
We hit a major milestone in October: Mondoo version 7! For important information about changes in the release, see the Mondoo 7 Release Notes.
Additionally, we released two new projects to open source: cnquery as the cloud-native asset inventory and cnspec for security assessment. See this section for more information below.
We have a lot of exciting changes to share from our work this month as well:
Chapters
- Powered by new open source projects
- CLI CVE-only scanning
- CI Setup in Integration
- Better prioritized control views
- Status tabs on top of asset pages
- All Kubernetes Namespaces scanned by default
- Add ephemeralContainers to k8s.pod
- New Azure authentication options
- Long-lived registration tokens
- New service account UI
- Add MQL ports resource for macOS and Windows
- Load base64 configuration directly from env vars
- FreeBSD scanning support
- GitHub Discussions open for business
- Policy updates
- Other improvements
Powered by new open source projects
We are excited to announce the open source release of cnquery and cnspec. These are the core components of the Mondoo CLI and will replace it going forward:
- cnquery is an asset inventory and search engine that features an interactive shell, MQL runner, and query pack execution. Query packs bundle queries together. When you run a query pack, the queries automatically execute and collect all data. They're useful for creating asset inventories and collecting data during incidents. Query packs are a lightweight alternative to policies (without scoring).
- cnspec is our security testing project, which focuses on misconfigurations and vulnerabilities. It's built on top of cnquery and adds policies and scored controls. It's also a drop-in replacement to the Mondoo CLI and uses the same commands to scan assets, run queries, open a shell, or work with policies.
Together with this open source release, we're giving the Mondoo community the ability to create custom resources and providers. In the coming weeks we'll start to release more guides for developers who are interested in contributing.
