-1.png?width=795&height=415&name=800x418%20blog%20feature%20images%20(2)-1.png)
Welcome to the September 2022 recap of Mondoo releases. We are a bit late this month, since there are some big announcements on the way!
We have a lot of exciting changes to share from our work this month as well:
Chapters:
- All New Fleet View Experience
- Explore Asset Relationships
- Top Five Recommended Actions
- View All Controls for an Asset
- Error Messages for Unavailable Assets
- Kubernetes Asset Scanning by Default
- Quickly Find Kubernetes Operator Scanned Assets
- Scan Kubernetes Resources on Add/Update
- Automatic Cleanup of Kubernetes Resources
- New Kubernetes MQL Resources
- HashiCorp Terraform GitHub Action Support
- Simplified Terraform State File Resource
- mondoo exec Is Now mondoo run
- Policy updates
- Other improvements
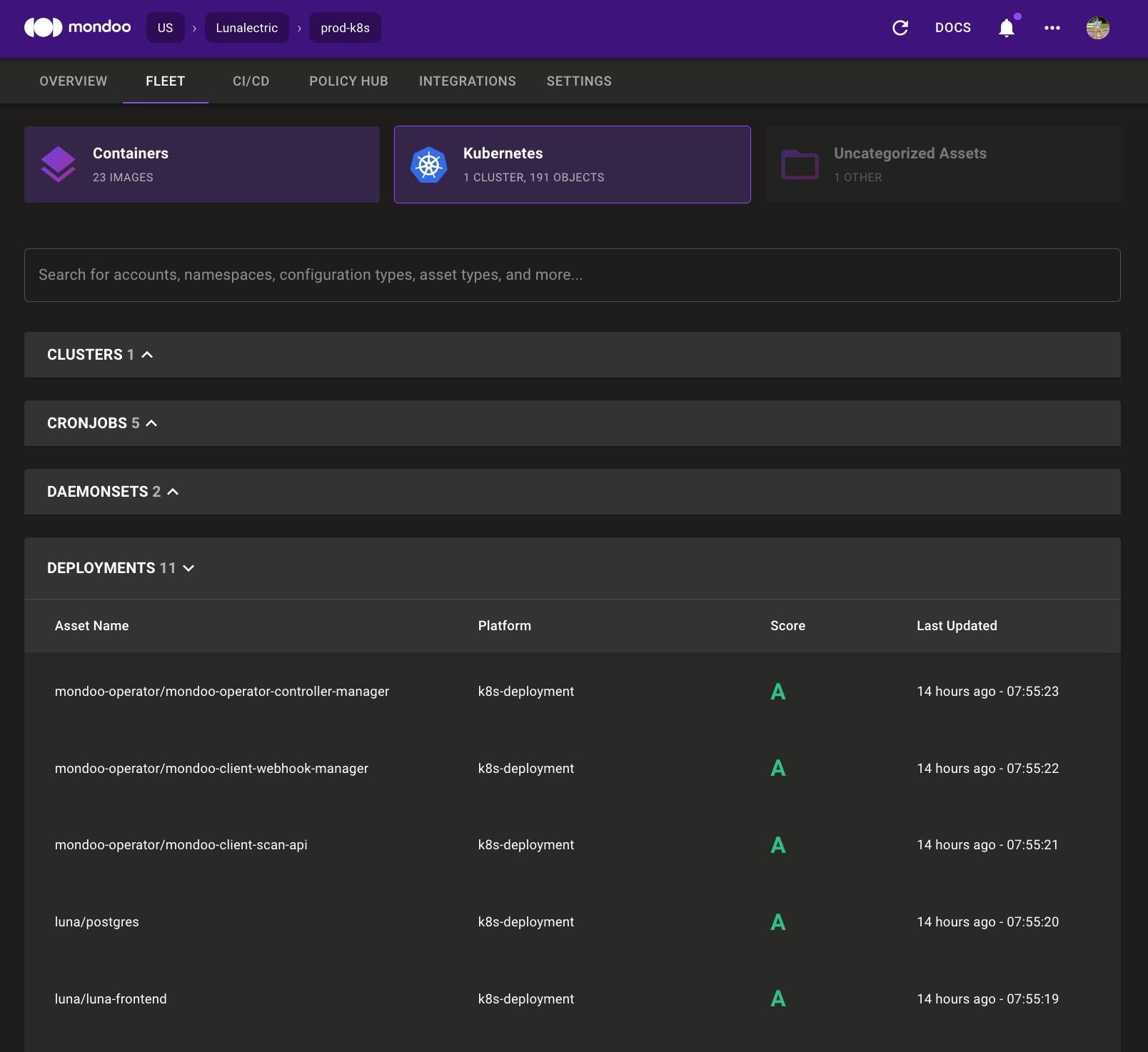
All New Fleet Experience
Problem: You have hundreds or thousands of assets in Mondoo. Finding types of systems and understanding the relationships between assets is difficult.
Solution: We added a whole new fleet view experience to Mondoo that groups your assets by type. You can quickly assess the security of different elements in your infrastructure and grasp interconnected security relationships.
Explore Asset Relationships
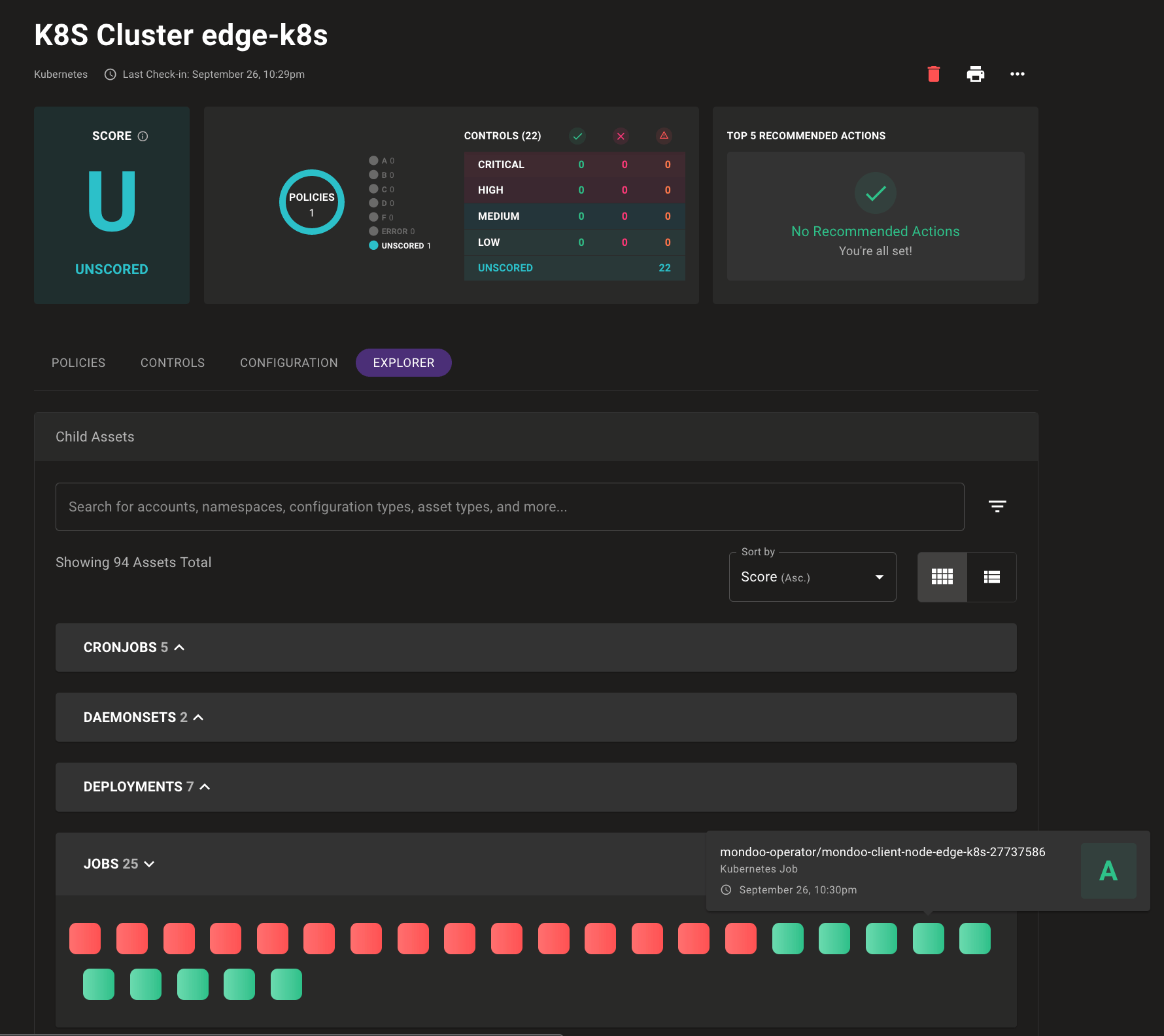
Problem: Your environment is complex, and so is the job of securing it. You want to understand not just the security of a single asset, but also how each asset relates to your overall infrastructure security.
