A quick introduction to the Kubernetes Hardening Guide by the NSA and CISA
The NSA and CISA have released the Kubernetes Hardening Guide. This is a rare event as it is one of the few times the NSA has given guidance on system hardening.
It speaks to the need for organizations to properly secure their Kubernetes clusters. Kubernetes (K8s) has become widely popular because of its ability to cover so many different use cases. It's easy to get a Kubernetes cluster up and running. However, a system so complex and configurable can be hard to manage from a security perspective.

With this hardening guide, these two federal agencies aim to "help organizations handle Kubernetes-associated risks and enjoy the benefits of using this technology." They cover these topics:
- Scan containers and Pods for vulnerabilities or misconfigurations.
- Run containers and Pods with the least privileges possible.
- Use network separation to control the amount of damage a compromise can cause.
- Use firewalls to limit unneeded network connectivity and use encryption to protect confidentiality.
- Use strong authentication and authorization to limit user and administrator access as well as to limit the attack surface.
- Capture and monitor audit logs so that administrators can be alerted to potential malicious activity.
- Periodically review all Kubernetes settings and use vulnerability scans to ensure risks are appropriately accounted for and security patches are applied.
The agencies provide detailed recommendations, which make up the bulk of the guide, followed by a few configuration examples. They're great guidelines, but here's the catch: Verifying that your infrastructure follows those recommendations is a daunting task. Without the right tool, it becomes even more difficult.
Mondoo to the rescue!
Recently Mondoo released a policy that does all that heavy lifting for you!
Enter: The “NSA Kubernetes Hardening Guide Version 1.2” policy by Mondoo.
We created this policy specifically to address the recommendations set by the NSA and CISA. It covers these Kubernetes resources:
- Kubernetes API Server
- Kubelet
- Configmaps
- CronJobs
- DaemonSets
- Deployments
- Jobs
- Network Policies
- Pods
- Pod Security Policies (deprecated)
- Pod Security Admissions (> 1.23)
- RBAC
- Roles
- RoleBindings
- ClusterRoles
- ClusterRoleBindings
- ReplicaSets
- StatefulSets
Run the "NSA Kubernetes Hardening Guide Version 1.2” policy by Mondoo on your cluster
Here are step-by-step instructions for using Mondoo to ensure that your Kubernetes cluster follows all the NSA/CISA recommendations.
