-4.png?width=795&height=415&name=800x418%20blog%20feature%20images%20(4)-4.png)
With the new year starting, we have already a number of exciting updates for the new year! Before moving to the next major release in February, let's take a look at some of these new features:
Chapters
- See errors from the Kubernetes operator
- CLI migration and upcoming release
- Mondoo installation PowerShell module
- Policy linting
- MQL improvements
- Policy updates
- Other improvements
Dive deeper into GitHub
We've been busy improving nearly every aspect of the GitHub experience with cnspec, making it easier to apply out-of-the-box policy to secure your GitHub infrastructure and providing the resources and UI experience you need to create custom policies.
The GitHub Organization Security by Mondoo policy has been rewritten from the ground up to focus on critical security settings in your organization and repository. Existing queries focused on open source repository best practices have been removed and replaced with additional security queries to ensure settings like important branch protections are in place.
While building out this updates policy, we realized the various GitHub resources were missing important data necessary to write our out of the box policy and custom policies for your organizations. We made the following changes to improve the GitHub resources:
- github.repository resources now support repository stargazer counts, repo fork resolution, and support for repository issues.
- github.organization resource now includes avatar, followers and following data
- github.user resource is greatly expanded to help examine user accounts
- github.organization and github.user now support collecting information on gists
Finally, we improved the cnquery to make exploring your GitHub infrastructure easier. The cnquery shell github command now shows a list of repositories to examine, making it easier to find the repository you want to explore. We also added a new cnquery shell github user command allows you to examine details on GitHub users using the expanded github.user resource.
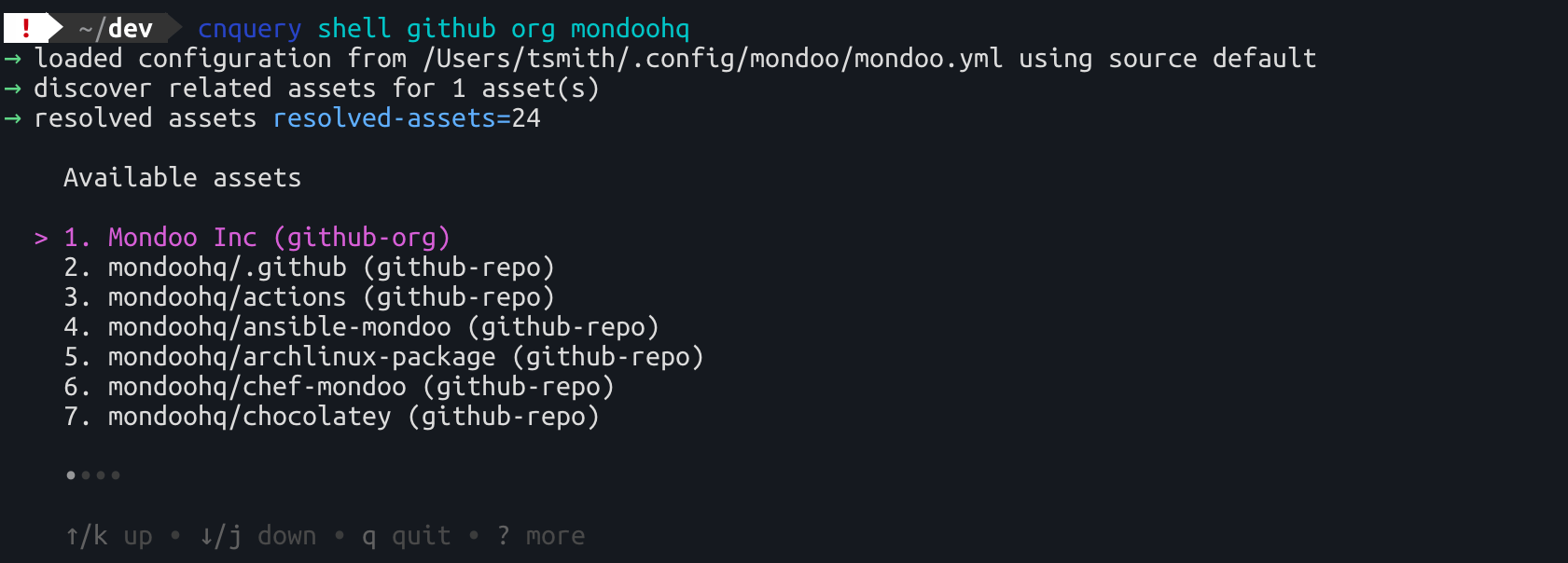
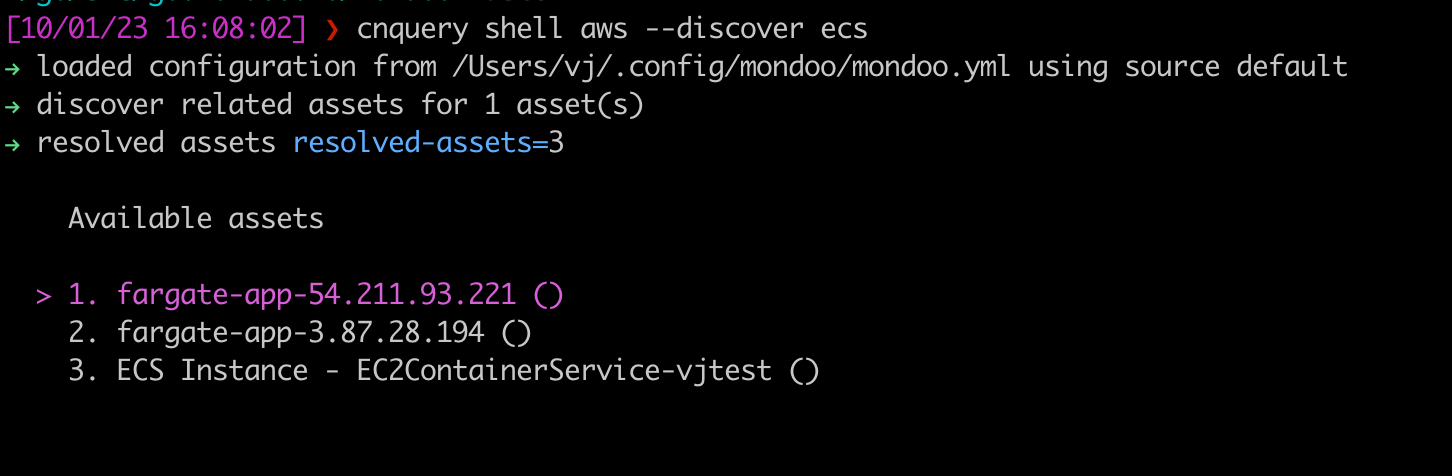
AWS ECS container scanning
You can now scan all AWS ECS containers when scanning your AWS account with a new --discover flag option, ecs. Use this flag with cnquery and cnspec to explore and secure ECS containers in your infrastructure.
