
Welcome to the June 2022 recap of Mondoo releases.
We have a lot of exciting changes to share from our work in June:
Automatic Container Discovery for Kubernetes
Agentless AWS EBS Volume Scanning
AWS Cross-Organization Queries
Kubernetes Scanning Enhancements

Automatic Container Discovery for Kubernetes
Problem
It is difficult to secure all the parts that make up a Kubernetes cluster. Particularly containers have to be manually added and scanned by users.
Solution
Mondoo now automatically discovers and scans all public containers in Kubernetes clusters. The scan will now test both the overall Kubernetes cluster and pod security, as well as evey running container in that cluster. These new containers are each added as a new asset.
This can be enabled in command line scans via:
mondoo scan k8s --discover=all
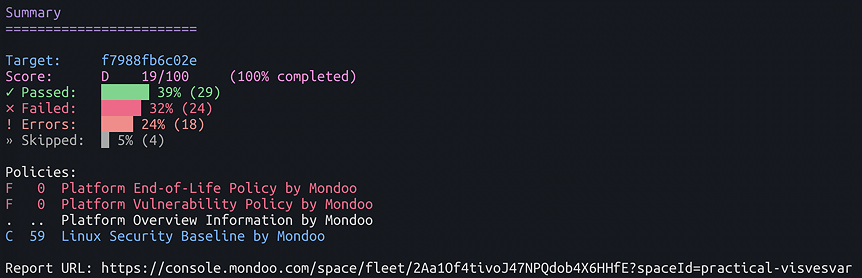
New Overview Page
Problem
When logging into the Mondoo console, users didn't have immediate access to the essential information about their infrastructure.
Solution
The Overview page has been refreshed to focus only on the most helpful information. If you use technologies like AWS and Kubernetes, you can see an overview for these integrations directly on the page. We remove cards if the integration is not used.
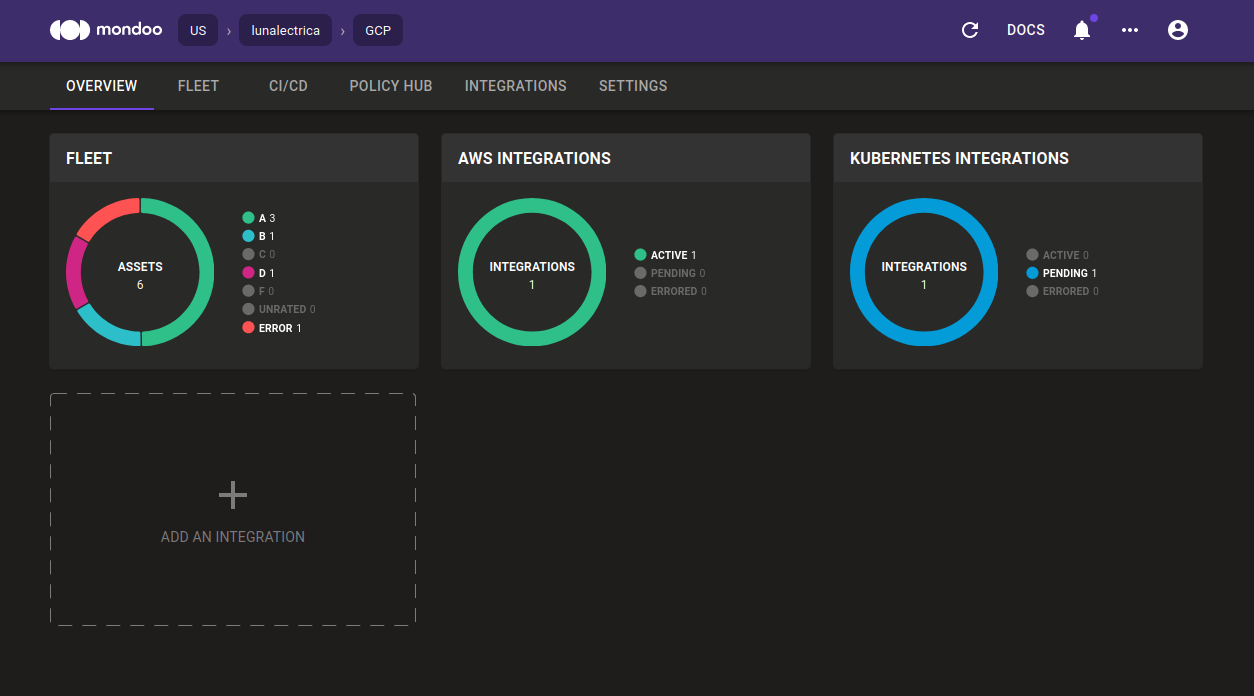
Information about managed clients is no longer part of the Overview page. Instead, you can now access the list of managed clients via the Integrations page.
We also updated how Mondoo integrations report their status to include a new Pending status. This better describes the status of integrations that haven't failed but instead just haven't reported to the Mondoo Platform yet.
Integrations Marketplace
Problem
It is difficult to get started with Mondoo and add the first systems of your infrastructure. This affects anything from local machines to cloud accounts and deeper integrations.
Solution
We have completely re-designed the Integrations page. With this new Marketplace, it is much easier to find, install, and manage your Mondoo integrations and clients from a single location.
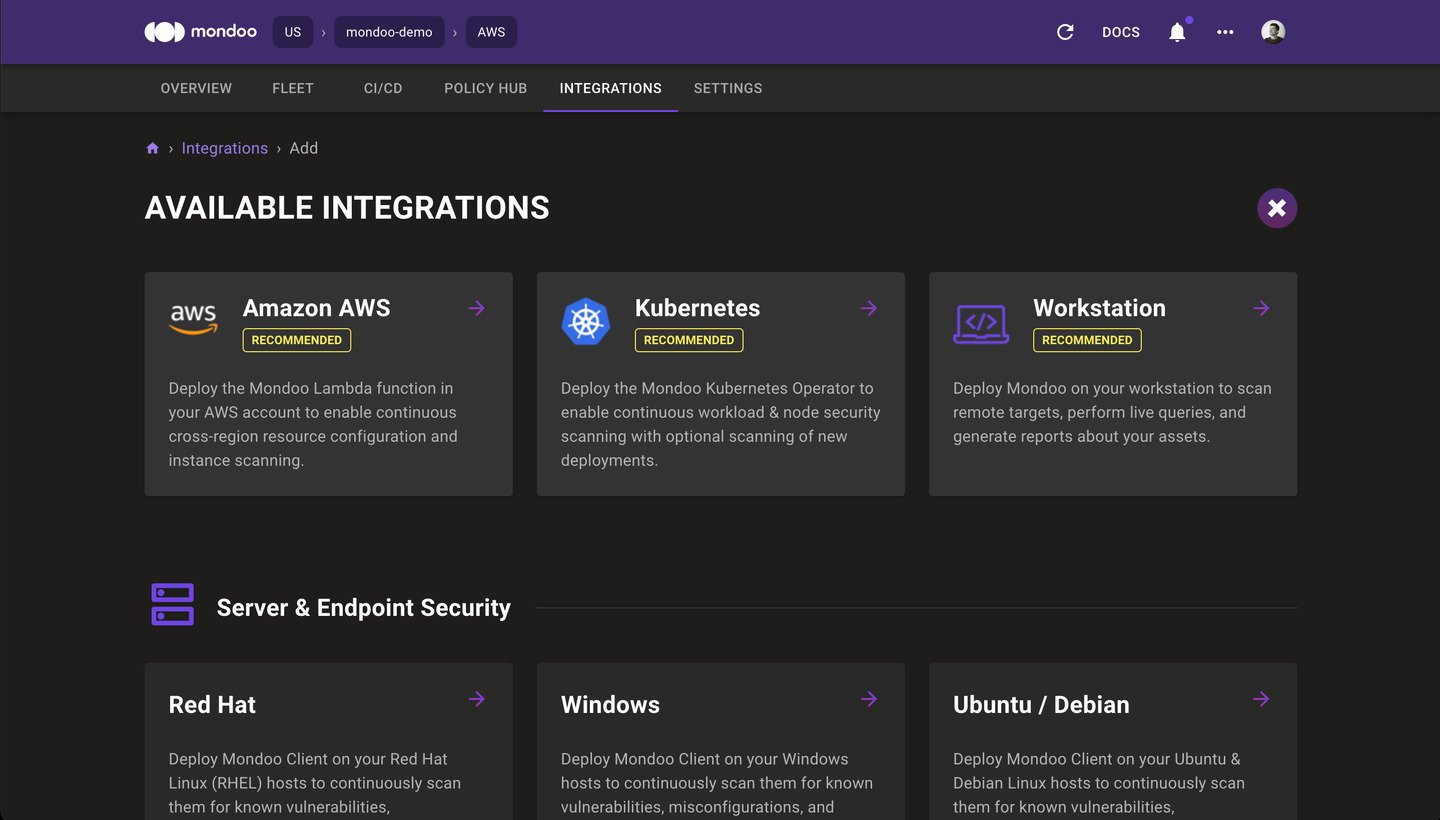
Packer Plugin Mondoo
Problem
Many users want to secure the machine images that they create with HashiCorp Packer. However, using Mondoo with Packer forced people to jump through more hoops than contestants in a Japanese game show, facing manual downloads, manual configuration, and an overall complicated setup.
Solution
Mondoo is now available as a native, open source Packer plugin. You can include Mondoo directly in any Packer 1.7 or higher installation by adding the following blocks to your template:
packer {
required_plugins {
mondoo = {
version = ">= 0.2.1"
source = "github.com/mondoohq/mondoo"
}
}
}
build {
...
provisioner "mondoo" {
score_threshold = 80
on_failure = "continue"
asset_name = "${var.image_prefix}-${local.timestamp}"
}
}
Check out our getting started guide on Building Secure AMI Images with Mondoo and Packer for more details, and add Mondoo to your Packer builds today!
Agentless AWS EBS Volume Scanning
Problem
Some users want to scan EC2 instances for security and vulnerabilities without having any direct access to these nodes. They want to inspect EC2 instances externally without compromising on the security checks they can run.