🌟 If you need a Kubernetes cluster, just use one of the Terraform templates from https://github.com/Lunalectric/container-escape to spin up a Kubernetes cluster in Azure or AWS. (Lunalectric is a sample entity we use for demos.)
Use the Mondoo Console
1. Create a Mondoo account.2. Make sure that you can connect to the Kubernetes cluster in question using your CLI. You can quickly check:
$ kubectl get namespaces
3. Do a preliminary scan of your cluster:
$ cnspec scan k8s
4. Follow the Report URL link and see the scan results in the Mondoo Console.
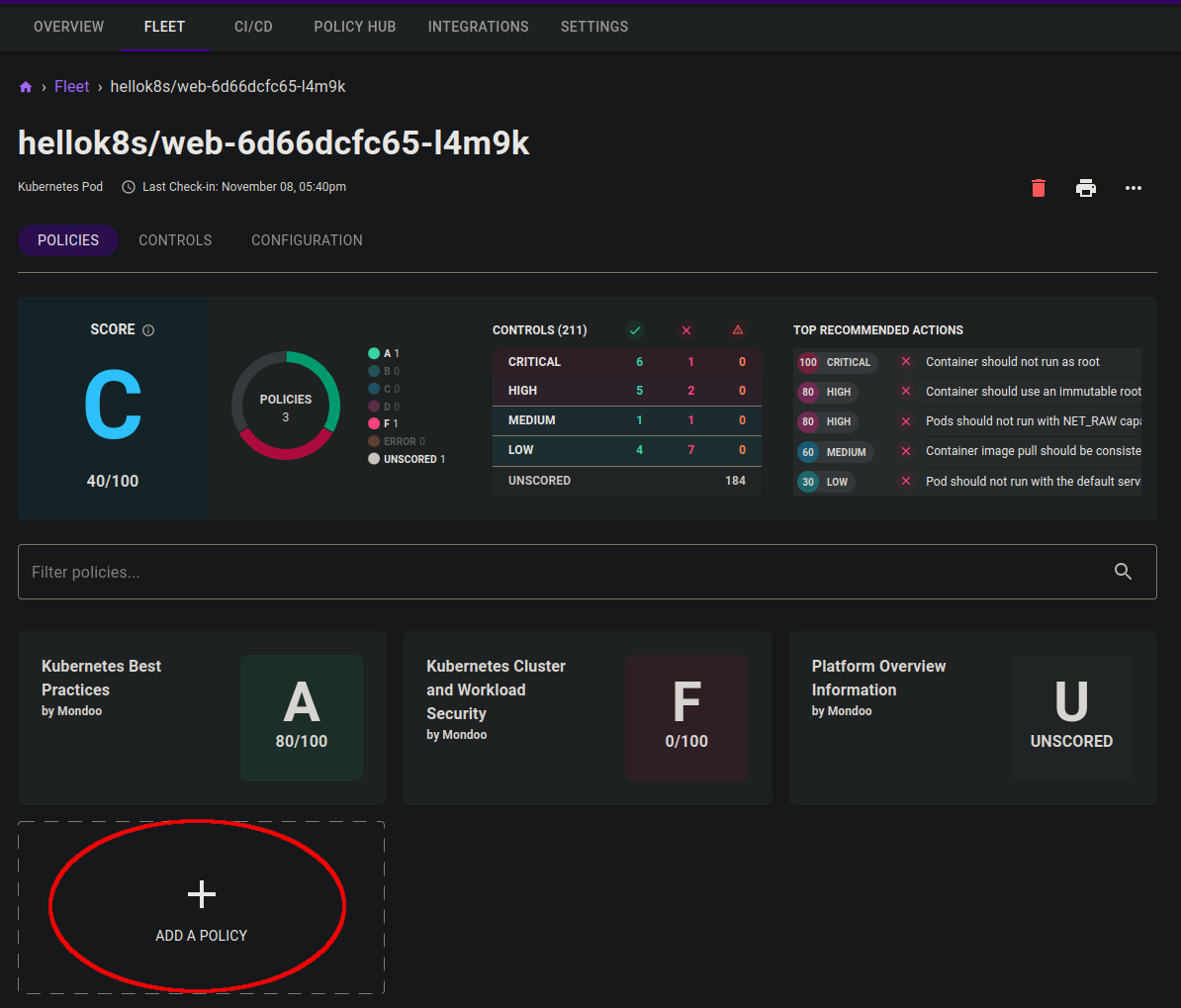
5. To enable the NSA policy for your cluster:
A. Select Add a Policy at the bottom of the page.
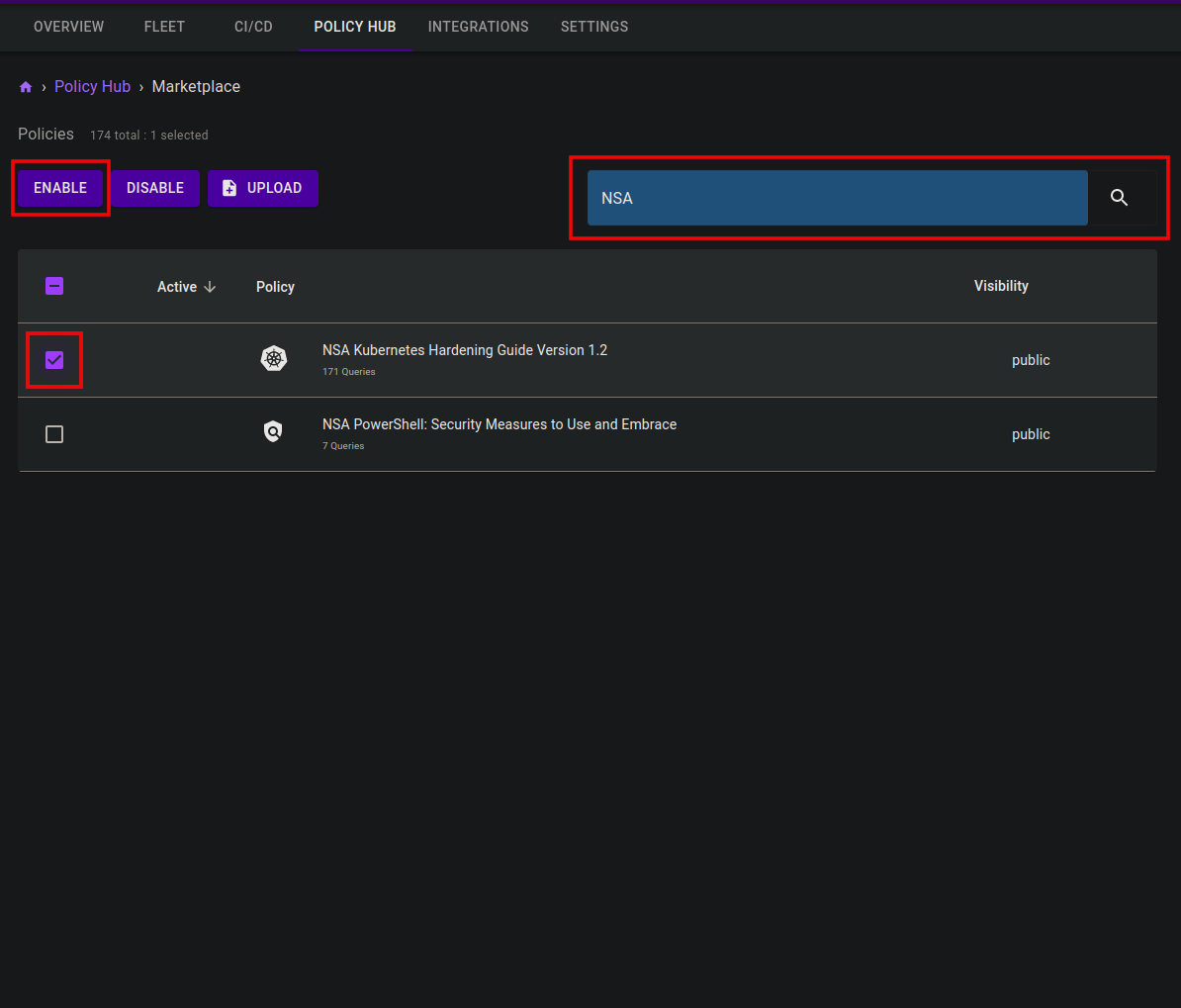
B. Use the search field to look up NSA Kubernetes Hardening Guide Version 1.2.
C. Check the box beside the policy and then select the Enable button to activate the policy.
6. Repeat the scan from your CLI:
$ cnspec scan k8s
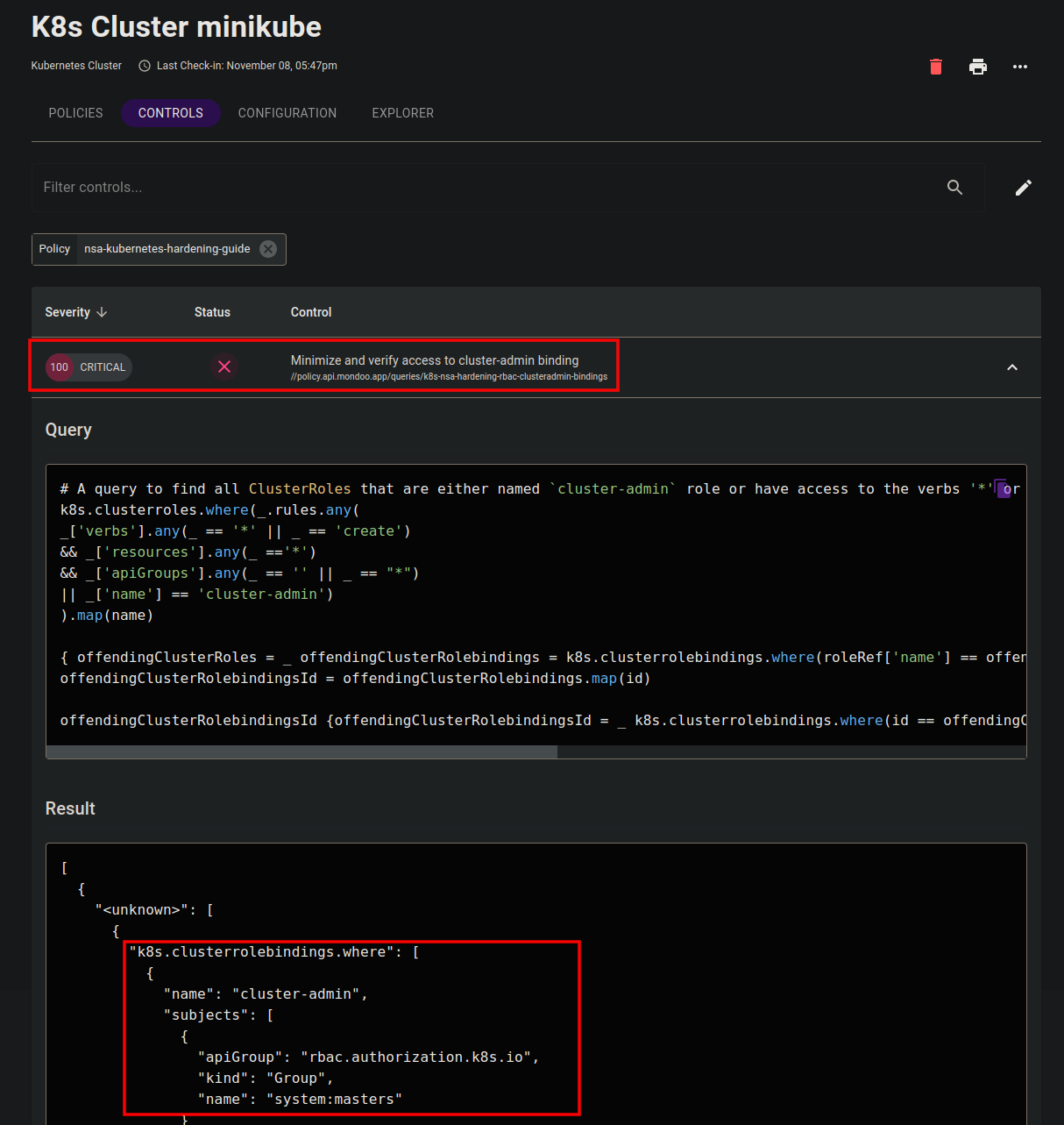
7. On the Mondoo Console, go to the Policy Hub and select the NSA Kubernetes Hardening Guide Version 1.2 policy to see the results of your scan. You can see the results either per query or per asset.