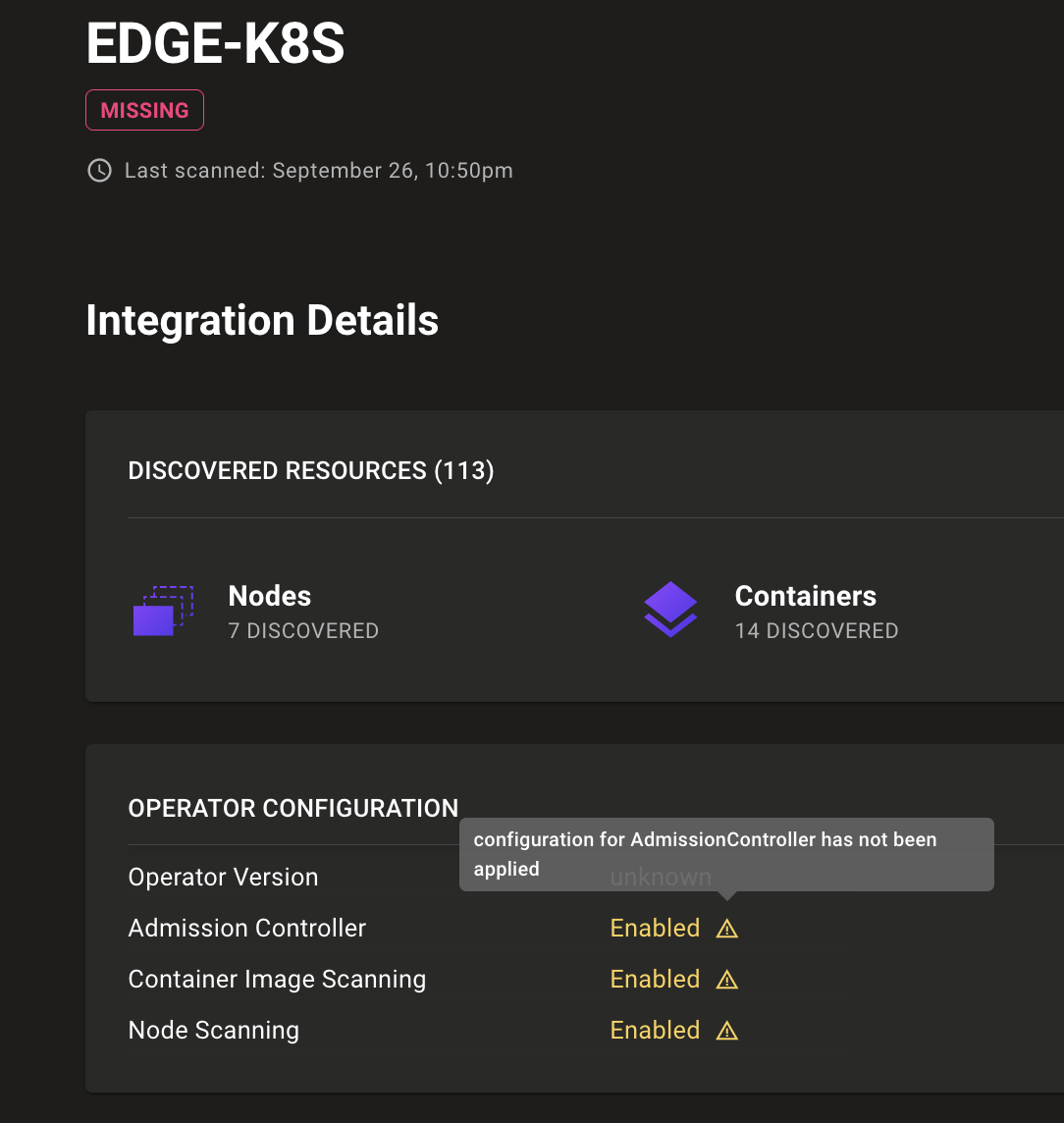
See errors from the Kubernetes operator
Kubernetes integration pages show any errors reported by the Mondoo Kubernetes Operator so you can more easily troubleshoot operator failures.
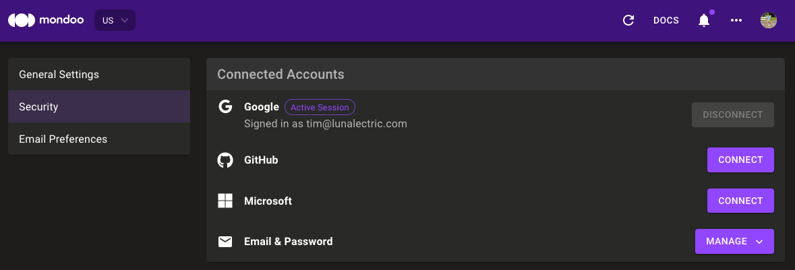
Multiple log-in methods in the Mondoo Console
Problem: Users who initially signed up with their email account had a hard time switching log-in methods after their account was created. Some prefer to sign in with their Google, Microsoft, or GitHub logins instead.
Solution: You can now add multiple authentication methods to your Mondoo Platform account, so you can log in with any combination of email, Microsoft, Google, or GitHub accounts.
To change your login method:
- In the top-right corner of the Mondoo Console, select your user icon.
- Select User Settings.
- In the left navigation, select Security. Under Connected Accounts, you can connect and disconnect accounts to upgrade your login methods.
CLI migration and upcoming release
Our migration from the legacy Mondoo CLI to cnspec continues this month with many components receiving updated instructions.
For example: CI integration examples in the console now show simpler cnspec steps, and the Mondoo Kubernetes Operator uses the new cnspec container images for all cluster scans.
February will mark the release of our next major release, which will finalize the migration of the Mondoo CLI to cnspec and slowly deprecate the old CLI. This migration is very straightforward, as the vast majority of commands behave exactly the same, while benefiting from further simplifications coming to cnspec.
Mondoo installation PowerShell module
Problem: You need to deploy trusted binaries from Mondoo to Windows hosts using Active Directory Group Policy or MDM solutions.
Solution: You can now install Mondoo using a new Mondoo.Installer signed PowerShell module that is published on the PowerShell Gallery at https://www.powershellgallery.com/packages/Mondoo.Installer/1.0. You can use this new signed module to deploy Mondoo CLIs to manage Windows hosts by running Install-Mondoo.
Install-Module -Name Mondoo.Installer
Install-MondooBecause our scripts and binaries are fully signed, the rollout of cnquery and cnspec was never easier. The module automatically validates if the latest version is already installed, or it updates to the newest version if required:
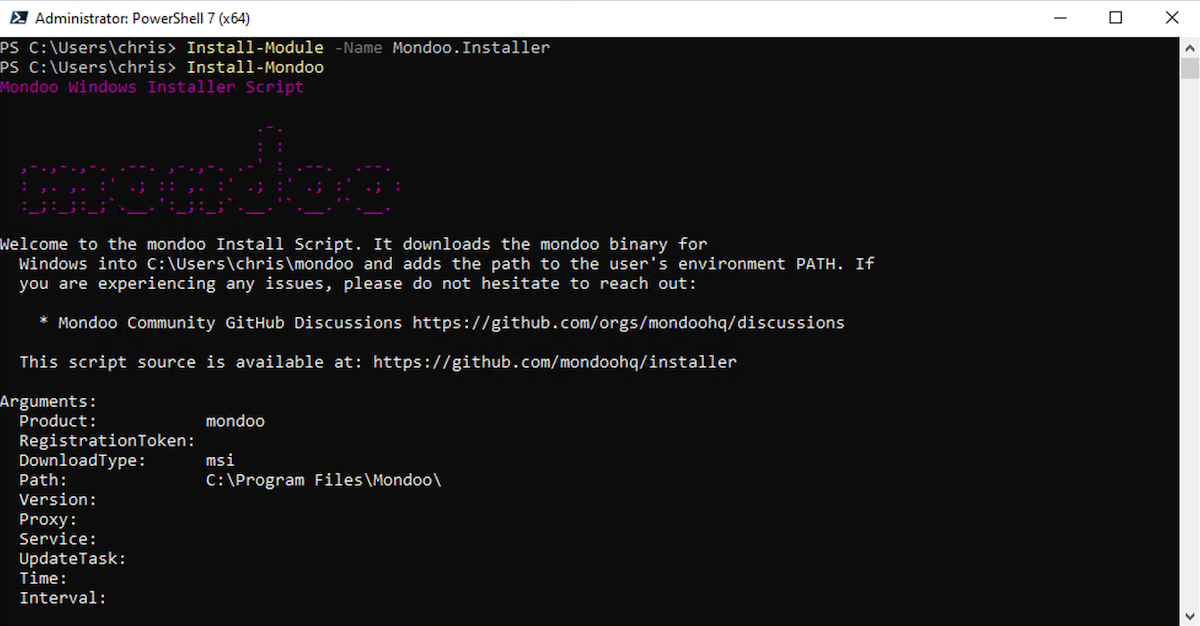
After the installation script is complete, cnquery and cnspec are available for use:

Run cnspec as a service
Problem: You want to move from the existing Mondoo client to the new and expanded cnspec client to scan your servers, but cnspec can't run as a service.
Solution: You can now run cnspec as a service to continuously scan servers and workstations. cnspec is our next-generation open source client with capabilities not found in the existing Mondoo command line interface (Mondoo Client). We highly recommend that you migrate your system to use this new and improved client as we begin the process of deprecating Mondoo Client.