Furthermore, we are solidifying MQL as an open standard for GraphQL-based infrastructure querying and assertions. Most of the engine can be found in cnquery. It's highly extensible as well as embeddable.
We enthusiastically encourage you to try out cnquery and cnspec! Please let us know if you encounter any challenges switching from the Mondoo CLI to cnspec. We'll continue to support the Mondoo CLI throughout the v7 release.
CI setup in integrations
Problem: You want to set up Mondoo to scan projects through your favorite CI systems, but the setup is manual and requires jumping between the Mondoo console and documentation.
Solution: We've revamped Mondoo CI integrations to make them faster and more intuitive to set up. Gone are the manual service account setup process and documentation site, and in their place are CI projects set up through the Integrations tab in the console, just like other integrations. Mondoo automatically creates service account tokens and the integration setup process now suggests helpful policies for use with your CI projects.
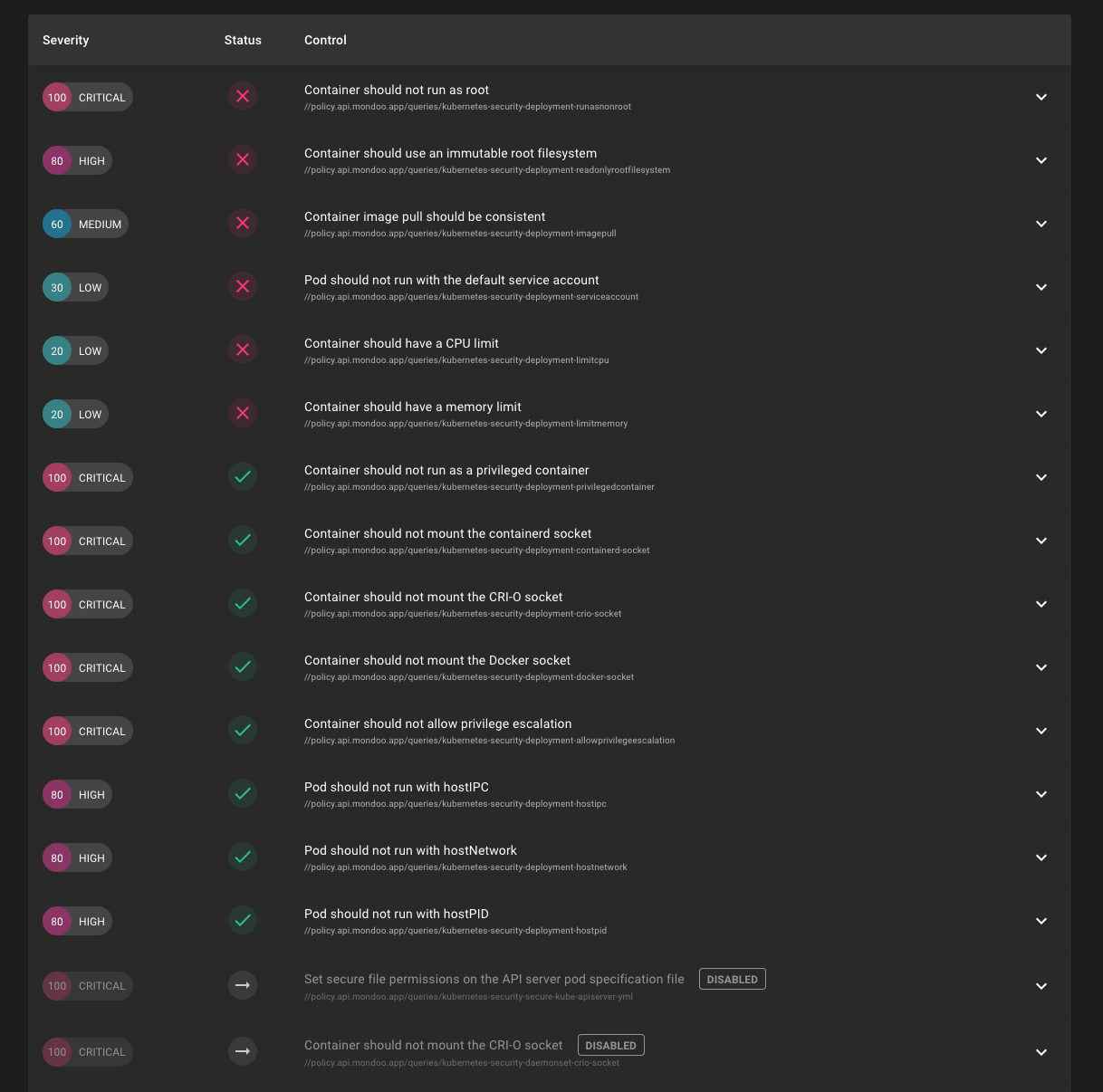
Better prioritized control views
Problem: Policies on your assets can have hundreds of controls and you need to evaluate the security of an asset at a glance.
Solution: We've improved how controls in policies display to make it easier to quickly understand the security posture of your assets. Skipped policies now display at the bottom of the results, which makes it easier for you to see the controls that have passed or failed. This is particularly useful when viewing the results of the Mondoo Kubernetes Security policy, which has many workload controls skipped depending on the asset type. We also now sort by severity within each status so you can quickly see the highest severity failed controls.
You can also manually sort on any column in the results, so you can always view the data just how you like.
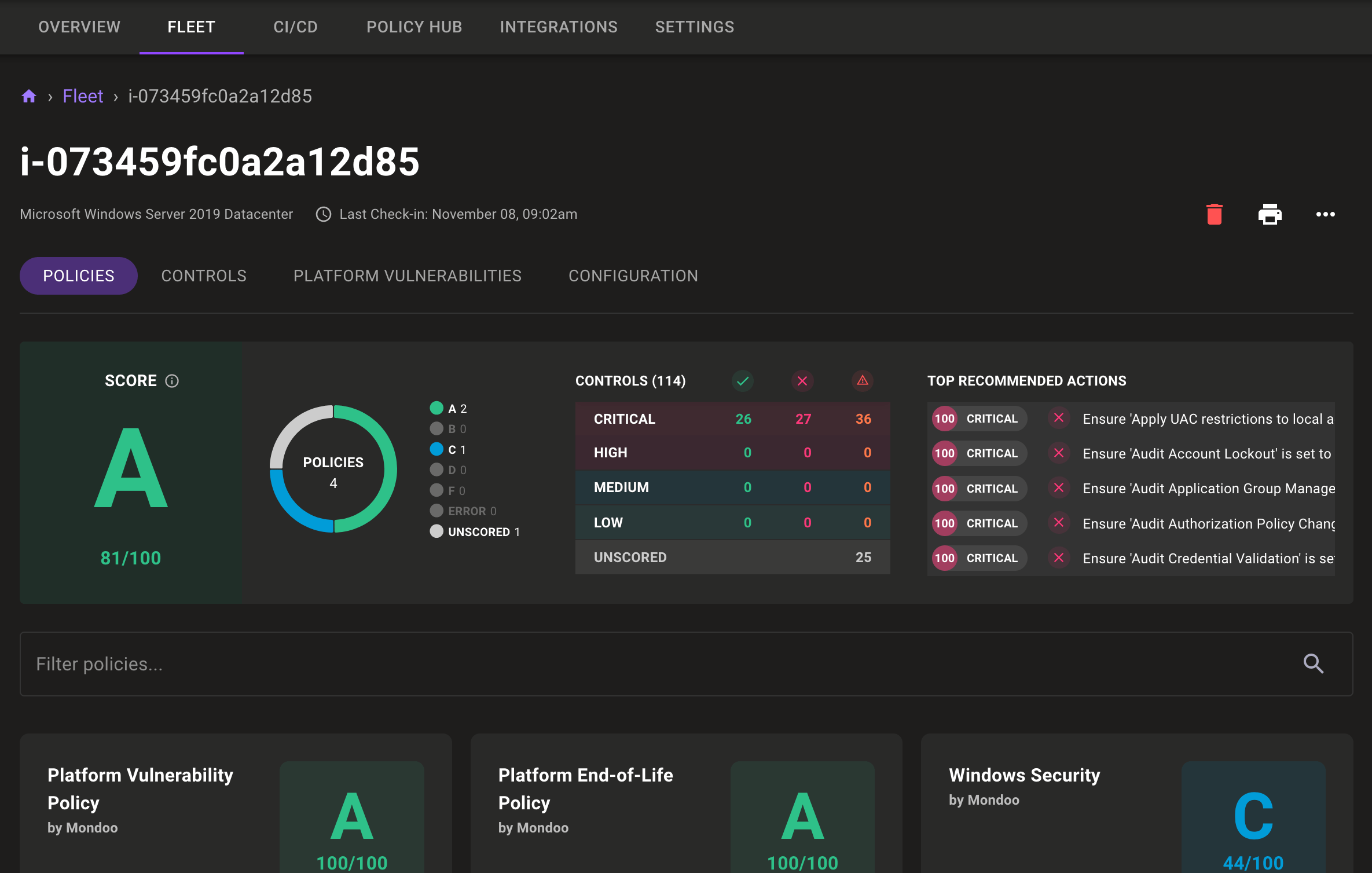
Navigation tabs on asset pages
Asset pages now include tabs for navigating between policies, controls, configuration, and vulnerabilities at the top of the page. Not only are these a bit easier to find in their new location, but also the content of these tabs now shows on the whole screen so you can better explore the data.