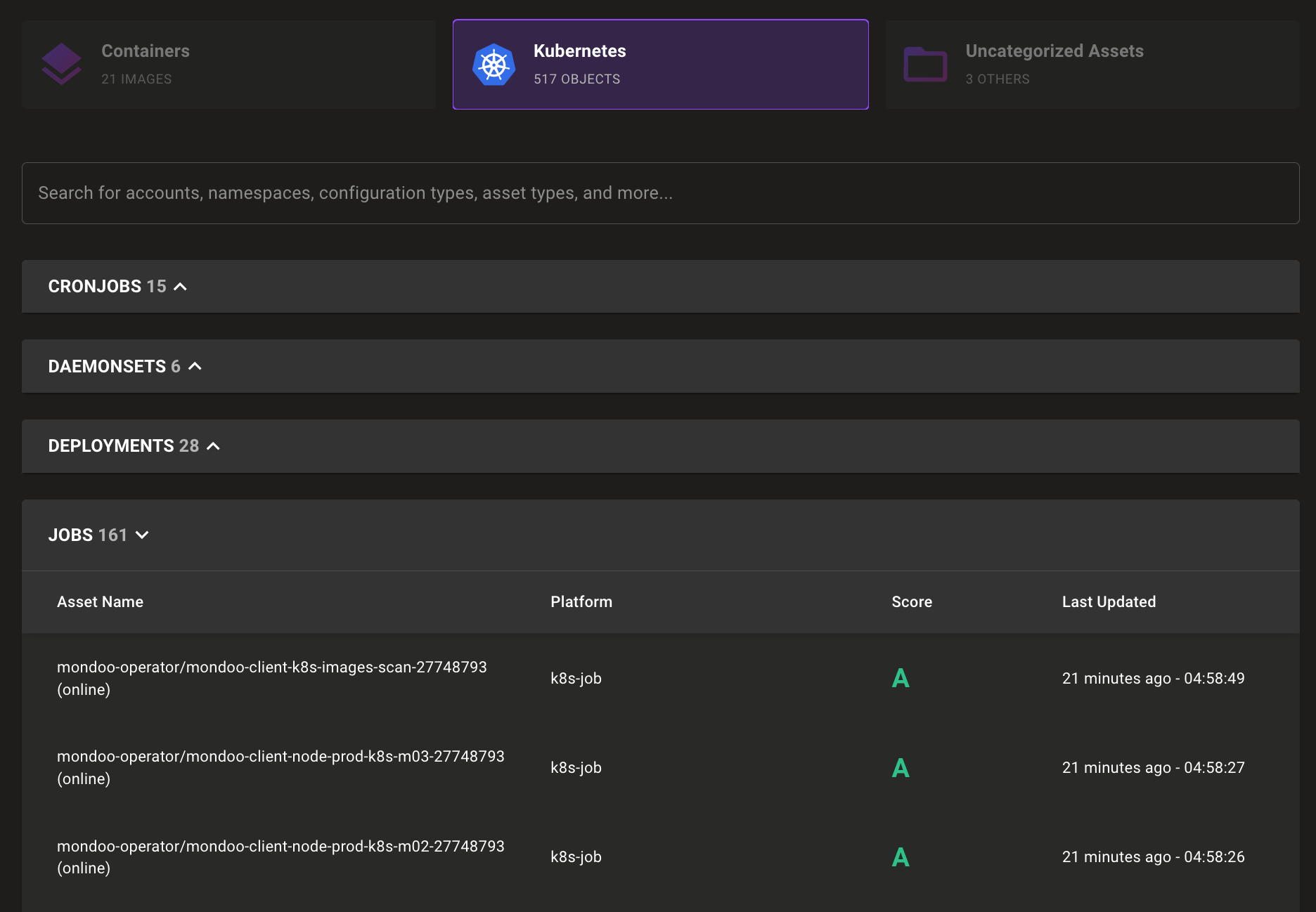
Solution: Mondoo now exposes the complex relationships that make up your infrastructure security in a new Explorer tab for each asset. The explorer view lets you quickly evaluate the security of related assets so you can better understand the security of complex infrastructure like cloud accounts or Kubernetes clusters. Each related asset is shown as a color-coded tile, which you can hover over for additional scan information. Here we see the results of Kubernetes job scans, including a Mondoo Operator job, which scored an A:
Top Five Recommended Actions
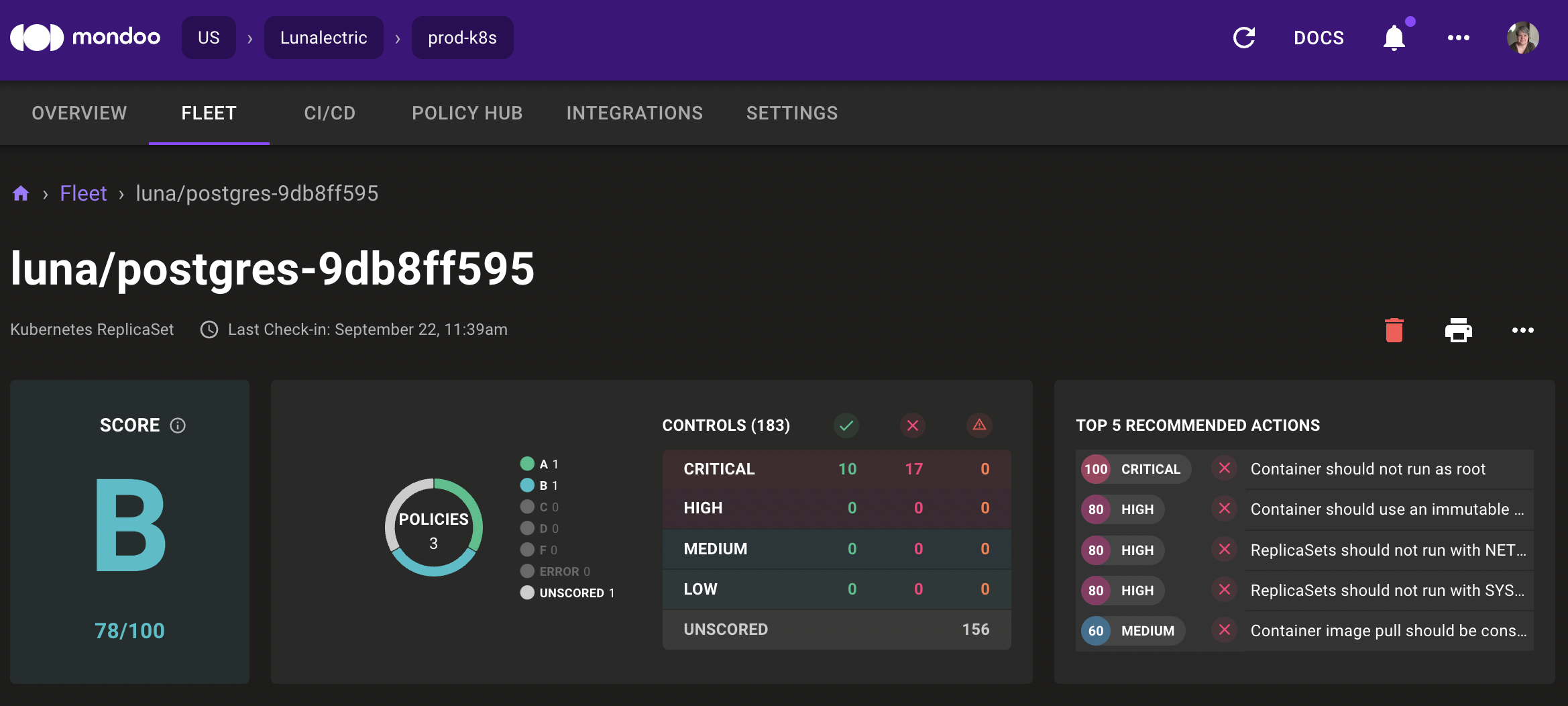