After deploying the cnspec package to your systems, you can migrate to the cnspec service with the following commands on systemd-based Linux hosts:
systemctl stop cnspec.service systemctl disable cnspec.service systemctl enable cnspec.service systemctl start cnspec.service
Find out more about cnspec here.
Add cnquery/cnspec integrations
You can now set up cnquery and cnspec to communicate with Mondoo Platform directly on the Integrations page of the console.
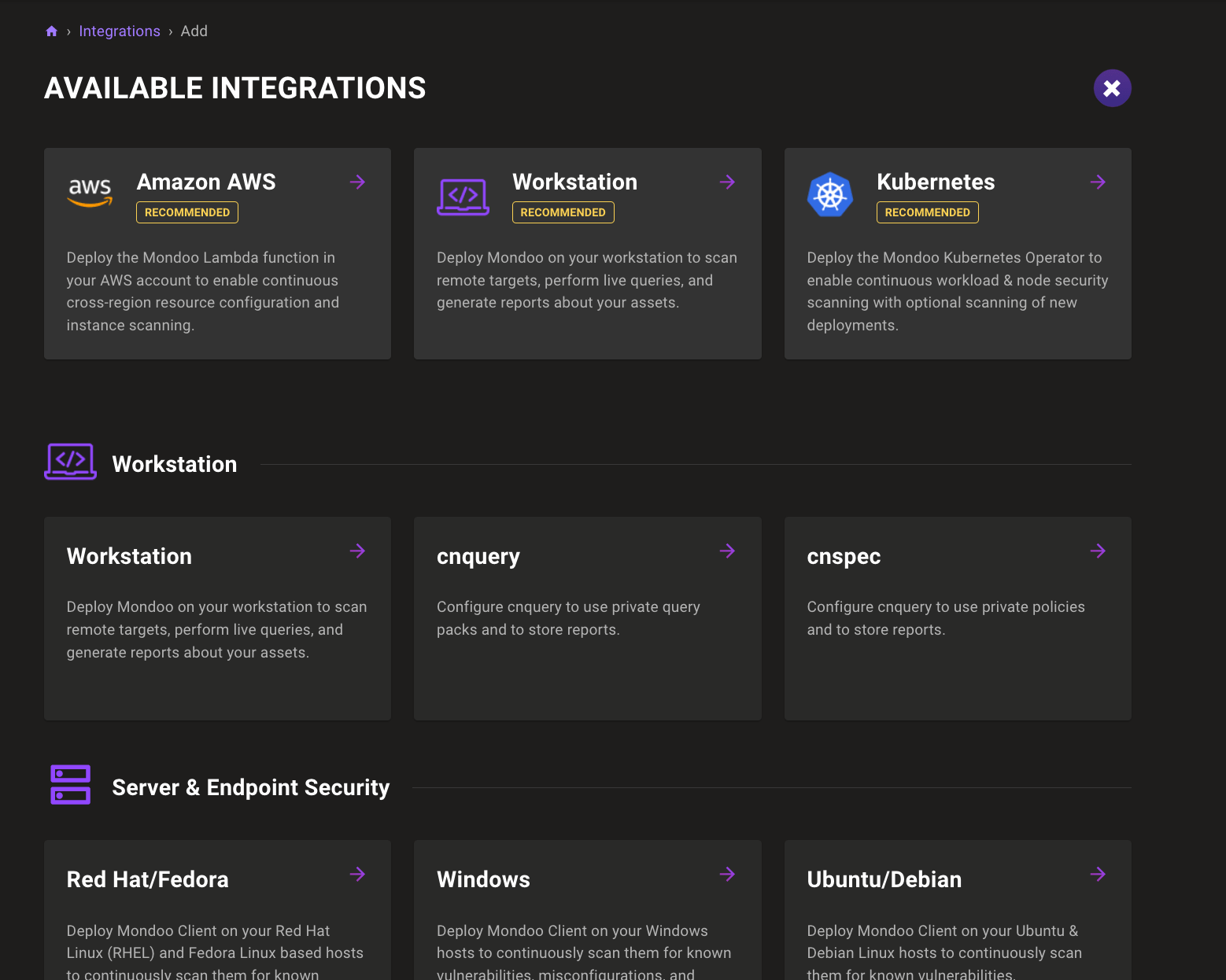
Asset counts on integrations
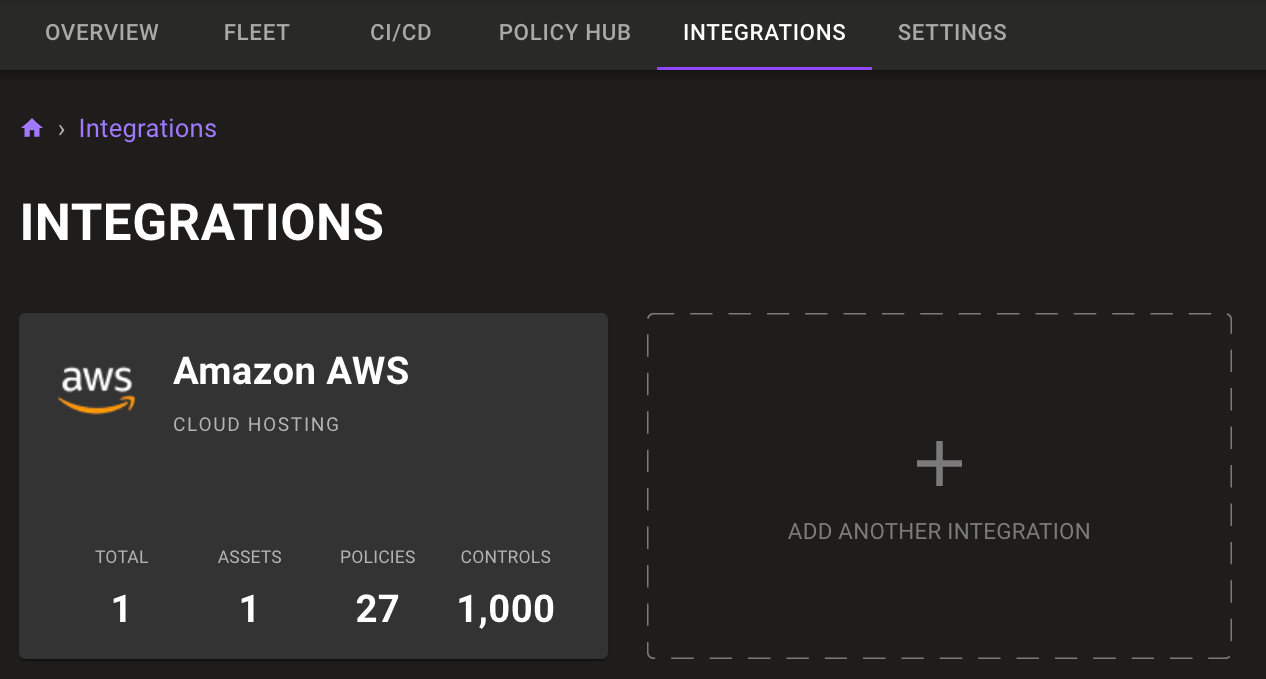
Integration tiles in the integration tab now show a summary of discovered assets, applied policies, and total applied controls. Now you can more easily see where assets are discovered.
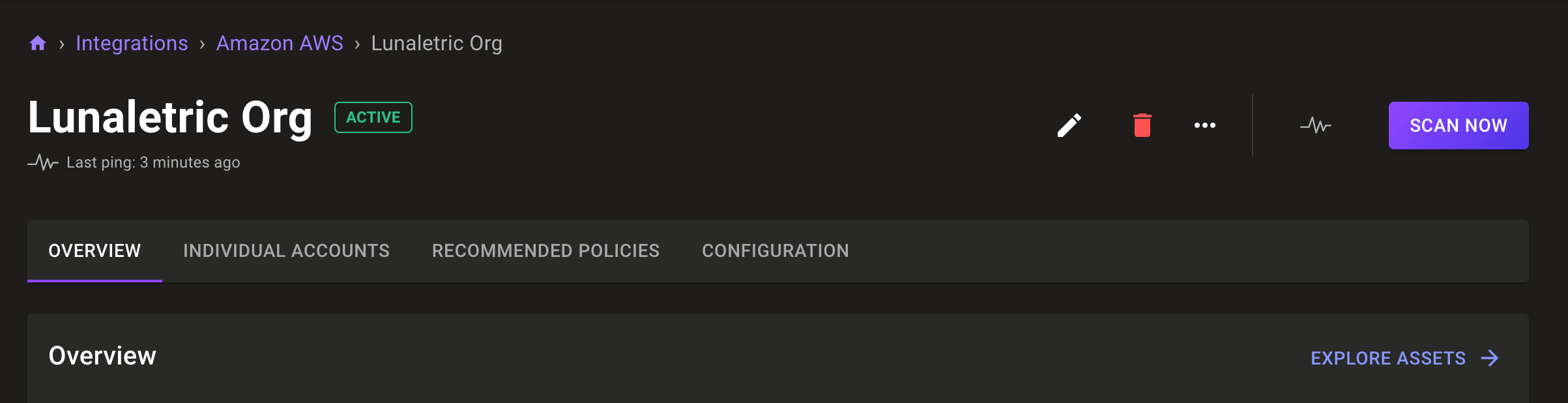
Trigger AWS integration scans directly in the console
Problem: Hassle free continuous scanning of your AWS accounts is great, but sometimes you need to trigger a scan to evaluate the current security state.
Solution: Now you can trigger a one time scan of your AWS account in the AWS Integration page.
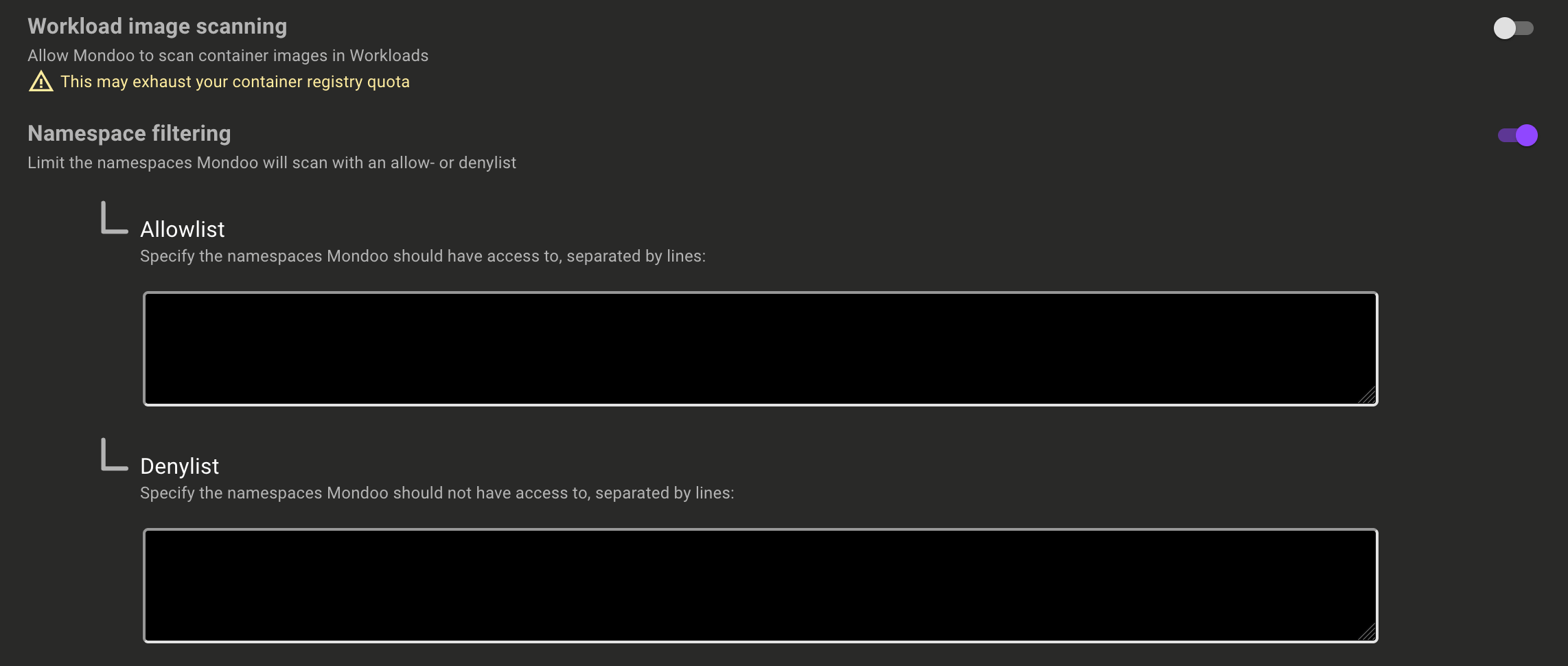
Filter namespaces to scan in the Kubernetes Operator
Problem: Different teams are responsible for different parts of a Kubernetes cluster and you need to control which namespaces the Mondoo Kubernetes Operator scans.
Solution: Mondoo now gives you more control over which namespaces are scanned by the Kubernetes Operator. Scan all namespaces, scan all namespaces except a list of specific namespaces, or take full control and only scan specified namespaces.
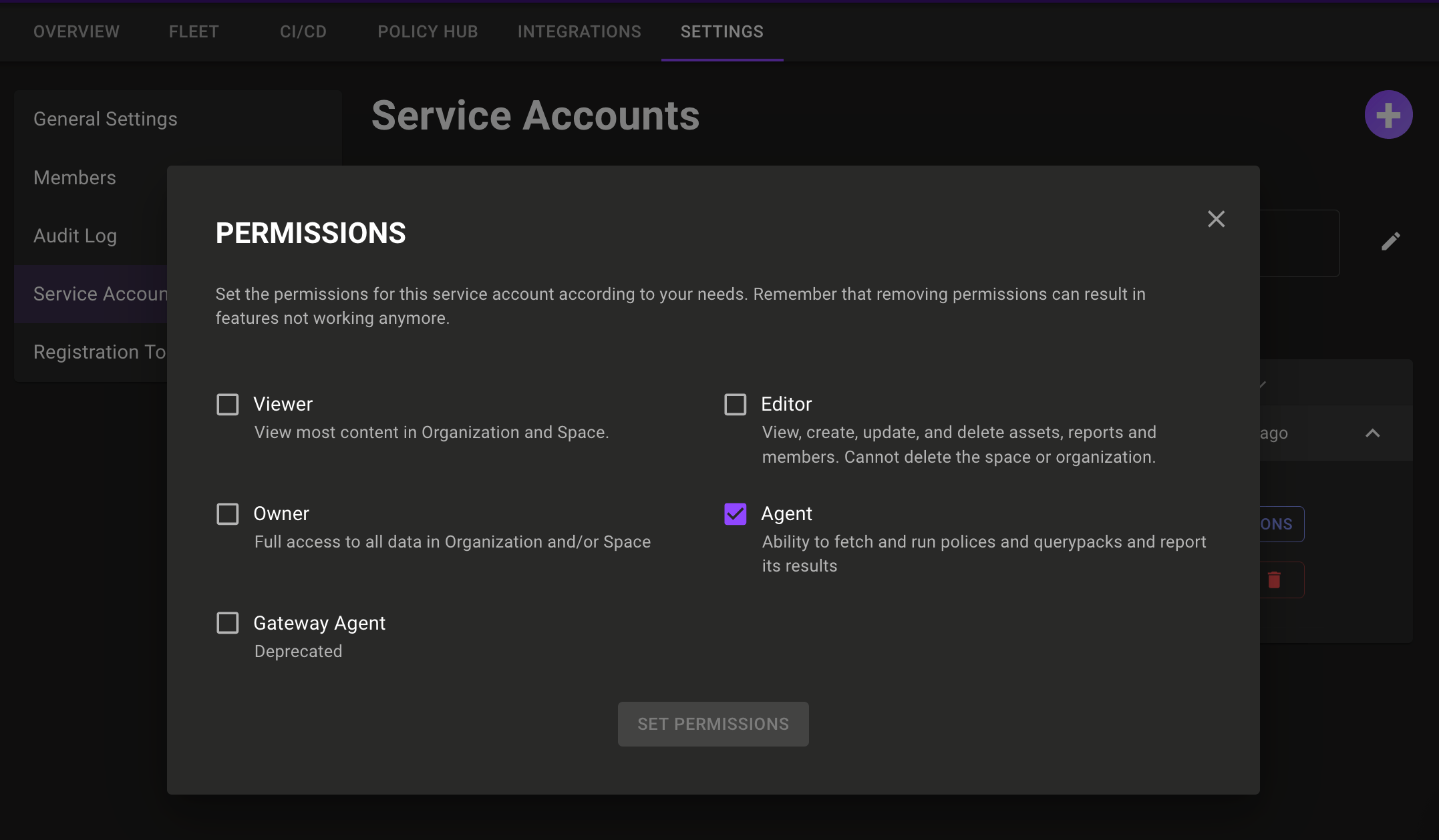
Multi-role service accounts
Problem: You need to set additional permissions for your service accounts, but you don't want to give unnecessary permissions by using the owner role.
Solution: You can now assign more than one role to a service account in the console to provide more fine grained permissions for service accounts. To set permissions on a service account select the Settings tab, select Service Accounts, select the account you wish to edit, and then select the Permissions button.
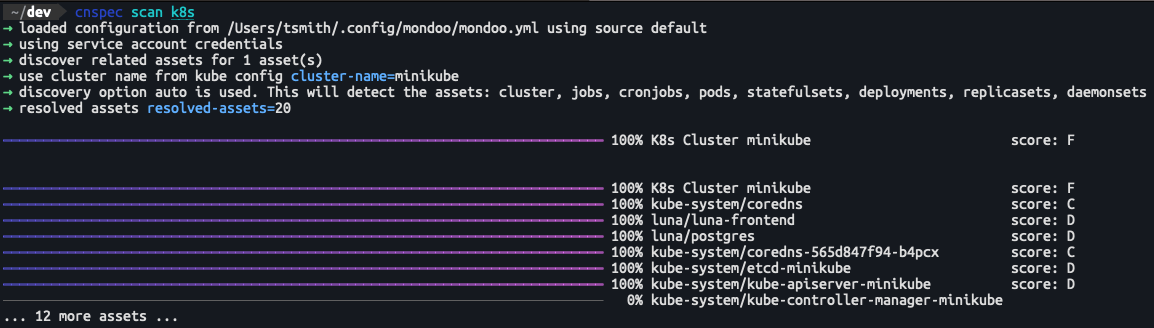
Multi-asset CLI scans
Problem: cnspec scan output gives you quick insight into the security posture of assets. However, when scanning complex systems like Kubernetes clusters with hundreds or thousands of assets, there is often too much data to consume.
Solution: We've developed an all-new summary view for asset scans that allows you to more easily understand the security posture of complex systems like Kubernetes in cnspec. We have also overhauled the progress reporting of these scans significantly.
An example screenshot for the scan progress:
An example scan of a small Kubernetes cluster:
Scanned 21 assets
Debian GNU/Linux 9 (stretch)
F index.docker.io/library/nginx@f7988fb6c02e
F index.docker.io/library/postgres@3f4441460029
Kubernetes Cluster
F K8s Cluster minikube
Kubernetes DaemonSet
D kube-system/kube-proxy
Kubernetes Deployment
C kube-system/coredns
D luna/luna-frontend
D luna/postgres
Kubernetes Pod
C kube-system/coredns-565d847f94-b4pcx
C kube-system/etcd-minikube
D kube-system/kube-apiserver-minikube
D kube-system/kube-controller-manager-minikube
D kube-system/kube-proxy-bqthk
D kube-system/kube-scheduler-minikube
D kube-system/storage-provisioner
D luna/luna-frontend-7fb96c846b-jjnhz
D luna/luna-frontend-7fb96c846b-tmg95
D luna/luna-frontend-7fb96c846b-xrl6c
D luna/postgres-5bb9d69b96-d9zzg
Kubernetes ReplicaSet
C kube-system/coredns-565d847f94
D luna/luna-frontend-7fb96c846b
D luna/postgres-5bb9d69b96
D luna/postgres-655d75f54b
Summary
=======
Score Distribution Asset Distribution
------------------ ------------------
A 0 assets Kubernetes ReplicaSet 4
B 5 assets Kubernetes Pod 11
C 4 assets Kubernetes DaemonSet 1
D 15 assets Kubernetes Cluster 1
F 3 assets Debian GNU/Linux 9 (stretch) 2
Kubernetes Deployment 3
For detailed output, run this scan with "-o full".
See more scan results and asset relationships on the Mondoo Console: https://console.mondoo.com/space/fleet?spaceId=...
Junit output format for cnspec
Problem: You want to run cnspec in your CI pipelines, but the output is hard to understand.
Solution: The cnspec CLI can now produce JUnit output on the CLI for integration with popular CI/CD platforms such as Jenkins or GitLab:
cnspec scan docker debian:10 --output junit > report.junit<?xml version="1.0" encoding="UTF-8"?>
<testsuites>
<testsuite name="Policy Report for debian:10@edcf96f9d9d9" tests="85" failures="43" errors="0" id="0" time="">
<testcase name="Ensure auditd is installed" classname="score">
<failure message="results do not match" type="fail"></failure>
</testcase>
<testcase name="Ensure no duplicate UIDs exist" classname="score"></testcase>
<testcase name="Ensure root group is empty" classname="score"></testcase>
<testcase name="Ensure no duplicate group names exist" classname="score"></testcase>
<testcase name="Ensure source routed packets are not accepted" classname="score">
<failure message="results do not match" type="fail"></failure>
</testcase>
...
<testcase name="Ensure login and logout events are collected" classname="score">
<failure message="results do not match" type="fail">
</testcase>
</testsuite>
</testsuites>
Expanded vault support for storing secrets
cnquery and cnspec now have expanded vault support for short-term secret storage when using inventory files. You can now store secrets with an in-memory vault or using GCP KMS encryption and GCP Cloud Storage through the Berglas project.
Example inventory file storing secrets with gcp-berglas:
apiVersion: v1
kind: Inventory
metadata:
name: inventory
spec:
assets:
- name: cool-stuff
connections:
- backend: 0
credentials:
- secret_id: storage/my-secrets/secret
type: 1
secret_encoding: 3
options:
discover:
targets:
- all
vault:
name: gcp-berglas
type: gcp-berglas
options:
project_id: id
Store GCP service account in an inventory file vault
Problem: You want to use an inventory file to store a set of GCP assets to scan, but you don't want to insecurely store credentials in the yaml config.
Solution: You can now store your GCP service account data in a secure inventory vault so you can share inventory files without worrying about credentials. This example inventory file stores the credentials used to access GCP infrastructure using the GCP Berglas project.
apiVersion: v1
kind: Inventory
metadata:
name: inventory
spec:
assets:
- name: cool-stuff
connections:
- backend: 13
credentials:
- secret_id: storage/random-bucket2/foo
type: 1
secret_encoding: 3
options:
discover:
targets:
- auto
vault:
name: gcp-berglas
type: gcp-berglas
options:
project_id: mondoo-dev-262313You can then run this inventory on the CLI without passing credentials on the CLI or within env vars:
cnquery scan --inventory-file inv.yamlFine-grained control over Azure subscription scanning
You can now control particular Azure subscriptions to include or exclude during scans with new --subscriptions and --subscriptions-exclude flags. You can use these new flags to control which subscriptions you want to inspect. For example, to run the cnquery shell on all subscriptions except for two, you can exclude those subscriptions explicitly: cnquery shell azure --subscriptions-exclude=984df67f-fc2e-4ebf-80a2-1234567891011,1e829eb0-e6a3-4c7b-8212-1234567891011
Policy linting
Problem: Custom policies are incredibly flexible to test assets according to your preferences. However, they can become large and may contain errors or incorrect data, which can lead to unexpected results.
Solution: cnspec now includes a new cnspec bundle lint command that helps you find incorrectly formatted policies. This new command checks for the following conditions:
- MQL compile error
- UID is not valid
- Missing policy UID
- Missing policy name
- No unique policy UID
- Policy is missing checks
- Assigned query missing
- Policy version is missing
- Policy version is invalid
- Missing query UID
- Missing query title
- No unique query UID
- Unassigned query
- Missing filters
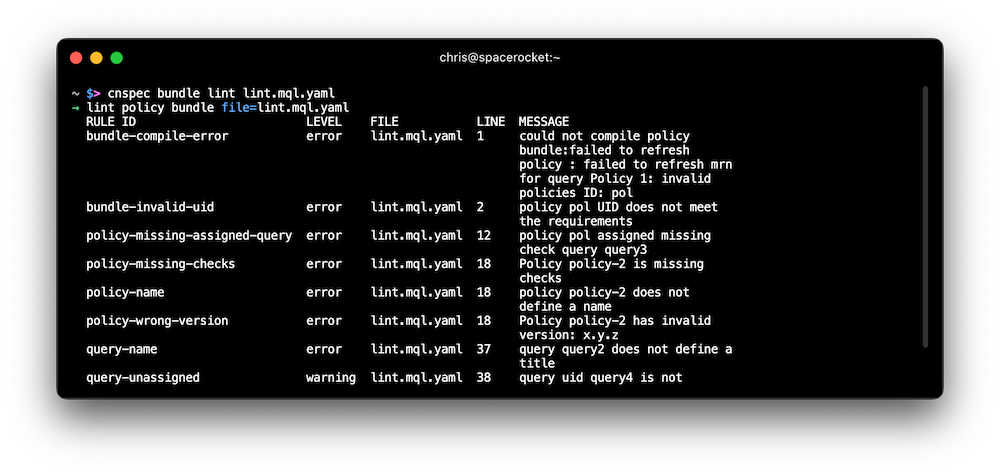 But wait, there's more! This new linting works with GitHub Code Scanning through our Mondoo GitHub Action. Applying the updated action scans your repository for Mondoo policies, annotates pull requests with any problems it finds, and even opens GitHub Code Scanning issues for problems.
But wait, there's more! This new linting works with GitHub Code Scanning through our Mondoo GitHub Action. Applying the updated action scans your repository for Mondoo policies, annotates pull requests with any problems it finds, and even opens GitHub Code Scanning issues for problems.
The action is compact and doesn't require a service account or any other additional setup:
---
name: Lint Policies
on:
pull_request:
push:
branches:
- main
jobs:
build:
runs-on: ubuntu-latest
steps:
- name: Checkout repository
uses: actions/checkout@v3
- name: Lint cnspec policies and output SARIF
uses: mondoohq/actions/cnspec-lint@main
with:
path: .
output-file: "results.sarif"
- name: Upload SARIF results file
uses: github/codeql-action/upload-sarif@v2
with:
sarif_file: results.sarifThis action scans each opened PR and merge, giving you annotations directly in the GitHub UI:
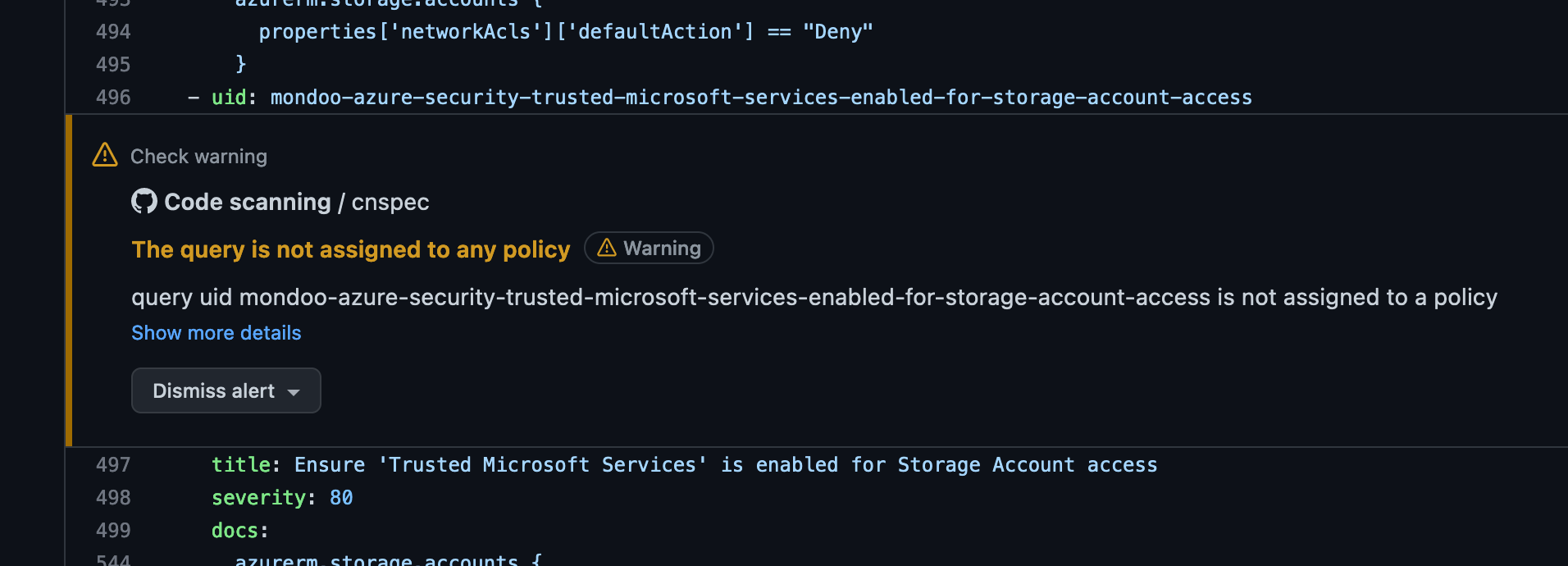
The GitHub Action integrates with GitHub Code Scanning to open GitHub Code Scanning issues for each problem in your policy:
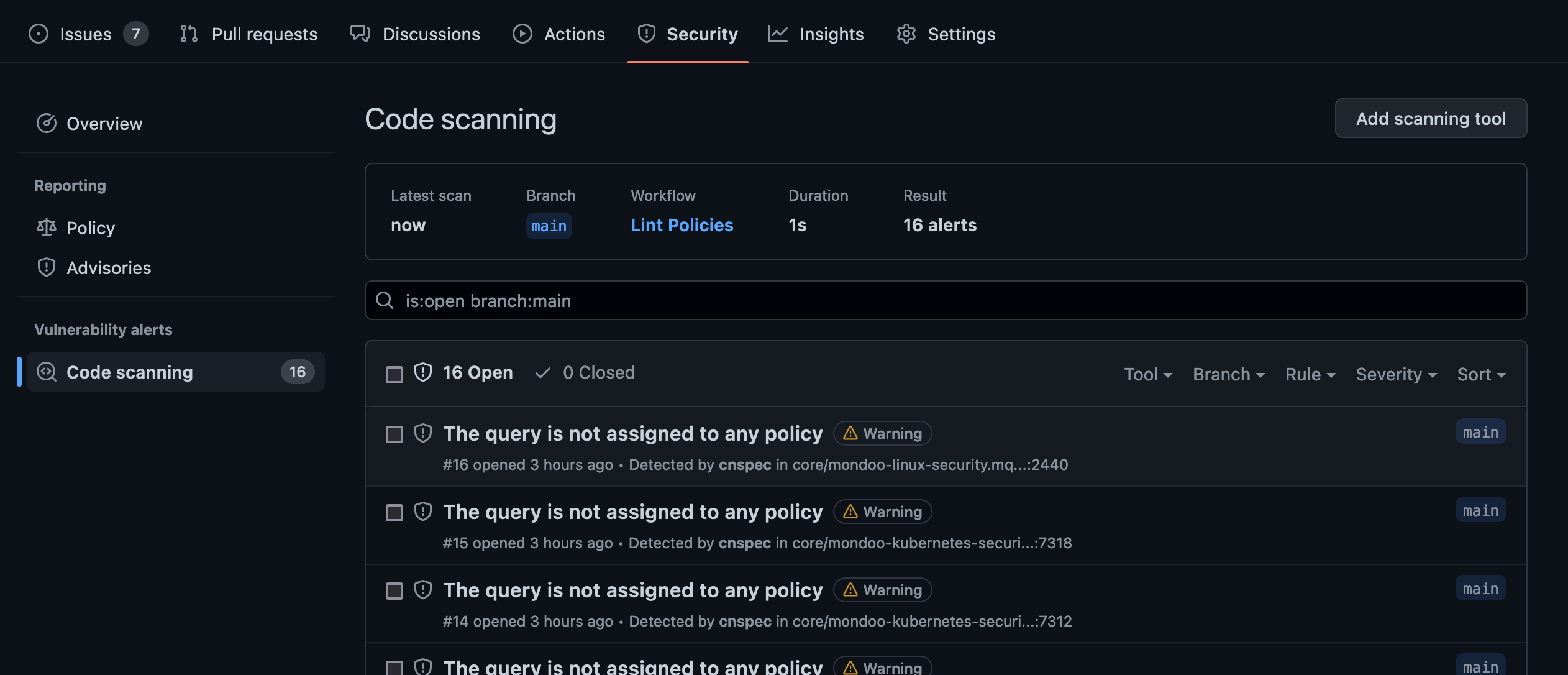
Policy updates
New CIS policies for GCP and Azure
Mondoo now includes the latest CIS benchmark policies for Azure, GCP, AWS, and VMware so you can secure the most complex multi-cloud and hybrid-cloud infrastructure. The CIS Microsoft Azure Foundations Benchmark policy is updated from 1.1.0 to 1.5.0, and the CIS Google Cloud Platform Foundation Benchmark is updated from 1.1.0 to 2.0.0. Both of these policies utilize the latest new resource shipped with new version of cnspec and include many new queries as well as audit and remediation steps for all queries.
New and updated CIS policies
Mondoo now includes the latest macOS and Linux CIS policies with new policies for the latest OS releases.
New CIS policies:
- CIS Red Hat Enterprise Linux 9 Benchmark 9 1.0
- CIS AlmaLinux OS 9 Benchmark 1.0
- CIS Rocky Linux 9 Benchmark 1.0
- CIS Oracle Linux 9 Benchmark 1.0
- CIS Apple macOS 13.0 Ventura Benchmark 1.0.0
Updated CIS policies:
- CIS CentOS Linux 8 Benchmark updated from 1.0.1 to 2.0.0
- CIS Oracle Linux 8 Benchmark updated from 1.0.1 to 2.0.0
- CIS SUSE Linux Enterprise 11 Benchmark updated from 2.0.0 to 2.1.1
- CIS Apple macOS 10.15 Catalina Benchmark updated from 2.1.0 to 3.0.0
- CIS Apple macOS 11.0 Big Sur Benchmark updated from 2.1.0 to 3.0.0
- CIS Apple macOS 12.0 Monterey updated from 1.1.0 to 2.0.0
Detect expiring certs in Kubernetes Ingresses
A new "Ingress certificates less than 15 days from expiration" query in the "Kubernetes Best Practices by Mondoo" policy detects certificates nearing their expiration data in your Kubernetes cluster. This query looks at all certificates defined in a Kubernetes Ingress resource that are stored as a Secret and fails when the expiration date is less than 15 days.
MQL improvements
Iterating over keys and values
MQL already supports accessing keys and values via key and value in maps:
> sshd.config.params.where( key == /p/ )
sshd.config.params.where: {
ChallengeResponseAuthentication: "no"
Ciphers: "aes256-ctr,aes192-ctr,aes128-ctr"
}
We extended this support to include parsed JSON and YAML structures:
> parse.json("my.json").params.where( value == 1 )
parse.json.params.where: {
apples: 1.000000
oranges: 1.000000
}
You can use these structures to quickly filter maps via key and value or to make assertions. For example you can ensure that certain keys exist:
> parse.json("my.json").params.where( key == /or/ )
parse.json.params.where: {
"hawthorn berries": 16.000000
oranges: 1.000000
}
New OpenPGP resource
You can now use new OpenPGP resources to access information about its keys and identities from MQL. This can be used to e.g. validate that repository signatures are still valid.
cnquery> parse.openpgp(path: "./expires.asc").all( identities.all( signatures.all( keyExpiresIn.days > 30 )))
[ok] value: true
Inspect OpenPGP keys with the following MQL query:
parse.openpgp(path: "./expires.asc") {
primaryPublicKey { * }
identities {
id
signatures { * }
}
}
Result from cnquery
cnquery> parse.openpgp(path: "./expires.asc") { primaryPublicKey { * } identities { id signatures { * } } }
parse.openpgp.list: [
0: {
primaryPublicKey: {
id: "7312FA356E7DB13F"
bitLength: 4096
version: 4
fingerprint: "07a453f8aea248e1e9b8eae27312fa356e7db13f"
keyAlgorithm: "rsa"
creationTime: 2023-01-14 17:24:58 +0100 CET
}
identities: [
0: {
id: "Test Expiration <test2@example.com>"
signatures: [
0: {
keyAlgorithm: "rsa"
version: 4
keyExpiresIn: 363 days 23 hours 43 minutes 5 seconds
identityName: "Test Expiration <test2@example.com>"
signatureType: "positive_cert"
hash: "SHA-256"
creationTime: 2023-01-14 17:24:58 +0100 CET
lifetimeSecs: -1
expiresIn: null
fingerprint: "07a453f8aea248e1e9b8eae27312fa356e7db13f"
keyLifetimeSecs: 31449568
}
]
}
]
}
]
Kubernetes Ingress resources
Mondoo now includes new resources for exploring and securing Kubernetes Ingress objects. New resources support exploring the Ingress objects themselves as well as the HTTP rules in each Ingress.
A few of the new resources are:
- k8s.ingress
- k8s.ingress.tls
- k8s.ingress.tls.certificates
Example cnspec shell query:
k8s.ingresses: [
0: {
annotations: {}
namespace: "default"
labels: {}
manifest: {
apiVersion: "networking.k8s.io/v1"
kind: "Ingress"
metadata: {
creationTimestamp: null
name: "no-tls-ingress"
namespace: "default"
}
spec: {
ingressClassName: "nginx"
rules: [
0: {
host: "api.nexus.info"
http: {
paths: [
0: {
backend: {
resource: {
apiGroup: "k8s.example.io"
kind: "MyKind"
name: "my-resource"
}
}
path: "/"
pathType: "Prefix"
}
]
}
}
...
New Azure resources
A comprehensive list of new resources for Microsoft's Azure have been added to MQL, including:
- NEW azure.cloudDefender
- NEW azure.sql.server.vulnerabilityassessment
- NEW azure.authorization.roleDefinition
- NEW azure.mysql.flexibleServer
- NEW storage account resources:
- azure.storage.account.queueService.properties
- azure.storage.account.blobService.properties
- azure.storage.account.tableService.properties
- azure.storage.account.dataProtection
- NEW azure.network.watcher.flowlog
- NEW Azure monitoring resources:
- azure.monitor.diagnosticSettings
- azure.monitor.activitylog
- NEW Azure CloudDefender resources:
- azure.cloudDefender.defenderForContainers
- azure.cloudDefender.defenderForServers
- NEW azure.resourceGroups resource
For more information, take a look at the Azure resource pack docs.
New GCP resources
cnquery and cnspec now include new resources for securing GCP, including:
- NEW Pub/Sub gcp.project.pubsub
- NEW KMS gcp.project.kms
- NEW API Keys gcp.project.apiKeys
- NEW essential contacts gcp.project.essentialContacts
- NEW logging gcp.project.logging
- NEW SQL gcp.project.sql
- NEW GCF gcp.project.cloudFunctions
- NEW CloudRun `gcp.project.cloudRun
- NEW Dataproc clusters gcp.project.dataproc.clusters
- NEW IAM service-accounts gcp.project.iam.serviceAccounts
- NEW compute backend services gcp.project.compute.backendServices
- NEW monitoring policies gcp.project.monitoring.alertPolicies
- gcp.compute.firewall now includes allowed and denied data
- gcp.compute.network now includes mode data
- gcp.project.clusters is now gcp.project.gke.clusters
- gcp.bigquery is now gcp.project.bigquery
- gcp.compute is now gcp.project.computeService
- gcp.dns is now gcp.project.dnsService
- gcp.storage is now gcp.project.storage
- gcp.project.compute.networks now includes subnetworks data
- gcp.project.computeService now includes confidentialInstanceConfig data
- gcp.project.dns.managedZones now includes dnssecConfig data
- gcp.project.kms.keyrings{cryptokeys{*}} now includes created, nextRotation, rotationPeriod, versionTemplate, labels, importOnly, destroyScheduledDuration, and cryptoKeyBackend data
- gcp.project now includes commonInstanceMetadata
- gcp.project.bigquery.datasets now includes access data
- gcp.organizations and gcp.projects now include accessApprovalSettings data
- gcp.project.kms.keyrings now includes cryptokeys
- gcp.project.dns.policies now includes network data
- gcp.project.logging.sinks now includes storageBucket data
- gcp.project.storage.buckets now includes retentionPolicy data
A few examples are listed below.
We added new resources to query GCP KMS Key Rings and their cryptographic keys:
cnquery> gcp.project.kms.keyrings { * }
gcp.project.kms.keyrings: [
0: {
resourcePath: "projects/example-project/locations/global/keyRings/testring"
created: 2022-12-19 15:17:46.974842182 +0000 UTC
projectId: "example-project"
cryptokeys: [
0: gcp.project.kmsService.keyring.cryptokey name="testring-key" purpose="ENCRYPT_DECRYPT"
]
name: "testring"
location: "global"
}
]
Inspect details for Crypto Keys:
cnquery> gcp.project.kms.keyrings { name cryptokeys { * } }
gcp.project.kms.keyrings: [
0: {
name: "testring"
cryptokeys: [
0: {
purpose: "ENCRYPT_DECRYPT"
resourcePath: "projects/example-project/locations/global/keyRings/testring/cryptoKeys/testring-key"
versions: [
0: gcp.project.kmsService.keyring.cryptokey.version name="1" state="ENABLED"
]
name: "testring-key"
primary: gcp.project.kmsService.keyring.cryptokey.version name="1" state="ENABLED"
}
]
}
]
We also added support for GCP Pubsub Subscriptions, Topics and Snapshots:
cnquery> gcp.project.pubsub { * }
gcp.project.pubsub: {
topics: [
0: gcp.project.pubsubService.topic name="gke-cluster-event-queue"
]
snapshots: []
projectId: "example-project"
subscriptions: [
0: gcp.project.pubsubService.subscription name="gke-cluster-event-queue-subscription"
]
}
See full documentation for all GCP resources in our GCP resource pack docs.
New GCP GKE resource
A new gcp.project.clusters resource lets you explore your GKE clusters and write policies to secure your cluster control plane.
cnquery> gcp.project.clusters { * }
gcp.project.clusters: [
0: {
resourceLabels: {}
name: "luna-gke-cluster-2"
projectId: "luna-edge"
locations: [
0: "us-central1-b"
1: "us-central1-c"
2: "us-central1-f"
]
created: 2022-12-15 20:43:41 +0000 +0000
status: "RUNNING"
zone: "us-central1"
description: ""
nodePools: [
0: gcp.project.cluster.nodepool name="generic-pool"
]
loggingService: "logging.googleapis.com/kubernetes"
expirationTime: null
enableKubernetesAlpha: false
initialClusterVersion: "1.24.5-gke.600"
network: "luna-gke-cluster-2"
clusterIpv4Cidr: "10.20.0.0/16"
autopilotEnabled: false
endpoint: "63.192.209.236"
currentMasterVersion: "1.24.5-gke.600"
id: "123abcbcada644fcb3b83c30ea0efcfc3cd6d8f42a814bccbcb3503181e12b5a"
subnetwork: "luna-gke-cluster-2-subnet"
monitoringService: "monitoring.googleapis.com/kubernetes"
}
]
Other improvements
A few noteworthy highlights:
When running cnspec scan aws --discover instances cnspec now uses EC2 Instance Connect and SSM to connect and remotely scan EC2 instances.
cnspec and cnquery now include improved help and resource descriptions: We've improved many command descriptions to help new users, added descriptions for many resources, and removed some invalid resources that were showing up in the shell's auto-complete.
The Mondoo AWS integration has been improved to better scan large and complex AWS environments. This enables the scanning of regions with more than 1,000 running instances. It now uses AWS Instance Connect to scan instances if SSH scans fail.
More enhancements:
- Improve the reliability of many controls in CIS and Mondoo Linux policies.
- Change SSM-scanned instances to not show up as "Other" scans.
- Avoid rate limiting in the AWS Lambda integration by reducing total API calls.
- Improve help and resource autocomplete text.
- Remove some unhelpful warning log messages in cnspec and cnquery.
- Fix the display of long Kubernetes integration names in the Kubernetes integration page.
- Fix login failures using the latest release of Safari on macOS and iOS.
- Fix incorrect display of long organization IDs in the create organization window.
- Fix MachineType error in gcp.compute.instances resource.
- Fix integer comparisons in MQL failing when resources returned a 32-bit integer instead of the assumed 64-bit integer.
- Allow users to navigate the console tabs with the keyboard.
- Allow users to upload policies that use alternative YAML MIME types to the Policy Hub.
- Fix errors in Ensure default user umask is 027 or more restrictive and Ensure default user umask is configured controls within Mondoo and CIS Linux policies.
- Fix some help descriptions not being displayed.
- Don't cut off the beginning of some help descriptions.
- Using two or more search filters in the console requires all filters to match instead of just one.
- Allow organization owners to delete invites.
- Improve the default output of the kernel resource.
- Fix terraform.module not discovering all modules.
- Fix invalid command examples in some console integration pages.
- Update Workstation integrations page text to better match terms used by cloud vendors.
- Show better results for failures in the Google Cloud (GCP) Security by Mondoo policy.
- Only check SSH server configuration when the SSH server is installed in the Linux Server Security by Mondoo. Thanks. @stdevel!
- Avoid failures when the Kubernetes Ingress has no certificates.
- Fix queries in Linux Workstation Security by Mondoo, BSI SYS.1.2 Windows Server, and Amazon Web Services (AWS) Operational Best Practices, CIS Distribution Independent Linux Benchmark, and CIS VMware ESXi 6.7 Benchmark policies that were not executing.
- Don't show a policy lint error if the policy spec has either scoring queries or data queries attached.
- Improve reliability when scanning instances using SSM in cnquery, cnspec, and the Mondoo AWS Integration.
- Better describe when a directory of Terraform or Kubernetes files is scanned.
- Improve reliability in MQL queries that execute commands concurrently.
- Don't silently fail to run the socketstats resource when it's not supported.
- Improve the reliability of scanning ECR images.
- Ensure that gcp.project.bigquery resource IDs are always unique.
- Change the default values in github.repository from id to fullName to make it easier to find repositories.
- Print labels when running MQL queries that use variables inside blocks.
- Show an error instead of crashing if the config file contains malformed keys.
- Avoid a potential crash when running cnspec login on a fresh installation.
- Fix an issue where the fallback to ssh-agent authentication was not working properly
- Improve client setup instructions in the console to resolve failures
- Simplify the workstation setup instructions
- Update Packer integration instructions to use cnspec and the latest Mondoo packer plugin
- Update long-lived token instructions to use cnspec
- Make sure that query result data displays in the console scan results
- Improve the reliability of Kubernetes integration status data in the console
- Fix the loading of inventory files when cnspec is running in serve mode
- Fix BSI/CIS/Mondoo Windows policies to account for users on a system that have not yet logged in
- Improve remediation steps in Mondoo and CIS policies
- Resolves slow loading times on the integrations tab
- Fix vendor specific icons not always displaying for policies in Policy Hub
- Add alias for mondoo login to the existing mondoo register command so that cnspec and mondoo commands match



