
Canonical recently released their latest long-term support (LTS) version of Ubuntu with Ubuntu 22.04 codenamed Jammy Jellyfish. Ubuntu ships an LTS release every two years in April and supports them for a full five years (instead of the usual 18-month support cycles). This extended support cycle makes LTS releases ideal for servers. What exactly is new in Ubuntu 22.04, though? There are plenty of articles showing the latest logos, desktop backgrounds, and display drivers, but nothing that really informs sysadmins.
(Ubuntu 22.10 Server security features are reviewed here.)
Part of security is understanding the impact new technologies have on safeguarding your infrastructure. To help, we’re going to dive deep into some of the great new security features you’ll find when upgrading your systems from Ubuntu 20.04 to 22.04. We’ll also show how you can quickly and easily scan your new system with Mondoo to identify even more opportunities to secure your infrastructure.
Sudo 1.9
It’s only appropriate to start with every sysadmin’s favorite command: sudo! sudo has received many new enhancements to improve your infrastructure security. Perhaps the best new feature for clumsy sysadmins like me is improved configuration parsing and error handling. A simple typo in your sudo configs will no longer result in sudo breaking completely. Instead, sudo will skip over faulty config lines, leaving you with a working system.
There have also been several great logging improvements in sudo 1.9. sudo’s default logging system can now output data in JSON format for easier parsing with popular log parsing tools. There’s also an entirely new logging daemon, sudo_logsrvd, that provides secure, centralized logging specifically for sudo. Systems securely communicate with the daemon using TLS, and you can even use the sudoreplay CLI tool to view a real-time recreation of each command typed in the sudo session.
If you’d like to extend sudo, there’s now support for writing plugins in Python 4 instead of just C. There are also two new types of plugins: audit and approval plugins. This makes it easier to write custom audit/approval workflow processes that match your business needs, tied directly into the sudo CLI.
OpenSSH 8.9
Like sudo, OpenSSH is one of those technologies sysadmins live by, and it’s received some very big security updates with OpenSSH 8.9 in Ubuntu 22.04. First off, there have been several updates to the out-of-the-box algorithms. RSA signatures using the insecure SHA-1 hash are now disabled by default, and a new hybrid Streamlined NTRU Prime + x25519 key exchange method has been added. This new standard, designed to protect against future quantum computing key attacks, will become the default key exchange method in OpenSSH 9.0. OpenSSH will now also prefer ED25519 host signatures over the traditional ECDSA signatures.
OpenSSH 8.9 also starts the process of removing the legacy SCP protocol. Don’t worry, though: you’ll still be able to SCP files between hosts. But instead of SCP, the command will utilize the SFTP protocol. You can opt into SFTP-based SCP transfers with a new scp -s flag for now, but OpenSSH 9.0 removes support for the legacy SCP protocol entirely.
Host key checking and updating have both seen significant new changes as well. The often frustrating CheckHostIP configuration is now disabled by default since it didn’t provide enough protection and made key rotation difficult. The UpdateHostkeys configuration option is now enabled by default, allowing sshd to provide additional trusted keys to clients after authentication. This automates one of the trickier parts of key management and hopefully paves the way for seamless key rotation in the future.
Last but not least, multi-factor authentication in OpenSSH took a giant leap forward with much-improved FIDO support. OpenSSH now supports FIDO devices with a pin and supports the web-based FIDO standard as well. To further protect resident keys OpenSSH also implements FIDO 2.1’s credProtect extension.
Bash 5.1
It might seem silly to include bash in a list of security updates, but bash 5.1 includes a great new feature for scripters concerned about security. A new SRANDOM environment variable provides secure random numbers from the system’s entropy engine instead of the existing RANDOM variable, which wasn’t so random after all.
OpenSSL 3
Ubuntu 22.04 is one of the first major Linux distributions to ship with the new OpenSSL 3 release. This release has been in development for the last three years and includes large-scale changes to the project structure that should make it easier to maintain and interface with.
One of the most exciting features in OpenSSL 3 is the built-in validated FIPS 140-2 module. The previous FIPS implementation was not built directly into the OpenSSL codebase and only worked with the now EOL OpenSSL 1.0.2. Ubuntu previously offered a custom implementation built on OpenSSL 1.1.1, requiring costly Ubuntu Advantage (UA) subscriptions.
OpenSSL 3 also uses the Linux kernel’s cryptographic APIs for some of its TLS operations. This results in improved performance and allows the use of hardware accelerator cards. This could be potentially interesting in the future to offload TLS work from web servers or load balancers.
Lastly, it wouldn’t be a new OpenSSL release without a large number of new supported algorithms:
- KDF algorithms
SINGLE STEPandSSH - MAC algorithms
GMACandKMAC - KEM algorithm
RSASVEand Cipher AlgorithmAES-SIV - New schema support for PKCS#7 and PKCS#12
- New PKCS signature verification algorithm support
LUKS2 Disk Encryption Support
Ubuntu 22.04 extends the previous Linux Unified Key Setup-on-disk-format (LUKS) support to include the new LUKS2 standard. LUKS allows users to encrypt an entire disk at the block level, protecting data if drives or entire systems are stolen. LUKS2 includes many important updates to the format, such as:
- An increase in the number of decryption keys that can be stored from 8 to 32
- An improved encryption method that is more difficult to crack
- New external token plugins capability so vendors can write authentication plugins for volume decryption
- Online disk LUKS to LUKS2 migration support
Nftables replaces iptables
This change may come as a shock to some sysadmins, but Ubuntu 22.04 replaces the venerable iptables with nftables as the default system firewall. Iptables was introduced back in 1998 and modernized how firewalls worked on Linux systems, but it’s time again for a leap forward. The nftables subsystem in the Linux kernel was introduced in Linux Kernel 3.13 way back in 2014 and has matured and stabilized since then. This new framework greatly improves performance on today’s high-speed interconnects and removes the need for separate firewall software stacks for ARP, IPv4, and IPV6. If you have existing iptables rules, you’ll want to read the nftpables wiki page Moving from iptables to nftables.
Linux Kernel 5.15
One of the most significant changes between Ubuntu 20.04 and 22.04 is Linux kernel 5.15, with hundreds of thousands of commits taking place over the last two years. Below are some of the largest and potentially impactful security changes between kernel 5.5 and 5.15. Keep in mind that Ubuntu allows you to update to newer non-LTS kernels. Many cloud vendors update their images with the later kernels as well. It’s possible that your Ubuntu 20.04 system is already running the 5.15 kernel if you’ve built or rebooted it recently.
CPU-Specific Changes
- Support for Intel’s Software Guard Extensions (SGX) system allows applications to write data to secure enclaves that are hardware protected. This is ideal for storing sensitive data such as encryption or authorization keys. See the Intel SGX page for more information.
- Improvements for use with AMD’s Secure Encryption Virtualization (SEV) system support encrypting virtualized guest registers so they cannot be read by the host (or other guests). See the AMD SEV Page for more information.
Memory Access
- Support for randomizing the stack address offset in each syscall. See the Phoronix article for more information on enabling this feature.
- New Kernel Concurrency Sanitizer (KCSAN) for detecting data races using compile-time memory access instrumentation supported in both GCC and Clang. See the kernel.org documentation for more details.
Process Isolation
- New Landlock Linux Security Module allows process sandboxing by allowing processes to self-impose additional restrictions on top of those set at the system level. See the Landlock Linux Kernel Documentation for more information.
Filesystems
- Google’s fscrypt project for hardware-accelerated full disk encryption on f2fs and ext4 filesystems was merged
- The CIFS filesystem module no longer supports the weak LANMAN and NTLM protocols used by SMBv1.
- NTFS support is now built-in, eliminating the need for 3rd party user-space NTFS drivers
SELinux
- Improved SELinux performance with context caching
- A new data structure cuts in half the policy disk space
Samba 4.15
While Samba is not an out-of-the box component on Ubuntu systems, it’s commonly used in organizations and has received a large number of security enhancements worth mentioning. Perhaps the most impactful change for some users is the removal of these insecure legacy protocols and algorithms:
- NT4 style domain controllers support
- SMBv1 and related legacy protocols
- DES encryption keys in Kerberos
- HEIM_WEAK_CRYPTO support
- Legacy Apple Filing Protocol (AFP) compatibility via vfs_netatalk module
Samba also removed legacy encryption and compression code from their codebase and instead now uses zlib and GnuTLS. This removed insecure compression and encryption code and greatly sped up SMB3 file transfers.
Those using Samba for more than just filesharing will be happy to see some improvements to account and client management. The net CLI includes a new net offlinejoin subcommand, allowing admins to pre-join systems before they can connect to domain controllers. The support for Group Policy on Ubuntu hosts has also been enhanced to allow setting sudoers and cron configurations with Group Policy.
Upgrading Systems
Ideally, we’d always provision new systems when a new operating system ships. But we don’t live in an ideal world. There always seem to be special snowflake servers, and reprovisioning user workstations impacts productivity. When we can’t provision fresh systems, we can always perform an upgrade using Canonical’s do-release-upgrade command:
# fully update and cleanup our existing 20.04 system
sudo apt-get update
sudo apt-get upgrade
sudo apt-get autoremove
# perform the upgrade
sudo apt-get install update-manager-core
sudo do-release-upgrade
How to further secure your system with hardening settings and Mondoo's security platform
In addition to the security updates that come with Ubuntu 22.04, there are further steps you can take to secure your system. One such step is applying hardening settings and ensuring that all critical packages are updated. You can use the open source cnspec tool from Mondoo and the Mondoo SaaS platform to scan and report on security best practices, package vulnerabilities, and CIS benchmarks. Mondoo is a hosted security platform that automates manual security processes for DevOps and security practitioners, helping users quickly find known vulnerabilities and misconfigurations.
How to scan your Ubuntu 22.04 system using Mondoo's cnspec
To scan your Ubuntu 22.04 system using Mondoo's cnspec tool, you will first need to install the cnspec package. You can do so by running the following command:
bash -c "$(curl -sSL https://install.mondoo.com/sh/cnspec)"Once cnspec is installed, you can scan your system for misconfigurations. For instance, you can perform a local scan by running the following command:
cnspec scan
cnspec can scan a range of things, from cloud accounts to Kubernetes clusters, as well as SaaS services such as MS365 or Google Workspace.
When you run a local scan, cnspec will generate a report highlighting the security status of your system. The report includes the list of controls that passed and failed, with their associated scores.
How to perform advanced security scanning with the Mondoo platform and cnspec
If you authenticate cnspec with the Mondoo Platform, the tool can perform additional checks, such as scanning packages for CVEs, and CIS and BSI compliance policies. Results of the scan will be stored on the Mondoo Platform for analysis.
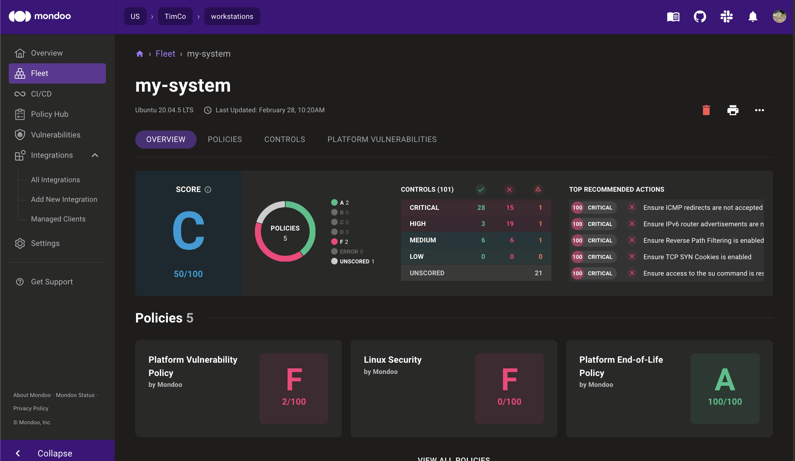
On the Mondoo platform console, you can view a high-level overview of the scan status of each policy and package vulnerability, as well as EOL data. For instance, you can check if the system is vulnerable to any known security threats, and see which packages need to be updated to ensure the best security practices.
Final Thoughts
If you're a sysadmin or security engineer, you know how tough it can be to keep up with all the security updates and patches required to protect your company's assets. But with the Mondoo platform, you can automate many of these tasks and stay on top of your security game. Plus, you'll have access to a community of like-minded professionals who can help you troubleshoot and share tips.
Don't waste any more time struggling with manual updates and outdated security protocols. Sign up for a free community account on Mondoo and see how easy security can be!