Problem: Mondoo found a lot of security issues for your asset and you're overwhelmed. It's hard to know what to fix first, without clicking through multiple screens and digging into your fleet.
Solution: The asset view now shows the five most important actions you should take to improve an asset's security.
View All Controls for an Asset
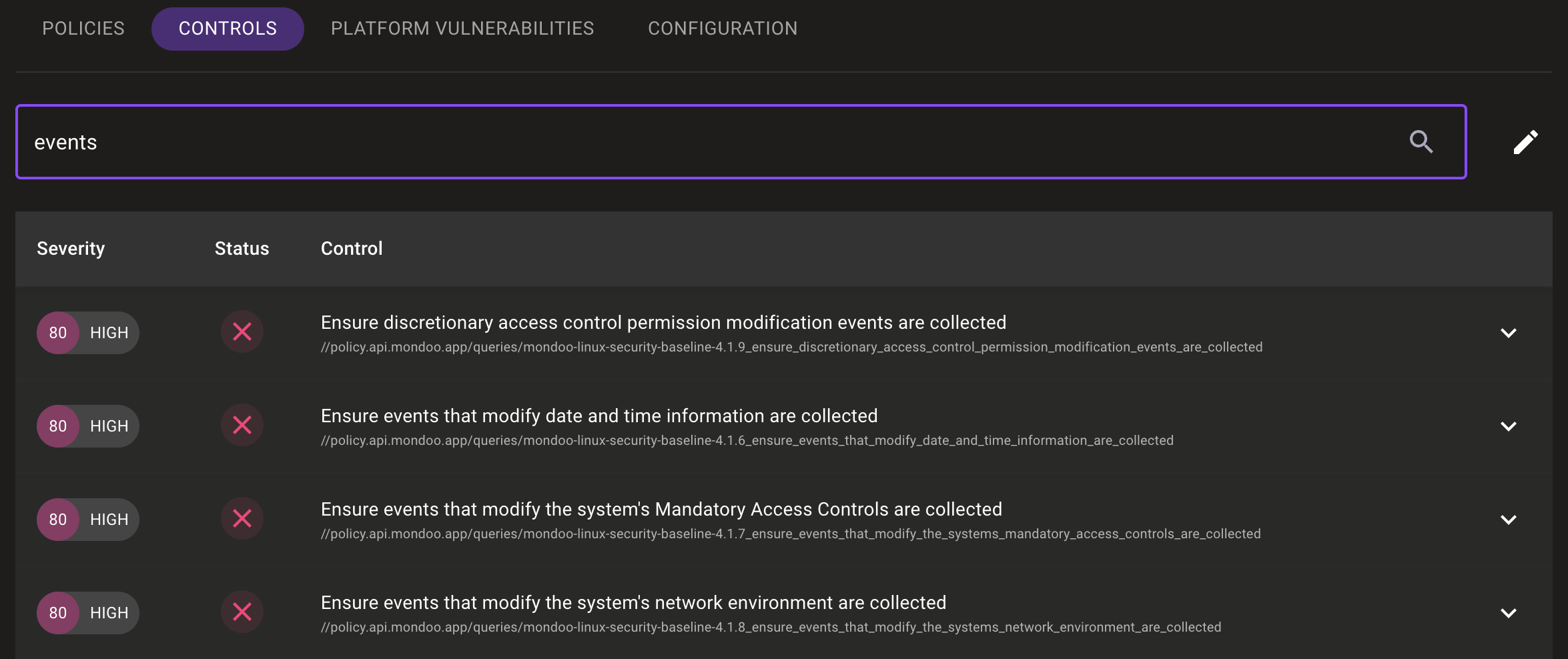
Problem: You want to find a specific control that is applied to an asset, but you don't know which policy contains it.
Solution: Mondoo now lists all of an asset's controls independently from their policies. You can filter controls by policy or by search string.
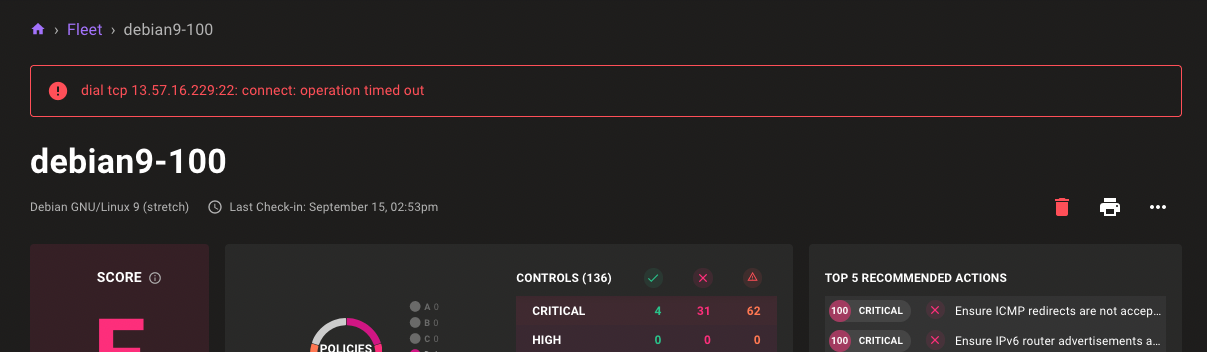
Error Messages for Unavailable Assets
Problem: It is hard to tell if Mondoo successfully connects to an asset that you view on the assets page.
Solution: Mondoo now shows an error message on the asset page when it fails to reach the asset:
Kubernetes Asset Scanning by Default
Problem: You want to scan your Kubernetes cluster and apply the Mondoo Kubernetes Security and Kubernetes Best Practices policies to all of the workloads in your cluster. But without extra flags, only the cluster shows up and the new policies don't apply.
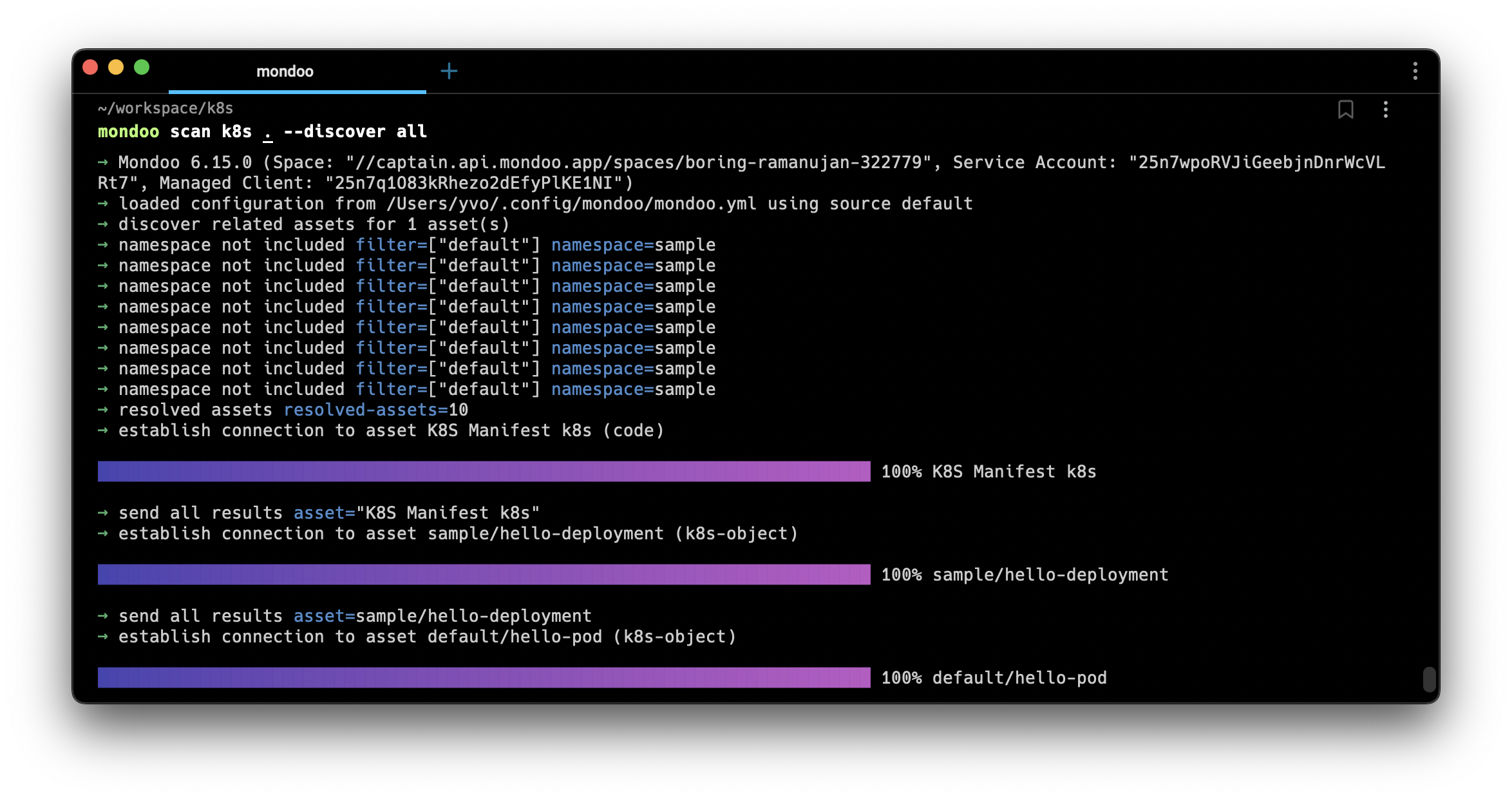
Solution: Mondoo Kubernetes scans now automatically scan cluster objects as assets. This provides a much more Kubernetes-friendly view of where security problems exist within your cluster. You can use our new policies with dozens of controls that aren't present in the legacy Kubernetes Application Benchmark policy.
Additionally, Mondoo scans now also respect the --discover all command line flag when scanning local manifests. This lets you scan individual Kubernetes resources and even the containers defined in your manifests.
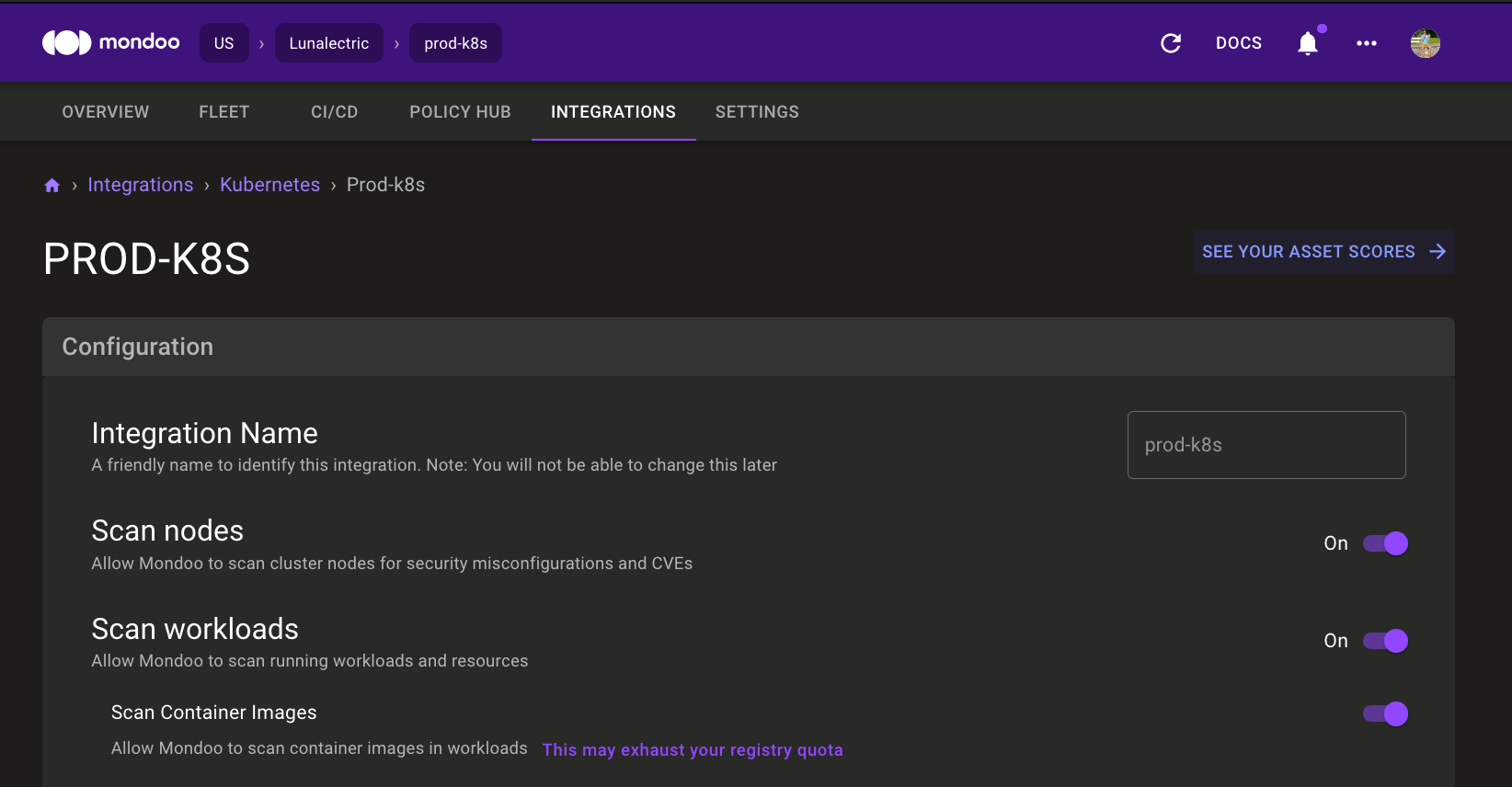
 Quickly Find Kubernetes Operator Scanned Assets
Quickly Find Kubernetes Operator Scanned Assets
We added a new See Your Asset Scores link in the Kubernetes Integration pages that takes you right to all the assets discovered by the Mondoo Operator.
Scan Kubernetes Resources on Add/Update
Problem: Mondoo's scan results don't always reflect the latest state of your Kuberenetes cluster. As new users deploy new and updated workloads to a cluster, these don't reflect the updates shortly after they happen.
Solution: Mondoo now scans your Kubernetes resources as they are updated or added to the cluster, so the fleet view always has the latest information on cluster-wide security.
Note: This requires the Mondoo Operator for Kubernetes 1.5 or later. To update to this new release, run:
kubectl delete --ignore-not-found -n mondoo-operator deployment
mondoo-operator-controller-manager
kubectl apply -f https://install.mondoo.com/k8s/operator
Automatic Cleanup of Kubernetes Resources
Problem: Resources come and resources go, but they sure add up quickly. Kubernetes clusters often contain large numbers of ephemeral resources. Over time, Mondoo's resource scanning results in spaces full of long-dead assets.
Solution: Mondoo now automatically cleans up Kubernetes assets older than 24 hours, keeping your spaces tidy and full of relevant scans.
New Kubernetes MQL Resources
k8s.admissionreview & k8s.admissionrequest
Mondoo now includes new k8s.admissionreview and k8s.admissionrequest resources that allow you to write policies against incoming deployments. Stay tuned as we expand this capability over time to allow additional control over the workloads that make it into your cluster.
k8s.kubelet
Problem: You need to secure your Kubernetes cluster nodes to secure your infrastructure, but the kubelet configuration system is complex. How do you handle the different names for the same configs and different defaults depending on the config location? Should you check the CLI flags, the YAML config, or the JSON config?
Solution: We've abstracted the complexity of parsing the kubelet config options into a new k8s.kubelet resource. The resource parses all three configuration locations, handles defaults, and understands the changing default values when config files are loaded. With this resource, you can write simple queries to check for kubelet config options and let Mondoo handle the heavy lifting of parsing Kubernetes configuration logic.
A manual query that does not account for default values:
if (props.kubeletconfigpath != null) {
cfg = parse.yaml(props.kubeletconfigpath).params
cfg["featureGates"]["RotateKubeletServerCertificate"] != null
cfg["featureGates"]["RotateKubeletServerCertificate"] == true
} else {
processes.where( executable.contains("kubelet")).all(flags["feature-gates"] == "RotateKubeletServerCertificate=true")
}An updated query that includes default value evaluation:
k8s.kubelet.configuration["featureGates"]["RotateKubeletServerCertificate"] == true
We've also updated our existing Kubernetes policies to use this new resource. This dramatically improves the reliability of configuration parsing in these policies, removing potential false positives.
env & envFrom in Kubernetes Containers
Problem: You want to write policies to ensure that only secure environment variables are passed into your Kubernetes workloads.
Solution: Container resources now expose the env and envFrom configs. This allows you to inspect manifests with plain text secrets being passed in using env vars like this:
apiVersion: v1
kind: Pod
metadata:
name: luna-frontend
namespace: prod
spec:
containers:
- name: luna-frontend
image: lunalectric/frontend:1.0
env:
- name: LOGIN
value: "oh_no"
- name: PASSWORD
value: "they_are_really_doing_this!"
Using a query to check for env var names:
k8s.pods.all(
containers.all(
env["LOGIN"] == null && env["PASSWORD"] == null
)
)
HashiCorp Terraform GitHub Action Support
The Mondoo GitHub Action 0.7.0 now includes two new actions for scanning your Terraform code:
- Terraform State File Action scans Terraform state files for security configuration best practices.
- Terraform Plan Action scans Terraform plan repositories for security configuration best practices.
Simplified Terraform State File Resource
We've simplified MQL access to resources from the Terraform state files.
Before this release, you had to iterate over all Terraform modules to get access to the resources:
cnquery> terraform.state.rootModule.resources { providerName == "registry.terraform.io/hashicorp/null" }
terraform.state.rootModule.resources: [
0: {
providerName == "registry.terraform.io/hashicorp/null": true
}
With this release, you can now access the resources directly from the state:
cnquery> terraform.state.resources
terraform.state.resources: [
0: terraform.state.resource id = null_resource.ls
]
mondoo exec Is Now mondoo run
We've updated the mondoo exec command to mondoo run. The existing command still works, but help now shows only mondoo run. We're making this change to align CLI options for some exciting new releases coming soon. Stay tuned for a major announcement!
Policy Updates
CIS AKS & GKE Benchmarks
Mondoo now includes CIS Level 1 and 2 benchmarks for both Azure Kubernetes Service (AKS) and Google Kubernetes Engine (GKE). These policies include critical controls for securing your cluster nodes and cluster workloads.
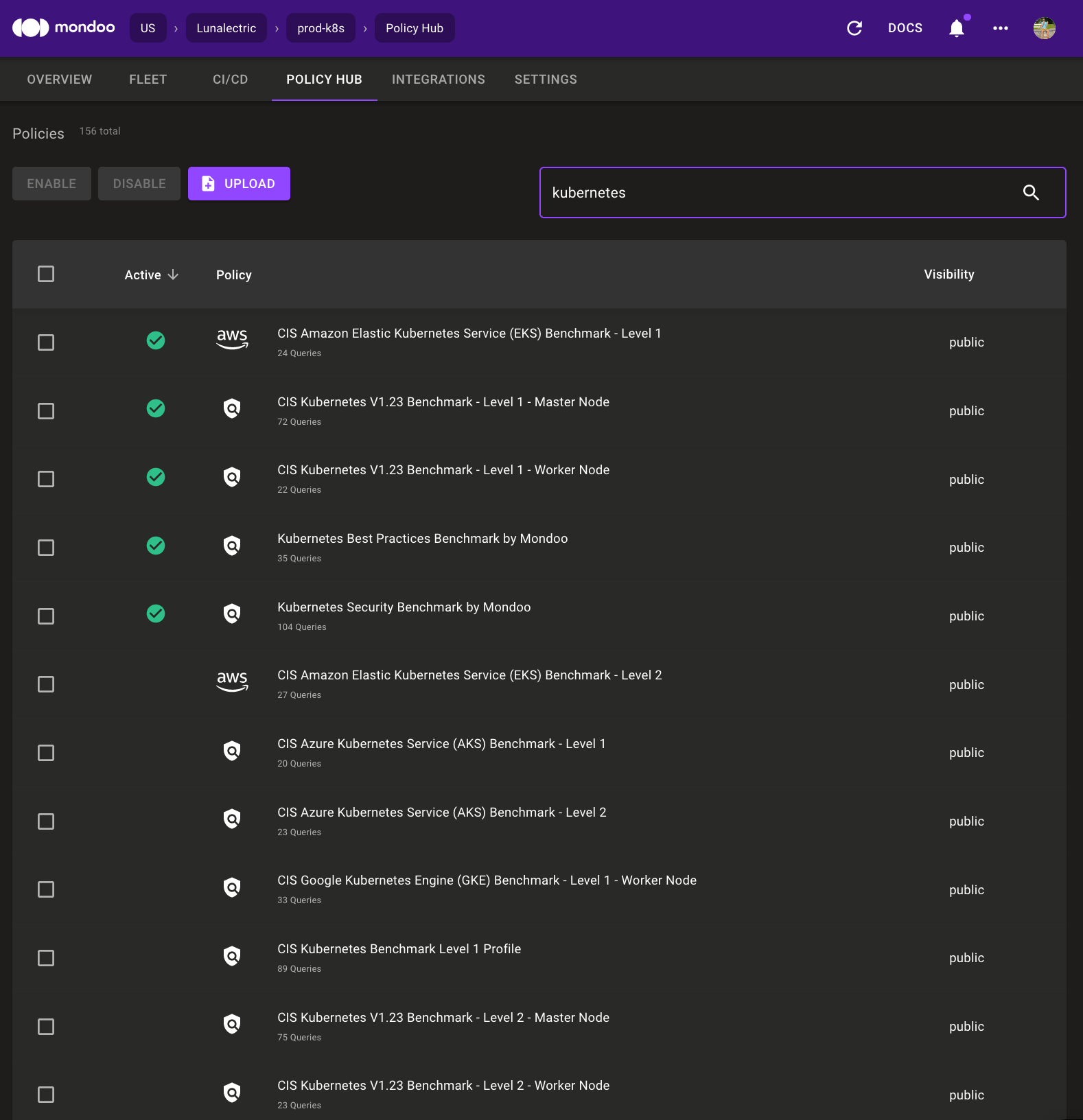
Kubernetes Policies
Problem: For most policies, results are reported as a flat list. It is very difficult to prioritize these results and determine what to fix first.
Solution: We've added priorities to the controls in CIS and Mondoo Kubernetes policies. You can now sort your scan results by priority and tackle the most important security issues first.
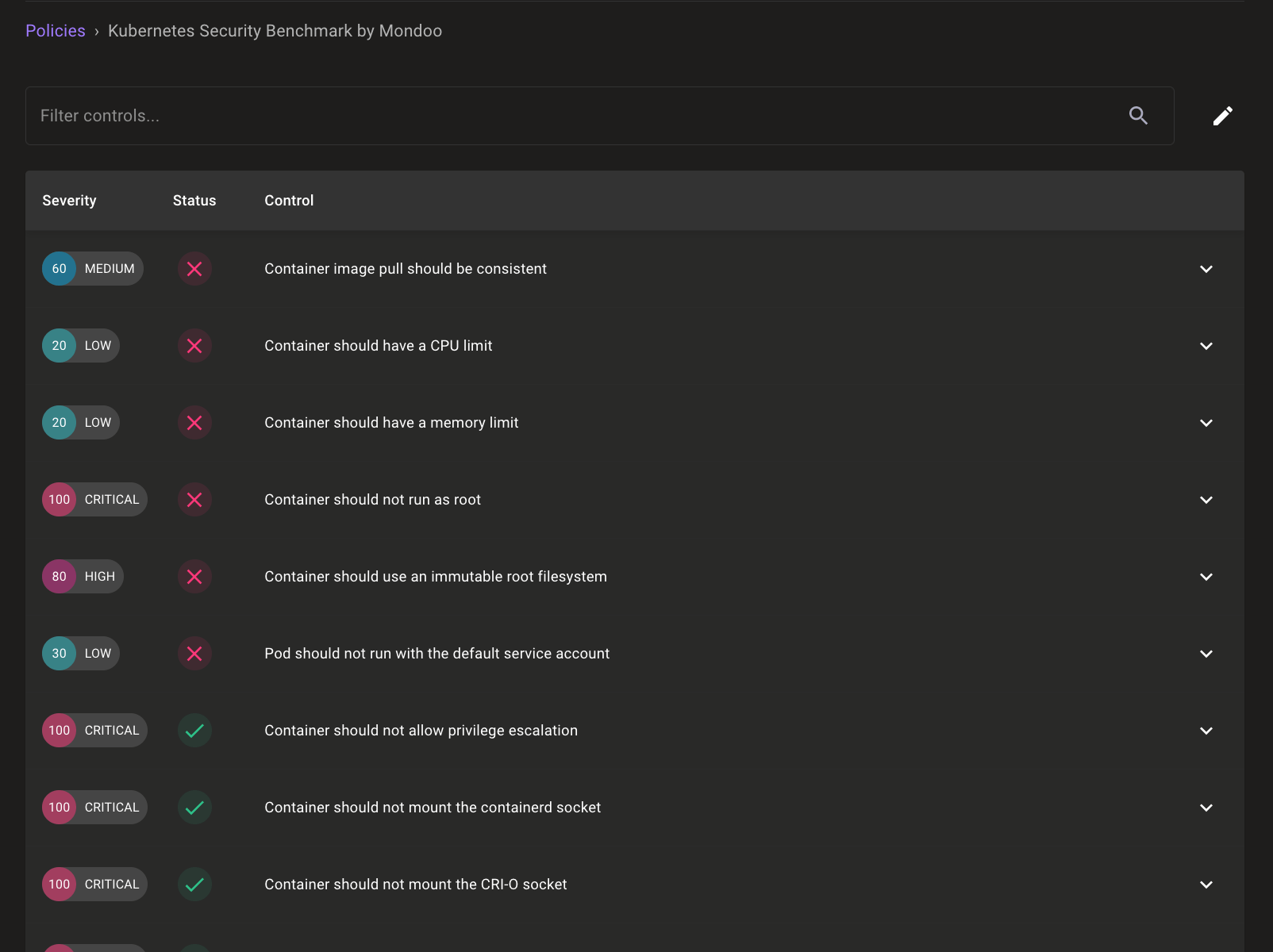
We've expanded our Kubernetes Security Benchmark and Kubernetes Best Practices Benchmark to expose more common misconfigurations in Kubernetes workloads.
- Workloads should not run in the default namespace—This new Kubernetes Best Practices Benchmark control discovers workloads that haven't defined a non-default namespace in which to run. It's best to group workloads into non-default namespaces to better organize work by teams and to isolate workloads.
- Workloads should not run with SYS_ADMIN capability—This new Kubernetes Security Benchmark policy discovers workloads with the SYS_ADMIN or ALL capabilities. The SYS_ADMIN capability is risky because it provides a pod with root capabilities.
- Workloads should not run with NET_RAW capability—This new Kubernetes Security Benchmark policy discovers workloads with the NET_RAW or ALL capabilities. Attackers can use the NET_RAW capability to craft fake packets on the host, which they can use to redirect network traffic bound for other pods.
- Pods should have an owner—This new Kubernetes Best Practices Benchmark control discovers pods that do not have an owner. These pods, commonly called naked pods, don't respawn if the node they're running on fails or terminates.
Finally, we made several improvements to the vanilla CIS Kubernetes Level 1 and 2 policies for master and worker nodes. Many controls previously marked as not implemented are now implemented and all file permission controls now pass when permissions are more secure than those required by CIS.
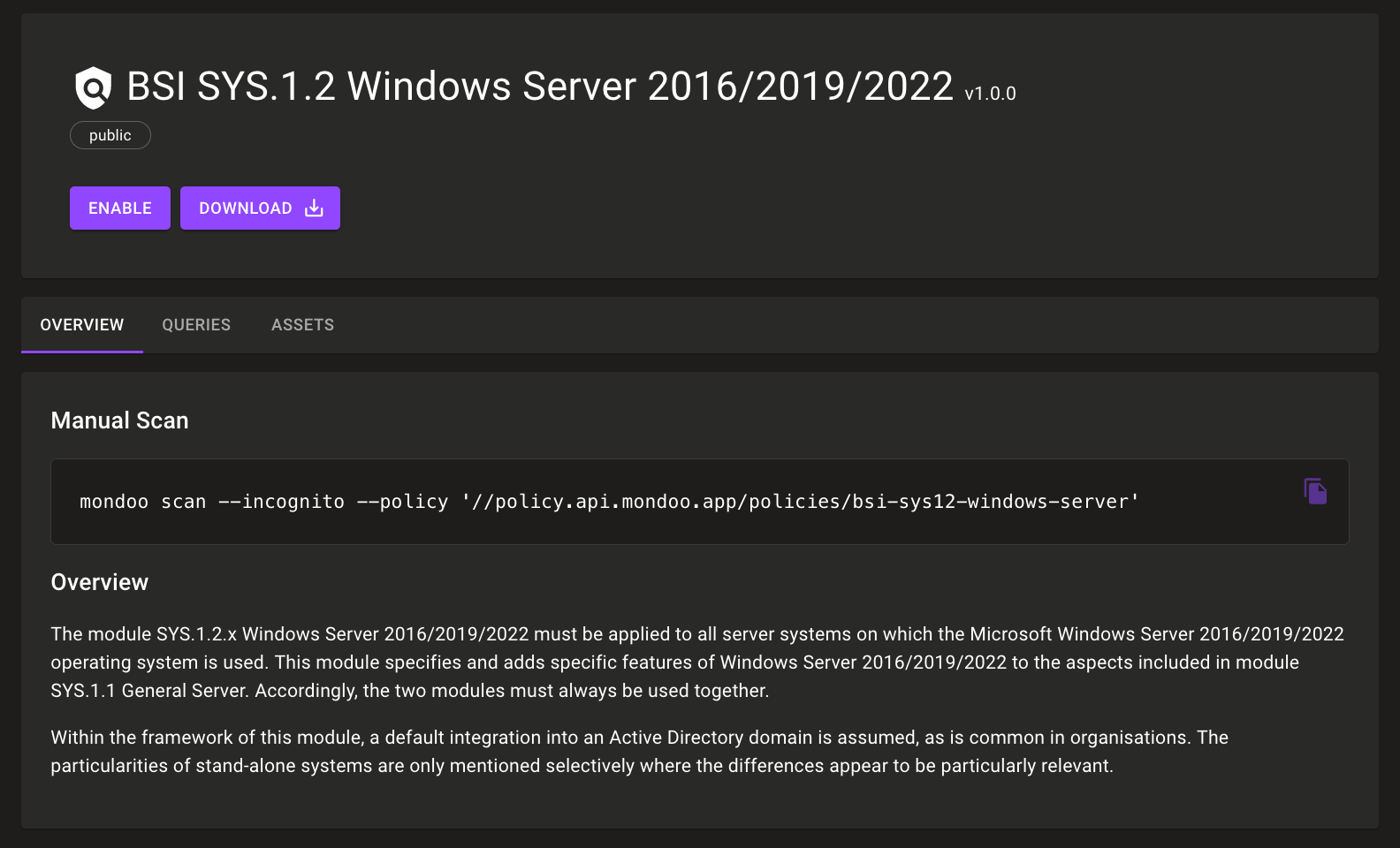
Bundesamt für Sicherheit in der Informationstechnik (BSI) Windows Policy
Problem: You want to secure your Windows systems according to the Federal Office for Information Security (BSI) and pass a BSI audit.
Solution: Mondoo now includes a new out-of-the-box BSI SYS.1.2 Windows Server 2016/2019/2022 policy. BSI is a German standard for IT security, similar to SOC2 in the US. This new policy complements our existing BSI SYS.1.3 Linux and Unix Servers policy for Debian- and Red Hat-based Linux systems. These policies are especially helpful for users in the DACH region and Germany in particular.