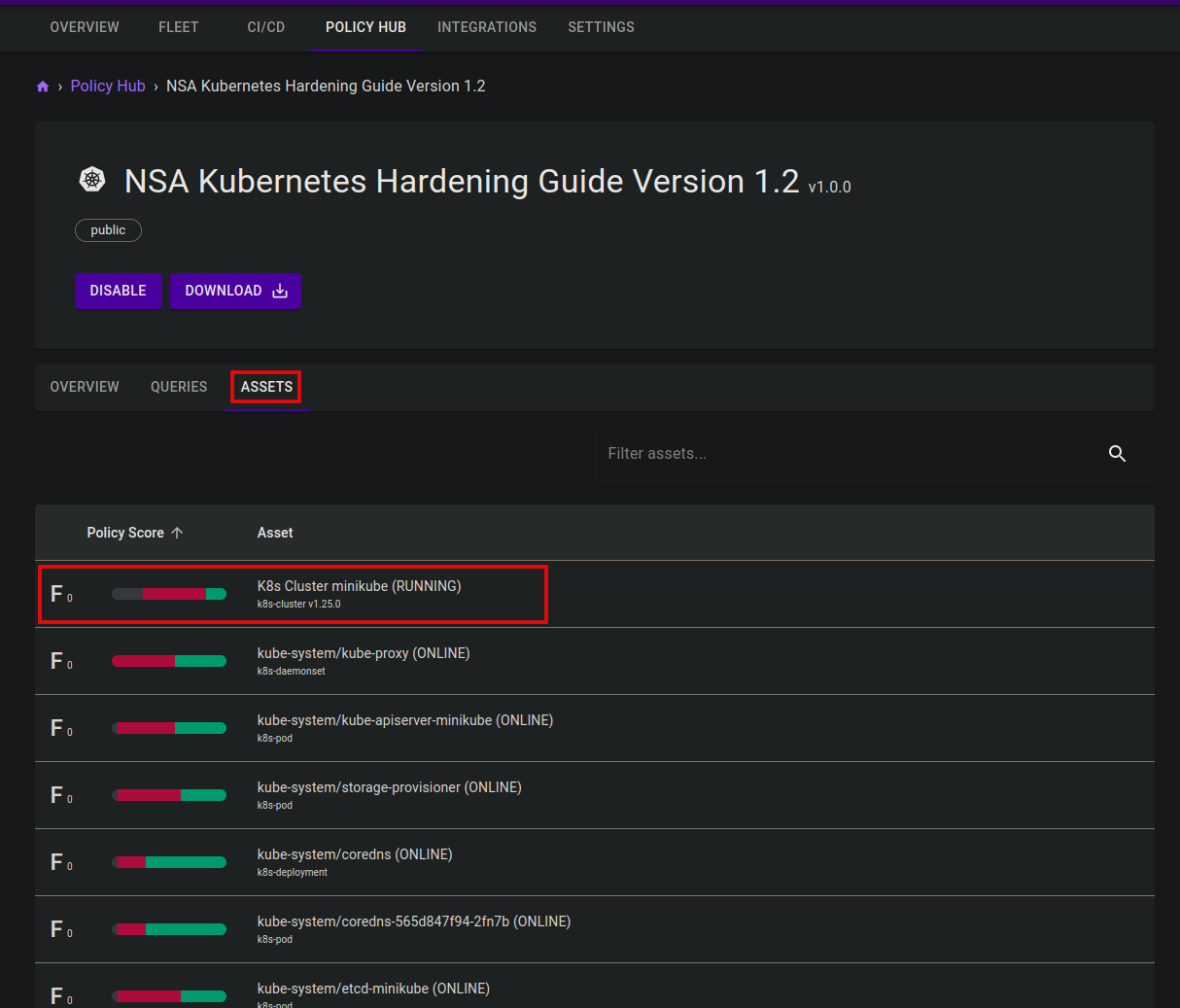
For example select the K8s Cluster minikube and get the results of all checks against that resource in detail.
Learn more about adding policies in Managing and Customizing Policies.
Use cnspec
Mondoo’s open source security testing tool, cnspec, allows you to quickly gather information about installed packages on your Kubernetes clusters.
If you have not yet installed cnspec, follow our instructions.
1. Make sure that you can connect to the Kubernetes cluster using your CLI:
$ kubectl get namespaces
2. Change the directory to the path where you policy is located and enter this command to run the NSA policy locally on your Kubernetes cluster:
$ cnspec scan k8s --policy-bundle nsa-kubernetes-hardening.yaml
3. To run against only certain components of the cluster, use this command with the --discover flag:
$ cnspec scan k8s --discover clusters --policy-bundle nsa-kubernetes-hardening.yaml
$ cnspec scan k8s --discover pods --policy-bundle nsa-kubernetes-hardening.yaml
4. To toggle full output, use the -o full flag.
$ cnspec scan k8s --policy-bundle nsa-kubernetes-hardening.yaml -o full
Prevent false positives
Because every system is unique, Mondoo accommodates different definitions of secure and insecure configurations. The scope of the NSA Kubernetes Hardening Guide Version 1.2” Policy by Mondoo in its default configuration is broad. We prefer to catch as many potentially harmful settings and objects as possible rather than to miss any. This approach often yields at least some false positives, which you can address.
Let's suppose that, after running the policy, you found a ClusterAdminBinding that looks suspicious at first, but is perfectly fine and actually needed. No problem!
See our guide on how to use policy props to avoid false positives. We explain how to individualize your Mondoo scans for your unique business security needs.
Note
The NSA Kubernetes Hardening Guide policy is only available to those who sign up with Mondoo.
But if you want to scan your Kubernetes cluster without a Mondoo account, you can use our open source cnspec policies, which also cover many common Kubernetes security issues:
mondoo-kubernetes-best-practices.mql.yaml
mondoo-kubernetes-security.mql.yaml
Links
cnspec policies:
- https://github.com/mondoohq/cnspec-policies/blob/main/core/mondoo-kubernetes-best-practices.mql.yaml
- https://github.com/mondoohq/cnspec-policies/blob/main/core/mondoo-kubernetes-security.mql.yaml
Documentation on the Kubernetes resource pack:





