.168.5.22
→ send all results asset=192.168.5.22
→ establish connection to asset 192.168.5.23 (baremetal)
███████████████████████████████████████████████████████████████████████████ 100% 192.168.5.23
→ send all results asset=192.168.5.23
→ scan took 14.149945998s
Data queries:
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "VMSA-2022-0004"
Mrn: "//vadvisor.api.mondoo.app/advisories/VMSA-2022-0004"
cves: [
0: {
ID: "CVE-2021-22042"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2021-22042"
cvss: [
... 326 more lines ...
esxi.host.properties[hardware][systemInfo][uuid]: "fe664d56-f513-9098-0e12-4e5ffce68410"
platform.title: "VMware ESXi, vSphere Host"
esxi.host.properties[summary][config][product][fullName]: "VMware ESXi 7.0.3 build-19035710"
platform.eol.date: 2025-04-02 00:00:00 +0000 UTC
platform.arch: ""
platform.release: "7.0.3"
mondoo.version: "6.9.0+7514"
esxi.host.name: "192.168.5.21"
esxi.host.properties[hardware][biosInfo][biosVersion]: "VMW71.00V.18452719.B64.2108091906"
esxi.host.properties[summary][config][product][osType]: "vmnix-x86"
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
Controls:
✕ Fail: Ensure no known platform CVEs exist
✓ Pass: Platform is not end-of-life
✕ Fail: Ensure no known platform advisories exist
✓ Pass: Ensure the platform is not End-of-Life
Data queries:
platform.arch: ""
esxi.host.properties[summary][config][product][osType]: "vmnix-x86"
platform.title: "VMware ESXi, vSphere Host"
mondoo.version: "6.9.0+7514"
esxi.host.properties[summary][config][product][fullName]: "VMware ESXi 7.0.3 build-19035710"
platform.release: "7.0.3"
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
esxi.host.properties[hardware][systemInfo][uuid]: "3f9a4d56-0ab9-2d28-80a2-c806a71d3f94"
esxi.host.properties[hardware][biosInfo][biosVersion]: "VMW71.00V.18452719.B64.2108091906"
platform.eol.date: 2025-04-02 00:00:00 +0000 UTC
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "VMSA-2022-0004"
Mrn: "//vadvisor.api.mondoo.app/advisories/VMSA-2022-0004"
cves: [
0: {
ID: "CVE-2021-22042"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2021-22042"
cvss: [
... 326 more lines ...
esxi.host.name: "192.168.5.22"
Controls:
✓ Pass: Platform is not end-of-life
✓ Pass: Ensure the platform is not End-of-Life
✕ Fail: Ensure no known platform advisories exist
✕ Fail: Ensure no known platform CVEs exist
Data queries:
platform.eol.date: 2025-04-02 00:00:00 +0000 UTC
platform.arch: ""
esxi.host.name: "192.168.5.23"
platform.release: "7.0.0"
esxi.host.properties[summary][config][product][osType]: "vmnix-x86"
esxi.host.properties[summary][config][product][fullName]: "VMware ESXi 7.0.0 build-16324942"
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
mondoo.version: "6.9.0+7514"
platform.title: "VMware ESXi, vSphere Host"
esxi.host.properties[hardware][systemInfo][uuid]: "c78a4d56-1ca1-1ae0-2a95-800815777e9f"
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "VMSA-2021-0014"
Mrn: "//vadvisor.api.mondoo.app/advisories/VMSA-2021-0014"
cves: [
0: {
ID: "CVE-2021-21994"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2021-21994"
cvss: [
... 682 more lines ...
esxi.host.properties[hardware][biosInfo][biosVersion]: "VMW71.00V.18452719.B64.2108091906"
Controls:
✕ Fail: Ensure no known platform CVEs exist
✓ Pass: Platform is not end-of-life
✕ Fail: Ensure no known platform advisories exist
✓ Pass: Ensure the platform is not End-of-Life
Data queries:
platform.eol.date: 2025-04-02 00:00:00 +0000 UTC
vsphere.about[fullName]: "VMware vCenter Server 7.0.3 build-18778458"
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
vsphere.about[osType]: "linux-x64"
mondoo.version: "6.9.0+7514"
platform.vulnerabilityReport: {
platform: {
build: "18778458"
name: "vmware-vsphere"
release: "7.0.3"
title: "VMware vCenter Server 7.0.3 build-18778458, vSphere"
}
published: "2022-08-05T11:08:07Z"
stats: {
advisories: {}
... 5 more lines ...
platform.title: "VMware vCenter Server 7.0.3 build-18778458, vSphere"
platform.arch: ""
platform.release: "7.0.3"
Controls:
✓ Pass: Ensure no known platform advisories exist
✓ Pass: Ensure no known platform CVEs exist
✓ Pass: Ensure the platform is not End-of-Life
✓ Pass: Platform is not end-of-life
Vulnerabilities:
■ No advisories found (passed)
Overall CVSS score: 0.0
Summary
========================
Target: 192.168.5.24 (VMware vCenter Server)
Score: A 100/100 (100% completed)
✓ Passed: ███████████████ 100% (4)
✕ Failed: 0% (0)
! Errors: 0% (0)
» Skipped: 0% (0)
Policies:
. .. Platform Overview Information by Mondoo
A 100 Platform End-of-Life Policy by Mondoo
A 100 Platform Vulnerability Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2Cvw0bU7pSzFMsX1rLq3PKI0M3b?spaceId=infallible-brahmagupta-442759
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 2.1 VMSA-2022-0016 7.0.3/19035710 7.0/19898904 ESXi70U3e-19898904 + KB88632
■ 5.6 VMSA-2022-0020 7.0.3/19035710 7.0/20036589 ESXi70U3sf-20036586
■ 6 VMSA-2022-0004 7.0.3/19035710 7.0/19193900 ESXi70U3c-19193900
■ 6.9 VMSA-2022-0001 7.0.3/19035710 7.0/19193900 ESXi70U3c-19193900
Overall CVSS score: 6.9
Summary
========================
Target: 192.168.5.21
Score: B 65/100 (100% completed)
✓ Passed: ████████ 50% (2)
✕ Failed: ████████ 50% (2)
! Errors: 0% (0)
» Skipped: 0% (0)
Policies:
. .. Platform Overview Information by Mondoo
C 31 Platform Vulnerability Policy by Mondoo
A 100 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2Cvw0i7EiUZPaXXFfFh6U0txhQl?spaceId=infallible-brahmagupta-442759
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 2.1 VMSA-2022-0016 7.0.3/19035710 7.0/19898904 ESXi70U3e-19898904 + KB88632
■ 5.6 VMSA-2022-0020 7.0.3/19035710 7.0/20036589 ESXi70U3sf-20036586
■ 6 VMSA-2022-0004 7.0.3/19035710 7.0/19193900 ESXi70U3c-19193900
■ 6.9 VMSA-2022-0001 7.0.3/19035710 7.0/19193900 ESXi70U3c-19193900
Overall CVSS score: 6.9
Summary
========================
Target: 192.168.5.22
Score: B 65/100 (100% completed)
✓ Passed: ████████ 50% (2)
✕ Failed: ████████ 50% (2)
! Errors: 0% (0)
» Skipped: 0% (0)
Policies:
. .. Platform Overview Information by Mondoo
C 31 Platform Vulnerability Policy by Mondoo
A 100 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2Cvw0hLwesvnLenD2fXIDDsbrLf?spaceId=infallible-brahmagupta-442759
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 2.1 VMSA-2022-0016 7.0.0/16324942 7.0/19898904 ESXi70U3e-19898904 + KB88632
■ 2.1 VMSA-2020-0029 7.0.0/16324942 7.0/17325551 ESXi70U1c-17325551
■ 5.6 VMSA-2022-0020 7.0.0/16324942 7.0/20036589 ESXi70U3sf-20036586
■ 6 VMSA-2022-0004 7.0.0/16324942 7.0/19193900 ESXi70U3c-19193900
■ 6.8 VMSA-2021-0014 7.0.0/16324942 7.0/17630552 ESXi70U2-17630552
■ 6.9 VMSA-2022-0001 7.0.0/16324942 7.0/19193900 ESXi70U3c-19193900
■ 7.2 VMSA-2020-0026 7.0.0/16324942 7.0/17168206 ESXi70U1b-17168206
■ 10 VMSA-2020-0023 7.0.0/16324942 7.0/16850804 ESXi_7.0.1-0.0.16850804
■ 10 VMSA-2021-0002 7.0.0/16324942 7.0/17325551 ESXi70U1c-17325551
Overall CVSS score: 10.0
Summary
========================
Target: 192.168.5.23
Score: C 50/100 (100% completed)
✓ Passed: ████████ 50% (2)
✕ Failed: ████████ 50% (2)
! Errors: 0% (0)
» Skipped: 0% (0)
Policies:
. .. Platform Overview Information by Mondoo
F 0 Platform Vulnerability Policy by Mondoo
A 100 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2Cvw0eRPdUpmVLf4YlheNCNc1re?spaceId=infallible-brahmagupta-442759
On the Mondoo Space OVERVIEW page, you can see the VMware cluster and the top vulnerabilities within the Space.
-1.png?width=1600&height=1572&name=unnamed%20(2)-1.png)
Select FLEET and then select the Windows Asse to see Mondoo Asset OVERVIEW page of an ESXi system.
.png?width=1600&height=1571&name=unnamed%20(3).png)
Select Platform Vulnerabilities to see the Advisories and CVEs that affect the system. Mondoo shows:
- An overview of the advisories and CVEs
- How critical the vulnerability is
.png?width=1537&height=1600&name=unnamed%20(4).png)
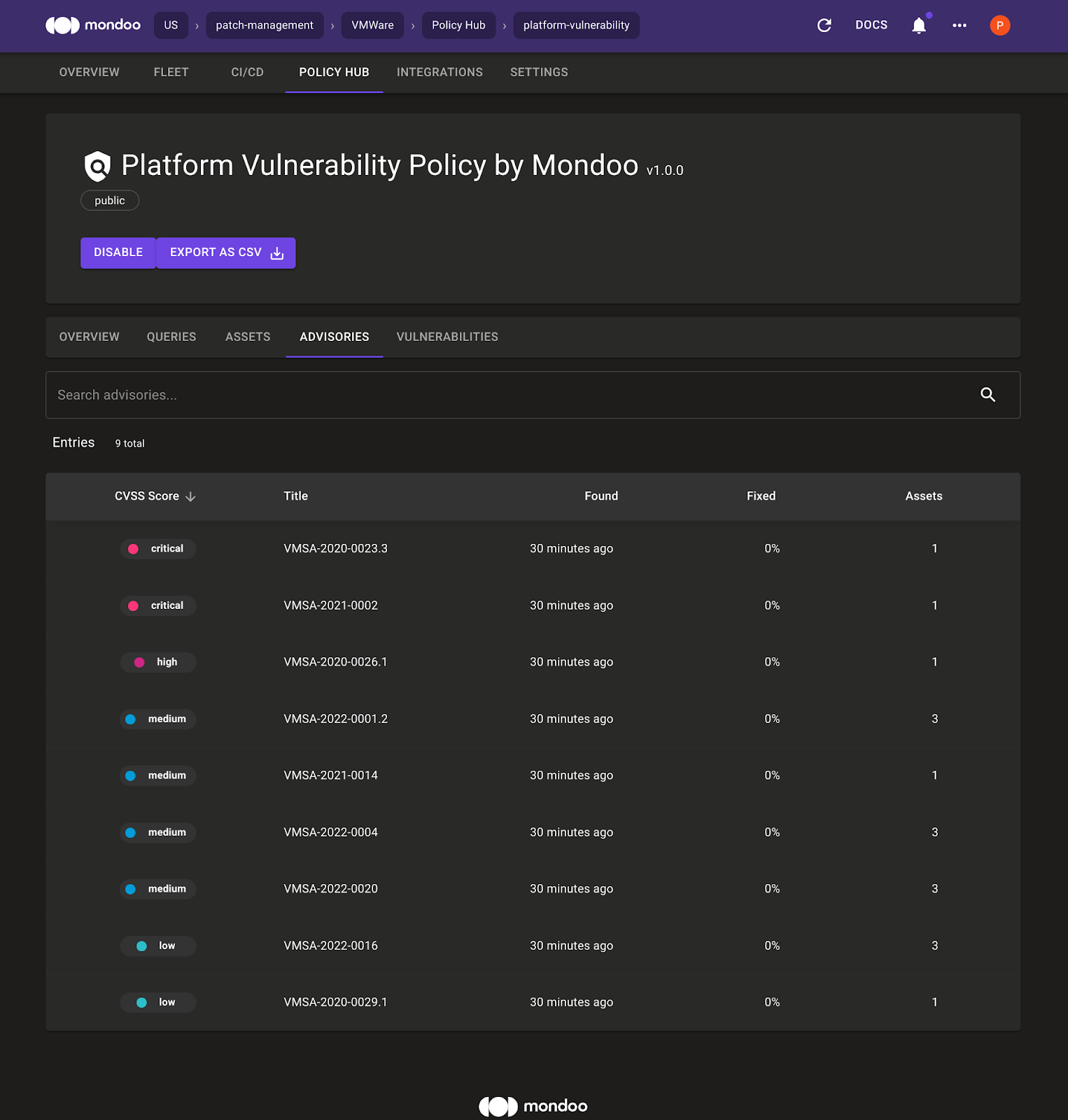
If you select POLICY HUB, Platform Vulnerability Policy by Mondoo, and Advisories, you see an overview of all advisories within the VMware’s Space. For each advisory, Mondoo shows:
- When it was found
- How many assets have it
- The fix status
You can continuously scan your VMware cluster: Follow the instructions in our documentation.
Don’t stop at scanning the machines I set up for this exercise! You can follow the same steps to scan your own infrastructure. Mondoo’s full-stack security solution identifies vulnerabilities and provides steps to fix the problems. Keep scanning and discover how you can harden your systems. If you have questions, we’d love to help.



-3.png?width=795&height=415&name=800x418%20blog%20feature%20images%20(4)-3.png)