Scan all Kubernetes namespaces by default
Problem: You want to scan your Kubernetes cluster, but it includes workloads from many different namespaces, which aren't scanned by default.
Solution: By default Mondoo now scans all Kubernetes namespaces. This means you can now achieve a complete cluster scan with just mondoo scan k8s. We've deprecated the --all-namespaces CLI flag and will remove it in a future release. If you want to limit a scan to just a single namespace, you can still do so by specifying the namespace on the CLI with --namespace FOO.
Add ephemeralContainers to k8s.pod
The k8s.pods and k8s.pod resources now include information on ephemeralContainers attached to the Pods. ephemeralContainers are a relatively new feature in Kubernetes. They let you attach containers to Pods for debugging. You can't remove them, and if you forget about them, they can introduce significant security risks to your environment.
Example workload with ephemeralContainers defined:
apiVersion: v1
kind: Pod
metadata:
annotations:
creationTimestamp: "2022-11-03T16:40:54Z"
labels:
admission-result: pass
name: passing-pod-yaml
namespace: debug-ns
resourceVersion: "75952"
uid: 823d82d5-890e-4d6a-9da6-404648144585
spec:
automountServiceAccountToken: false
containers:
...
dnsPolicy: ClusterFirst
enableServiceLinks: true
ephemeralContainers:
- args:
- sleep
- "9999"
image: busybox:1.28
imagePullPolicy: IfNotPresent
name: ephemeral_junk
resources: {}
securityContext:
privileged: true
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
preemptionPolicy: PreemptLowerPriority
priority: 0
restartPolicy: Always
…
New Azure authentication process
Problem: You want to secure your Azure infrastructure, but you don't want to authenticate using less secure methods like token authentication.
Solution: Mondoo now includes additional options for authenticating against your Azure infrastructure, including those that enable security features such as MFA. You can now authenticate to your Azure infrastructure using certificates or a client ID and secret.
