-2.png?width=800&height=418&name=800x418%20blog%20feature%20images%20(4)-2.png)
The Zero Day Initiative issued on 22 December 2022 a new critical Linux Kernel vulnerability ZDI-22-1690.
What’s ksmbd and how does it relate to this Linux kernel vulnerability?
ksmbd is a Linux kernel component responsible for handling SMB (Server Message Block) protocol requests. SMB is a network protocol used for file sharing and printing between devices on a network.
ksmbd is used by the Linux kernel to handle incoming SMB requests and to perform the necessary actions to fulfill those requests. This can include reading or writing files, creating directories, or printing documents.
It is an essential component of the Linux kernel that plays a critical role in enabling file sharing and other network services on Linux-based systems.
What's this Linux kernel vulnerability about?
Linux Kernel ksmbd Use-After-Free Remote Code Execution Vulnerability is a security issue that was discovered in the Linux kernel in July 2022. The vulnerability, which is classified as a Use-After-Free Remote Code Execution vulnerability, allows an attacker to execute arbitrary code on a vulnerable system.
The vulnerability exists in the ksmbd component of the Linux kernel, which is responsible for handling SMB (Server Message Block) protocol requests. SMB is a network protocol used for file sharing and printing between devices on a network.
The vulnerability can be exploited by an attacker who can send a malicious SMB request to a vulnerable system. The system does not validate the existence of an object, which allows the attacker to execute their own code on the system. This can potentially allow the attacker to gain unauthorized access to the system.
Are your systems affected by this Linux kernel vulnerability?
Mondoo’s GraphQL-based query language, MQL, allows you to quickly gather information about installed packages on your assets, including container images, VMs, bare-metal servers… everything.
If you have not yet installed cnquery, follow our instructions. Once you've installed it, you can gather information about installed packages from your systems:
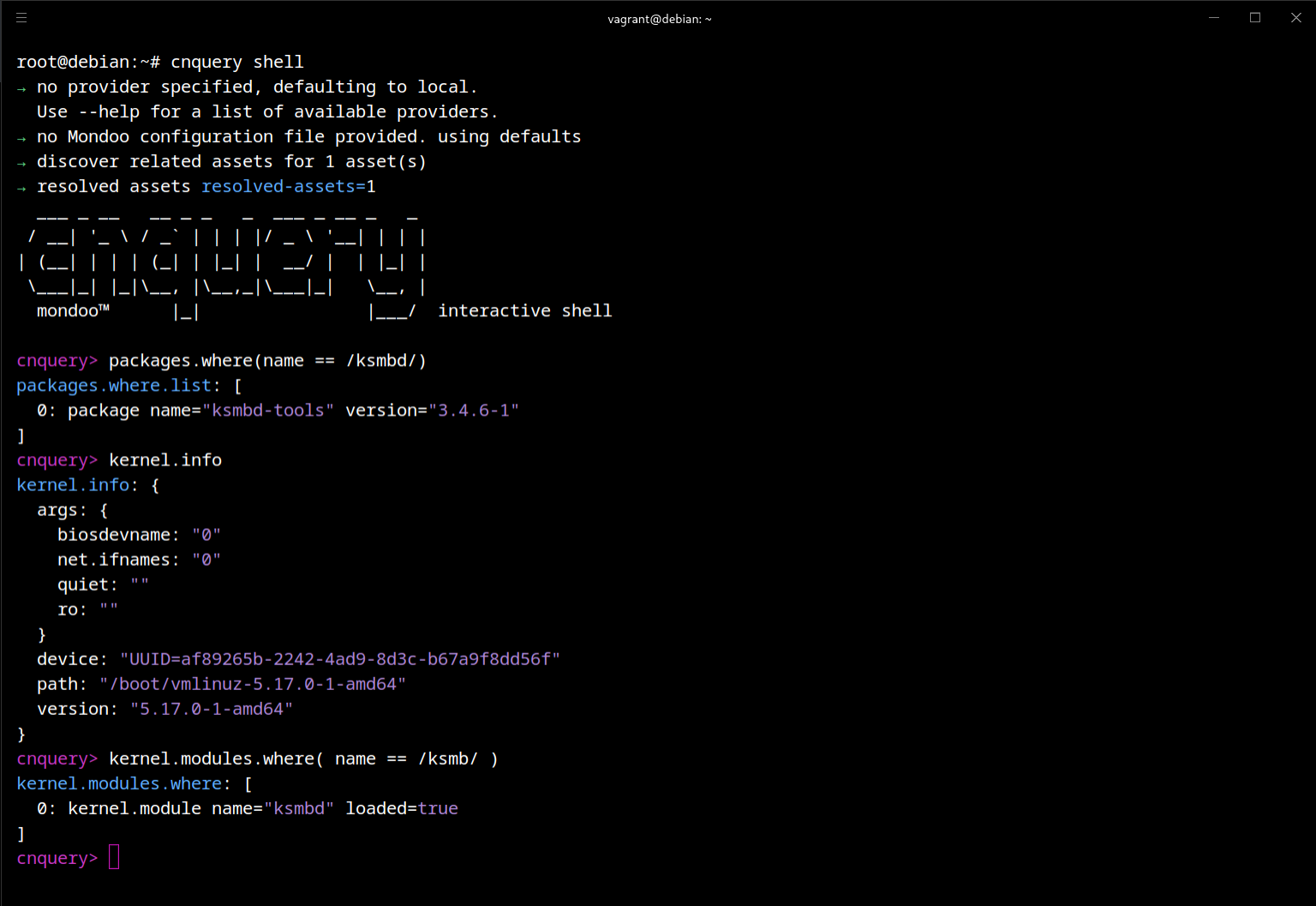
packages.where(name == /ksmbd/)Identify the running kernel version.
kernel.info
Identify if the ksmb kernel module is loaded.
kernel.modules.where( name == /ksmb/ )
Get the required information with cnquery to connect to your targets via ssh:
cnquery scan ssh vagrant@192.168.56.247 --ask-pass --querypack mondoo-linux-incident-response
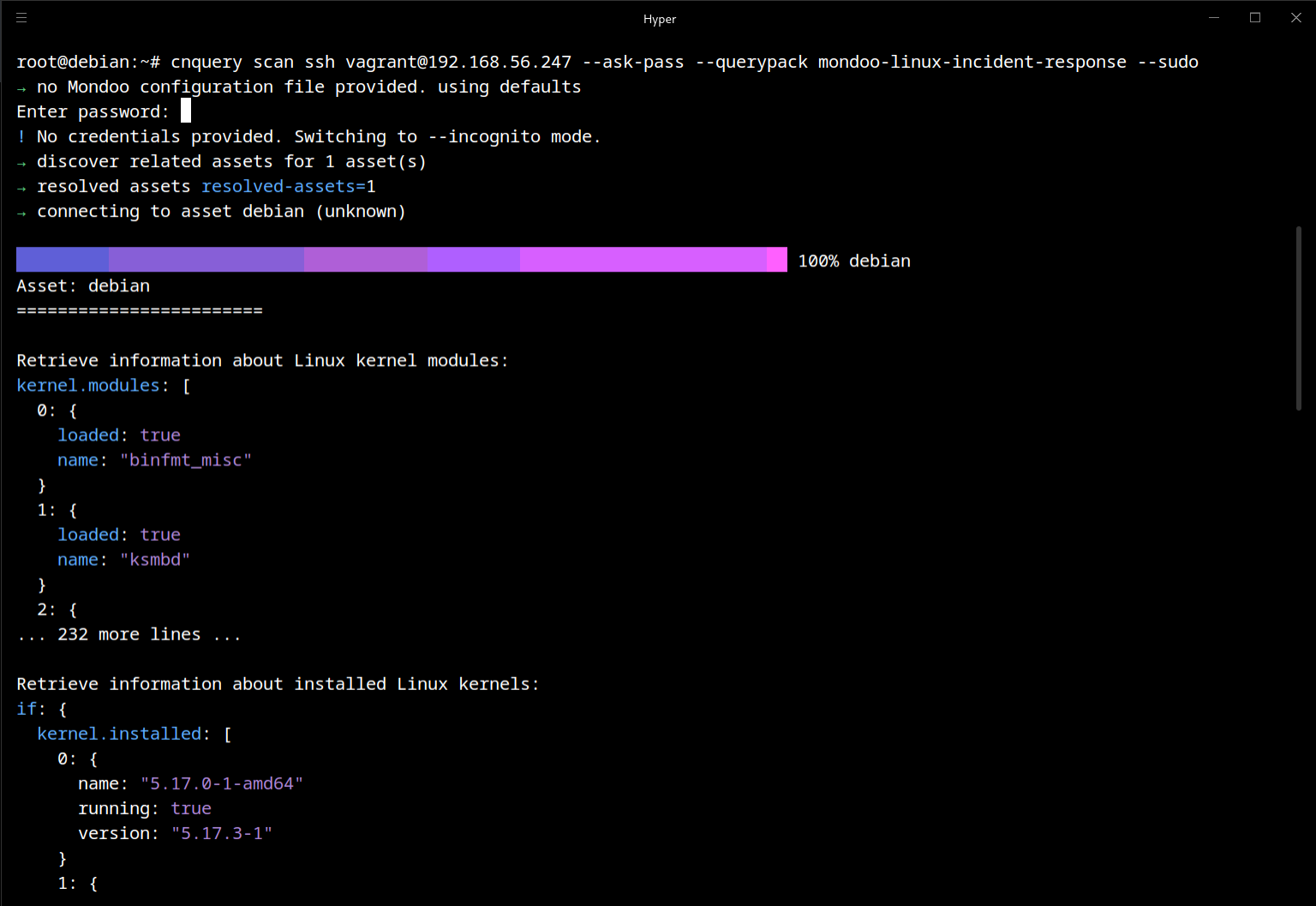
If ksmb kernel module is not loaded and the ksmbd package is not installed, then you are not affected by this vulnerability.
The vulnerability is fixed in kernel version 5.15.61, and most people are using the LTS (Long Term Stable) kernel version, and all issues reported by ZDI are fixed, the patches have been propagated to that kernel versions.