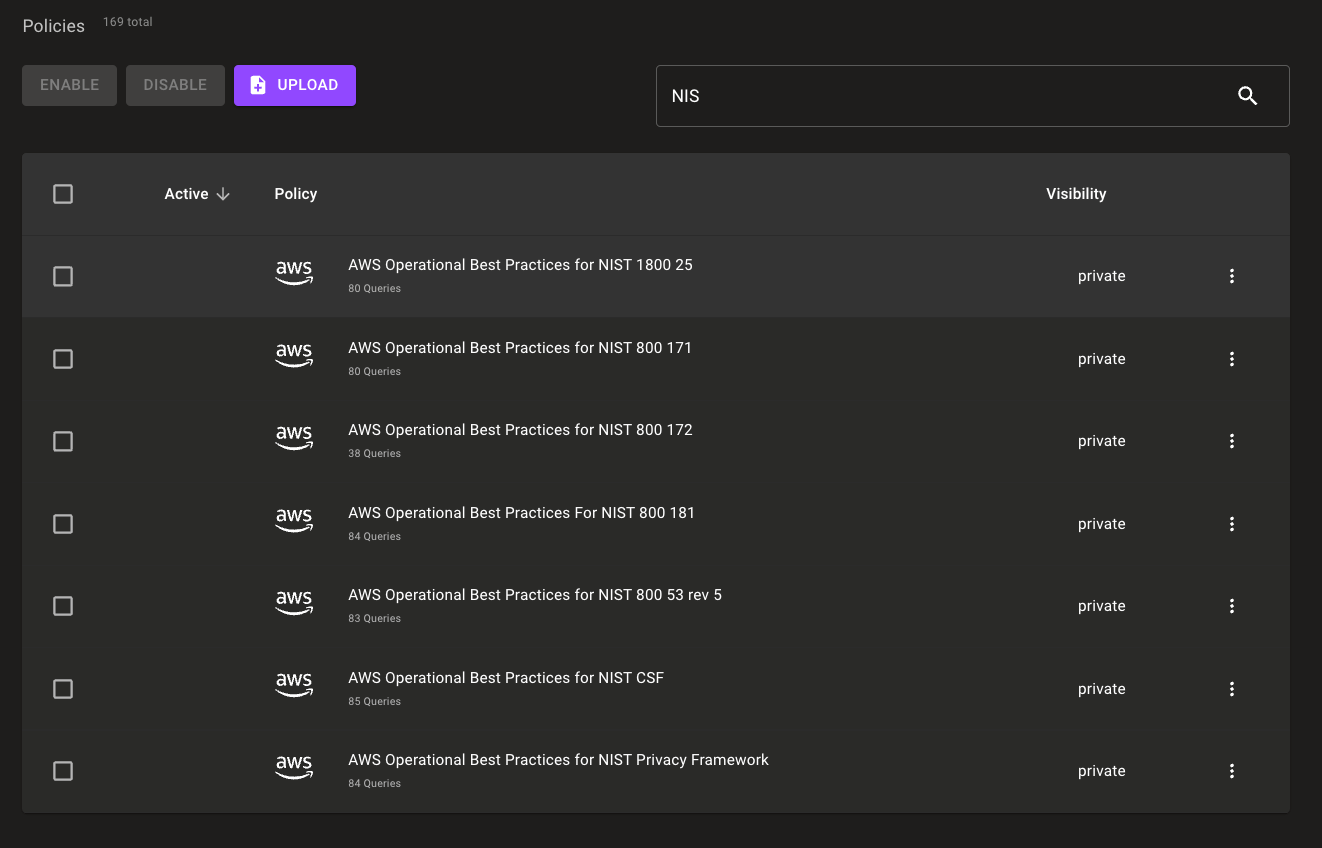
NIST Special Publication 800 Preview Policies for AWS
We're introducing a preview of five new NIST SP 800 policies to help you keep your systems in compliance with US federal government requirements.
Mondoo Policy for Google Cloud Terraform Plans
We have introducing a new policy, Terraform Plan - CIS Google Cloud Platform Foundation Benchmark. It lets you run Mondoo security scans directly against HashiCorp Terraform plans for your Google Cloud infrastructure.
BIOS Updates Control Added to Client Linux Security Baseline by Mondoo
The Client Linux Security Baseline by Mondoo now includes a control to validate that systems have the most up-to-date BIOS when the fwupd utility is installed.
Other Improvements
- mondoo shell & mondoo exec now support transport providers (such as mondoo shell terraform). The -t flag is now deprecated for both.
- Properly redirects users to the Welcome to Mondoo page after verifying their e-mail during sign-up.
- Improves the error message guidance when an AWS fails to check-in.
- Fixes the See Your Scores link in the AWS integrations pages to properly load the list of account assets.
- Properly detects the path to Grub2 configs in CIS benchmarks on Amazon Linux.
- Renames potentially confusing control titles in Linux Security Baseline by Mondoo policy.
- Skips internal fields in the mondoo shell help output.
- Improves error handling in the AWS Lamba scans.
-
Changes Mondoo agent searches to not be case sensitive.
-
Returns more helpful error messages from Mondoo Client when a necessary environment variable is missing on CI platforms.
-
Fixes missing available packages in asset Platform Vulnerabilities pages.
-
Improves the handling of null data for regular data types: We now consistently return non-null data from the upstream service. In the next major release, we will support storing other null data.
-
Fixes failures parsing Linux kernel parameters when files in /proc/sys can't be read.
-
Networks and domains are now properly grouped in the fleet view.
-
GitHub, Terraform, and cloud Kubernetes policies in the Policy Hub now include custom icons.
-
Updates Pods should not run with NET_RAW capability and Pods should not run with SYS_ADMIN capability controls in the Mondoo Kubernetes Security policy to not fail when no securityContext or capabilities are defined.
-
Resolves failures in Minimize the admission of root containers and Minimize the admission of containers with the NET_RAW capability controls in CIS Kubernetes policies.
-
Asset view once again includes the state of the asset's Mondoo Client.
-
Long policy names now truncate better in the asset view.
-
The --option command line flag is now properly passed through to AWS EBS-based scans.
-
The --token command line flag is now properly set when scanning GitHub organizations or repositories.
-
Scans in the CI/CD view no longer appear unscored.
-
Kubernetes cluster nodes are no longer part of the k8s-workload family.
-
Prevents failures checking kernel parameters if files in /proc/sys cannot be read.
-
Unknown scan status coloring is now always white throughout the console.
-
Corrects control counts on the asset pages.
-
Fixes small score donut charts on the asset pages.
-
Searches of scans from the Kubernetes Admission Controller are now case insensitive.
-
Adds missing breadcrumb links on the main Fleet page.
-
Corrects sample PowerShell setup commands on the Workstation Integration page.
-
Makes the asset type summary text more consistent.
-
Properly detects an asset's platform.
-
Improves the reliability and performance of removing policies and assets.
-
Improves reliability of EBS volume scans with the AWS integration.
-
mondoo.version queries now return the correct Mondoo Client version.
-
Resolves errors deleting CI/CD jobs.
-
Resolves Kubernetes cluster names reverting to UID from the friendly name in the CI/CD view.
-
Improves the reliability of CIS Kubernetes controls that inspect the state of the Kubelet.
-
mondoo scan aws ec2 ebs now respects the --option region option.
-
Resolves an error that could cause creation of empty AWS account assets when scanning instances.
-
Prevents errors in the Linux Security by Mondoo policy when /etc/shadow is not present on a system.
-
Container images no longer show up in the fleet view as container registries during scans.
-
Fixes parsing of OS uptime on some Linux distributions.
-
Corrects reporting of Kubernetes Integration errors while cluster during scans.
-
Scanning a Kubernetes cluster with an invalid namespace specified no longer creates an empty cluster asset.