Certificate authentication:
cnquery shell azure --client-id --certificate-path /Users/stella/certificate.pfx --tenant-id --certificate-secret supersecretClient ID/secret authentication:
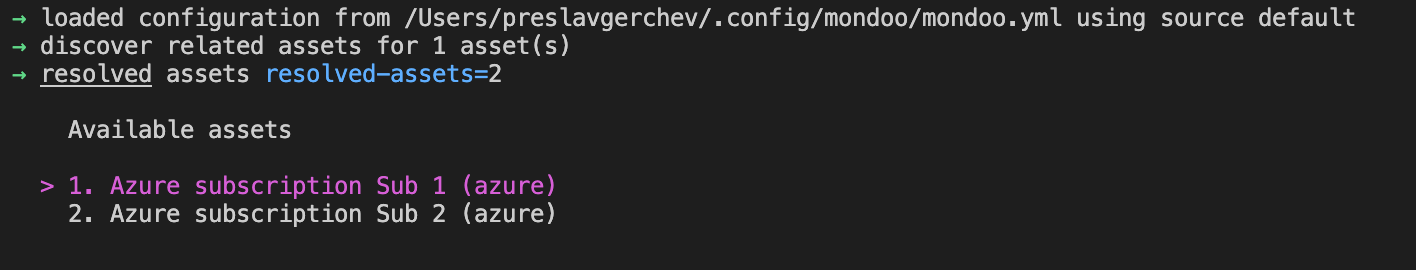
cnquery shell azure --client-id --tenant-id --client-secret my_secretIf you don't specify an authentication method, Mondoo uses the method you've set up for the az CLI. So if you prefer shorter CLI commands, feel free to leave out the authentication flags entirely.
We also know you often have multiple subscriptions, so we've made it easy to select subscriptions. If the subscription flag is not set, you'll get a CLI menu of possible subscriptions to use:
CLI CVE-only scanning
Problem: Sometimes you only care about CVEs on a server, container, or container image, but you have to scan the system for security misconfigurations as well.
Solution: We've added a new `cnspec vuln` command that allows you to scan for CVEs on servers, containers, and container images without performing a full security scan. The command also offers more detailed CVE output so you can see what's best to patch first.
 Long-lived registration tokens
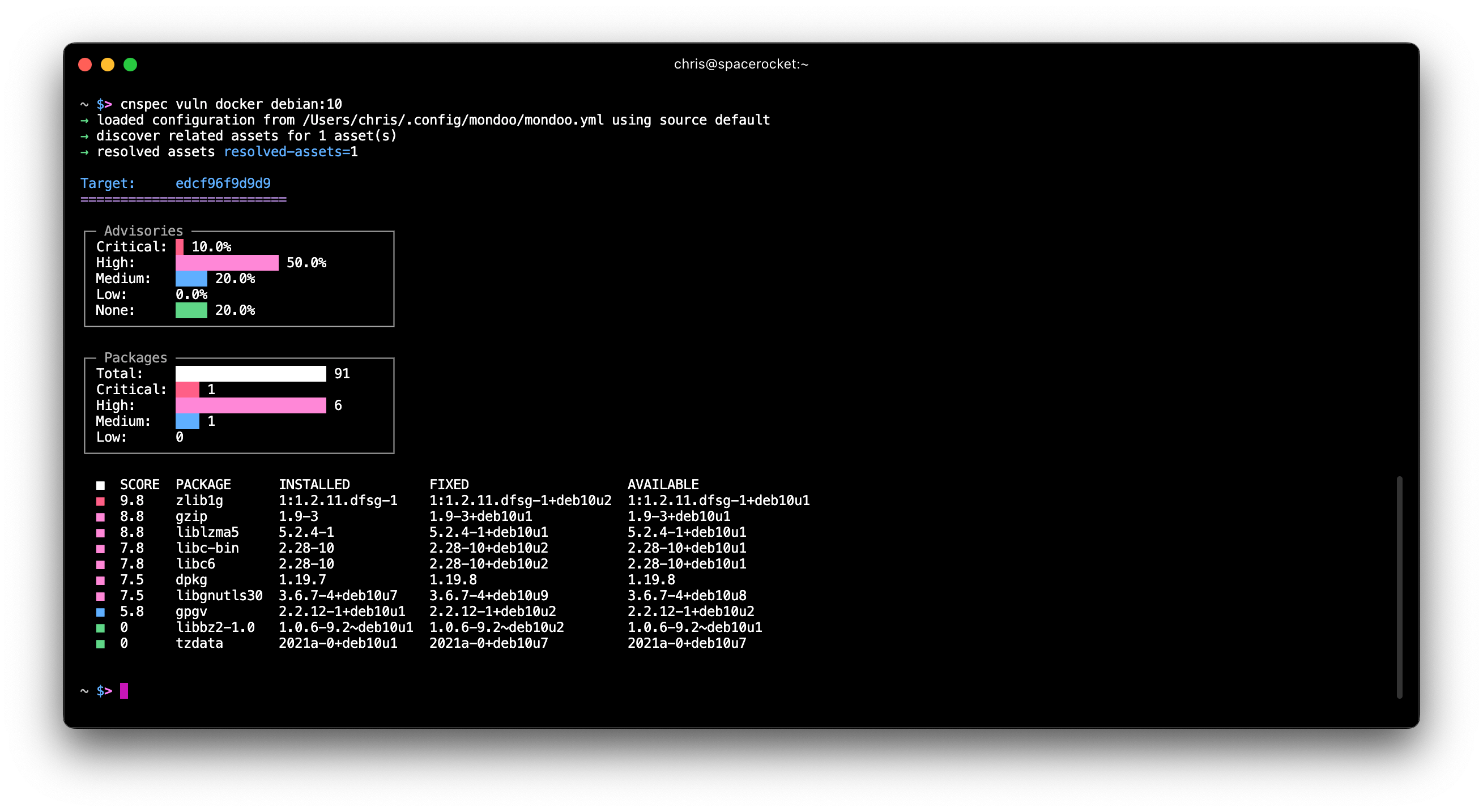
Long-lived registration tokens
Problem: You want to automate the registration of new nodes into the Mondoo Platform, but it's difficult when new registration tokens need to be generated constantly.
Solution: You can now generate long-lived (aka non-expiring) registration tokens in the UI. These are ideal for automated processes like auto-scaling groups where tokens are stored in secrets management systems and cannot expire.
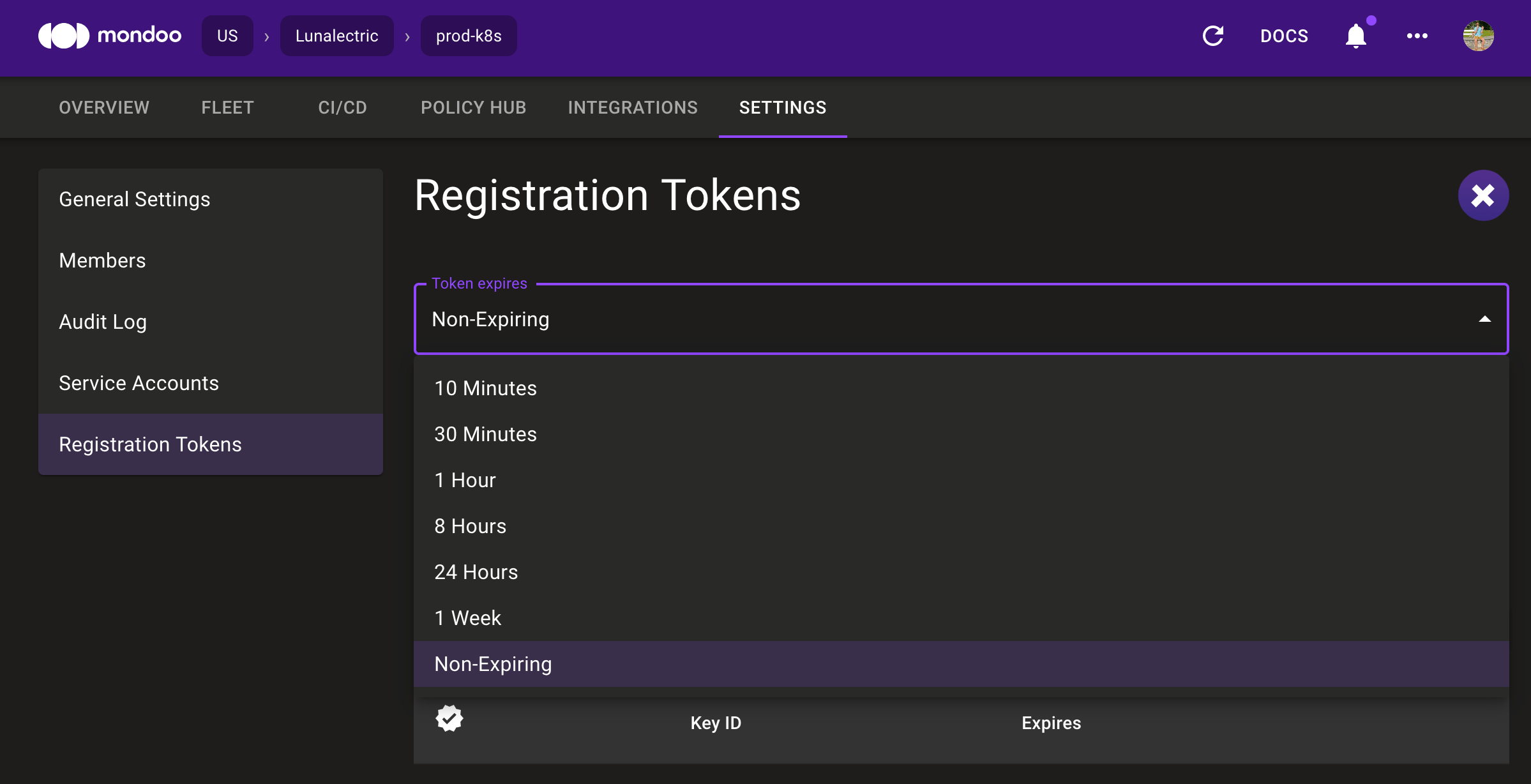
New service account UI
Problem: Each integration you set up in Mondoo adds a service account. Managing these accounts can be difficult if you want to remove unused accounts or view usage.
Solution: We've updated the service account page to make it easier to manage service accounts. The new UI exposes important information like the creation date, the last used date, and what created the account. You can also expand each item in the list to link to the integration using the service account, change permissions, or delete the account.
Add MQL ports resource for macOS and Windows
cnquery> ports.listening
ports.listening: [
port port=56863 protocol="ipv4" address="*" process.executable="/usr/libexec/rapportd"
port port=56863 protocol="ipv6" address="*" process.executable="/usr/libexec/rapportd"
port port=7000 protocol="ipv4" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/MacOS/ControlCenter"
port port=7000 protocol="ipv6" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/MacOS/ControlCenter"
port port=5000 protocol="ipv4" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/MacOS/ControlCenter"
port port=5000 protocol="ipv6" address="*" process.executable="/System/Library/CoreServices/ControlCenter.app/Contents/MacOS/ControlCenter"
port port=44960 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=44950 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=18412 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=7335 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=17223 protocol="ipv4" address="127.0.0.1" process.executable="/Users/chris/Library/Application"
port port=17223 protocol="ipv6" address="[::1]" process.executable="/Users/chris/Library/Application"
]Load base64 configuration directly from env vars
cnspec now loads a Base64-encoded configuration from the MONDOO_CONFIG_BASE64 env var. This means you no longer need to load the Base64-encoded config in your CI jobs, write it out to a config file on disk, and then run cnspec to scan your CI job.
Previously CI jobs had to write the config to disk:
echo $VARIABLE_WITH_BASE64_CONFIG > mondoo.json
cnspec scan k8s my_file.yml --config mondoo.jsonNow with MONDOO_CONFIG_BASE64 set you can just run the CLI:
cnspec scan k8s my_file.ymlFreeBSD scanning support
cnquery and cnspec now include initial support for remotely scanning FreeBSD hosts. With this update, you can now list packages and services, examine file contents, and execute commands. Stay tuned for more FreeBSD updates, and if you have thoughts or would like to contribute resource support for FreeBSD, join the Mondoo GitHub Discussions.
GitHub Discussions open for business
Problem: You have a question about writing policies or scanning hosts with Mondoo, but nothing comes up in search engines, and waiting on Slack responses can take a while.
Solution: We decided to move our main community presence to GitHub Discussions. Slack is fantastic for real-time discussions, but it's problematic for getting quick answers to common questions. With GitHub Discussions, every question asked in the past is available in search. Over time this builds up an extensive FAQ resource. You can find these discussions at https://github.com/orgs/mondoohq/discussions. We already started to move interesting topics there, so you'll find plenty of MQL guidance. We'll still be around on Slack and Discord for interactive chat, but prefer to discuss common topics on GitHub now.
Policy updates
New Mondoo policies replacing existing policies
We've introduced newly renamed Mondoo out-of-the-box policies. These policies include more consistent policy and UID names to differentiate security and best practices as well as the new scoring system mentioned below. We've marked the existing policies as deprecated to avoid impacting you at this time.
You can switch to these new policies in the Policy Hub by disabling the deprecated policy and enabling the new policies. At a later date we will automatically migrate users from the existing policies to these new policies. Stay tuned for more details!
New policy scoring evaluation
We've updated our out-of-the-box Mondoo policies to use a more appropriate scoring system. With this change the overall score a policy receives is now always reflecting the most critical failure. Previously, we would compute an average for all failed controls, which sometimes hid critical controls.
With this change high impact controls in policies are not hidden by a large number of low impact passing controls anymore. For many users this will increase the number of low scoring policies in their spaces by exposing controls that are failing.
NSA/CISA Kubernetes Hardening Guidelines preview policy
Mondoo now includes a preview policy implementing the NSA/CISA guidance. This guidance looks at Kubernetes security in the control plane, cluster nodes, and workloads. Stay tuned for updates to this policy in the coming weeks.
Be sure to check out the NSA's press release announcing this new guidance document, which includes a link to the complete PDF: https://www.nsa.gov/Press-Room/News-Highlights/Article/Article/2716980/nsa-cisa-release-kubernetes-hardening-guidance/
New controls for macOS security policy
We've added new controls to the macOS Security policy to make sure that automatic updates are securely configured:
- Ensure automatic checking of software updates enabled
- Ensure automatic download of software updates enabled
- Ensure critical updates are installed automatically
Policies for OpenSSL
Problem: You want to apply a specific policy to find instances or containers running OpenSSL versions vulnerable to the recently announced CVE-2022-3786 and CVE-2022-3602 CVEs.
Solution: We've introduced a new policy, OpenSSL Vulnerability Policy by Mondoo, to specifically report on CVEs in OpenSSL so you can more easily target these systems for remediation.
More severity data in policies
Problem: At first scan, Mondoo finds an enormous pile of security issues in your environment for you to tackle. Which ones are the most important?
Solution: We've continued to improve Mondoo's ability to help you prioritize your work with severities in policies. Our Windows policies now all include severity data. We've adjusted Linux policies to make sure you're tackling the most pressing issues first.
Updated EOL data
We've updated our platform EOL data with new platform versions, so you always have the most up-to-date data:
- Added Google Container OS 101 with a release date of Sept 15, 2002, and an EOL date of Sept 1, 2024.
- Added Google Container OS release date information for milestone 97, 93, and 89.
- Added macOS 13.0 with a release date of Oct 24, 2022.
- Updated macOS 10.14 with an EOL date of July 21, 2021 when the last security update was released.
Additional policy improvements
- All Mondoo policies now include additional usage guidance with examples of how to run the policies using cnspec.
- When using incorrect providers in cnquery and cnspec, Mondoo now warns users and display the available providers instead.
- When scanning VMware vSphere assets, Mondoo now automatically discovers all ESXi hosts.
- Linux Security by Mondoo policy's audited controls now fail instead of erroring if audited configs are not found.
- Policy control UIDs in Mondoo TLS/SSL Security Baseline, Linux Workstation Security by Mondoo, and Linux Security by Mondoo policies better describe what they check.
- The Kubernetes Cluster and Workload Security by Mondoo policy's "Ensure that the Kubernetes PKI/SSL directory is owned by root:root" control properly handles paths on Minikube.
- CIS Kubernetes Worker Node Level 1 policy's "Ensure that the Kubelet only makes use of Strong Cryptographic Cipher" no longer results in a query error on Minikube.
- CIS Kubernetes Master Level 1 policy's "Pod Security Standards" controls have been updated to not run against workloads.
- CIS Ubuntu 20.04 Server Level 1 policy's "Ensure password creation requirements are configured" no longer errors if PAM is not installed, such as when Mondoo is scanning a container or container image.
- CIS Ubuntu 20.04 Server Level 1 policy's "Ensure chrony is configured" no longer errors if chrony's config is not found.
- Updated the Terraform HCL Security Static Analysis for Google Cloud policy's "Ensure that Cloud Storage bucket is not publicly accessible" control to improve reliability.
- NSA Kubernetes Hardening Guide Version 1.2 policy's "Ensure that the --audit-log-maxsize argument is set to 100 or as appropriate" and "Ensure that the --audit-log-maxbackup argument is set to 10 or as appropriate" checks now audit for the proper values.
- NSA Kubernetes Hardening Guide Version 1.2 policy now includes new controls to check for secure cryptographic ciphers on the API Server and Kubelets.
- Added missing queries to controls in the AlmaLinux CIS benchmark.
- Added new "Limit the access of Pods to cloud metadata services" control to the NSA Kubernetes Hardening Guide Version 1.2 policy.
- Added new "Minimize and verify access to secrets" control to the NSA Kubernetes Hardening Guide Version 1.2 policy.
- Updated Kubernetes Cluster and Workload Security policy to avoid failures scanning Kubernetes master nodes.
Other improvements
- Improve the security of the Mondoo Kubernetes Operator by dropping unnecessary privileges from any pods that are created by the operator.
- If part of a control name is clipped due to the size of the Top 5 Recommended Actions tile, you can now hover over the titles for a tooltip with the complete name.
- Fix failures to properly filter on tags when scanning AWS instances.
- Fix failures parsing the contents of /proc/sys when a file was empty.
- Fix incorrect asset counts in the fleet view after an asset was deleted.
- Kubernetes manifest names in the shell now show as the file name and not the file's directory.
- Improve help text to make it more clear what commands do.
- Remove the undocumented mondoo scan github user sub-command. Stay tuned for the return of this command with more clear use cases for scanning all user repositories.
- Use sysctl to scan Linux kernel parameters where we can to prevent failures scanning /proc/sys in some scenarios.
- Properly read the exit codes of commands that are executed on Docker containers.
- Improve error output when connecting to AWS accounts.
- Do not panic when querying a single k8s resource without providing id/name.
- Do not fail when using k8s.networkPolicies if a cluster has the Calico CNI.
- Registration tokens properly refresh in the integrations setup UI pages.
- Prevent failures to scan EC2 instances when a single keypair is missing.
- Fix failures using MS365 certificate authentication.
- Fix failures in search filtering for Kubernetes admission controller assets.
- Add links to download Mondoo client to the manual setup instructions on the Workstation integration page.
- Add missing breadcrumbs to the Policy Hub pages to make it easier to navigate.
- Avoid a scan failure when a /proc/sys file cannot be read.
- Don't show controls skipped due to conditionals in policies as being disabled on assets.
- Don't show double asset scans in the CI projects.
- Fix container images being incorrectly classified as operating system assets.
- Fix incorrect breadcrumb names on some integration pages.
- Fix incorrect Kubernetes namespace IDs in k8s.namespaces{ id } if Kubernetes objects have no namespace.
- Fix the --sudo flag not being honored when running mondoo scan.
- Fix the mondoo.version MQL query not returning the correct version.
- Google Container OS systems are now properly categorized as operating systems instead of "Uncategorized Assets."
- Mondoo platform links for CI/CD jobs on the CLI now go to the proper CI/CD asset view.
- Only show asset scheduled EOL warning if the vendor has scheduled the EOL for less than one year in the future.
- Performing an empty search in the Fleet view no longer goes to an error page.
- Policy descriptions on Policy Hub no longer suggest the legacy mondoo scan -t CLI format.
- Policy Hub no longer lists potentially incorrect manual scan instructions.
- Properly render the list of assets when navigating through the pagination.
- Remember the previous fleet filter selection when returning to the fleet page after viewing an asset.
- Resolve failures running mondoo scan gitlab.
- Resolve multiple errors when running CIS Kubernetes Master Level 1 policy on Minikube clusters.
- The initial load of the Mondoo console no longer flashes white when dark mode is enabled.
- Updates the VMware and Azure integration pages to use the latest mondoo scan syntax.
- Warn when using mondoo scan k8s --namespace if the namespace was not found on the cluster.
- Detect Rocky Linux 9 as platform family redhat so package and service resources function properly.
- Better raise permission issues when running the ports resource.
- Do not panic in cnquery when there are no query bundles.
- Escape JSON data to prevent errors parsing some values.
- If an asset is terminated mid-scan, report it as unscored instead of an error.
- Fix asset filter not properly applying Terraform HCL Security Static Analysis for AWS policy.
- Update EOL dates for Debian releases to the latest versions on their wiki.
- Improve spacing of EBS volume scans to reduce API throttling.
- Greatly improve the speed of service account and space deletion.
- Fix typos in NSA Kubernetes Hardening Guide Version 1.2 policy.
- Resolve errors when checking for default ingress/egress network rules in NSA Kubernetes Hardening Guide Version 1.2 policy.
- Resolve errors when checking for the PKI directory on Minikube in NSA Kubernetes Hardening Guide Version 1.2 policy.
- Avoid incorrect CVE counts for assets in the console.
- Update the Amazon Linux 2 EOL date to reflect the updated date of June 30, 2024.
- Detect the upcoming Fedora 37 release in the EOL policy.
- Improve error messages in the Mondoo Kubernetes Operator when private images cannot be scanned.
- Fix errors running github.repository { webhooks } if no webhooks were found.
- Fix errors running aws.rds.dbClusters {*}.
- Add state data to the aws.ec2.snapshot resource.
- Resolve failures loading base64 configs from env vars in cnspec.
- Resolve a panic when running cnspec in GitHub Actions.
- The install script now points users to GitHub Discussions not Slack.
- Improve cleanup of Kubernetes admissions controller scans older than 30 days to improve performance in spaces.
- EOL warning banners now show up on asset pages after an asset becomes EOL with the OS vendor.
- Show errors when policies cannot be uploaded to Policy Hub.
- Resolve errors with pagination on the asset not behaving as expected.
- Resolve incorrect links in Microsoft Teams notifications.