Solution
Mondoo now provides fully agentless AWS EBS Volume Scanning. This allows us to perform a read-only evaluation of EC2 instances without accessing the instances and without installing any agents. Mondoo can quickly scan any instance, snapshot, or volume without impacting production workloads.
Requirements
Requires the ability to run mondoo client in the same AWS account as the infrastructure you wish to scan. AWS CloudShell is excellent for this! The scanner needs permission to list instances, copy snapshots, create volumes, and attach volumes to instances.
====================================================
Here is an example AWS security policy to enable Agentless AWS EBS Volume Scanning. You can see the details below:
"Version": "2012-10-17",
"Statement": [
{
"Condition": {
"StringEquals": {
"aws:ResourceTag/Created By": "Mondoo"
}
},
"Action": [
"ec2:AttachVolume",
"ec2:DetachVolume",
"ec2:DeleteVolume",
"ec2:DeleteSnapshot"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Action": [
"ec2:CreateSnapshot",
"ec2:CreateVolume",
"ec2:CopySnapshot",
"ec2:CreateTags",
"ec2:DescribeInstances",
"ec2:DescribeVolumes",
"ec2:DescribeSnapshots",
"kms:Decrypt",
"kms:ReEncryptTo",
"kms:GenerateDataKeyWithoutPlaintext",
"kms:DescribeKey",
"kms:ReEncryptFrom"
],
"Resource": "*",
"Effect": "Allow"
},
{
"Condition": {
"Bool": {
"kms:GrantIsForAWSResource": "true"
}
},
"Action": "kms:CreateGrant",
"Resource": "*",
"Effect": "Allow"
}
]
}
====================================================
Example usage:
mondoo scan aws ec2 ebs <INSTANCEID>
mondoo scan aws ec2 ebs volume <VOLUMEID>
mondoo scan aws ec2 ebs snapshot <SNAPSHOTID>
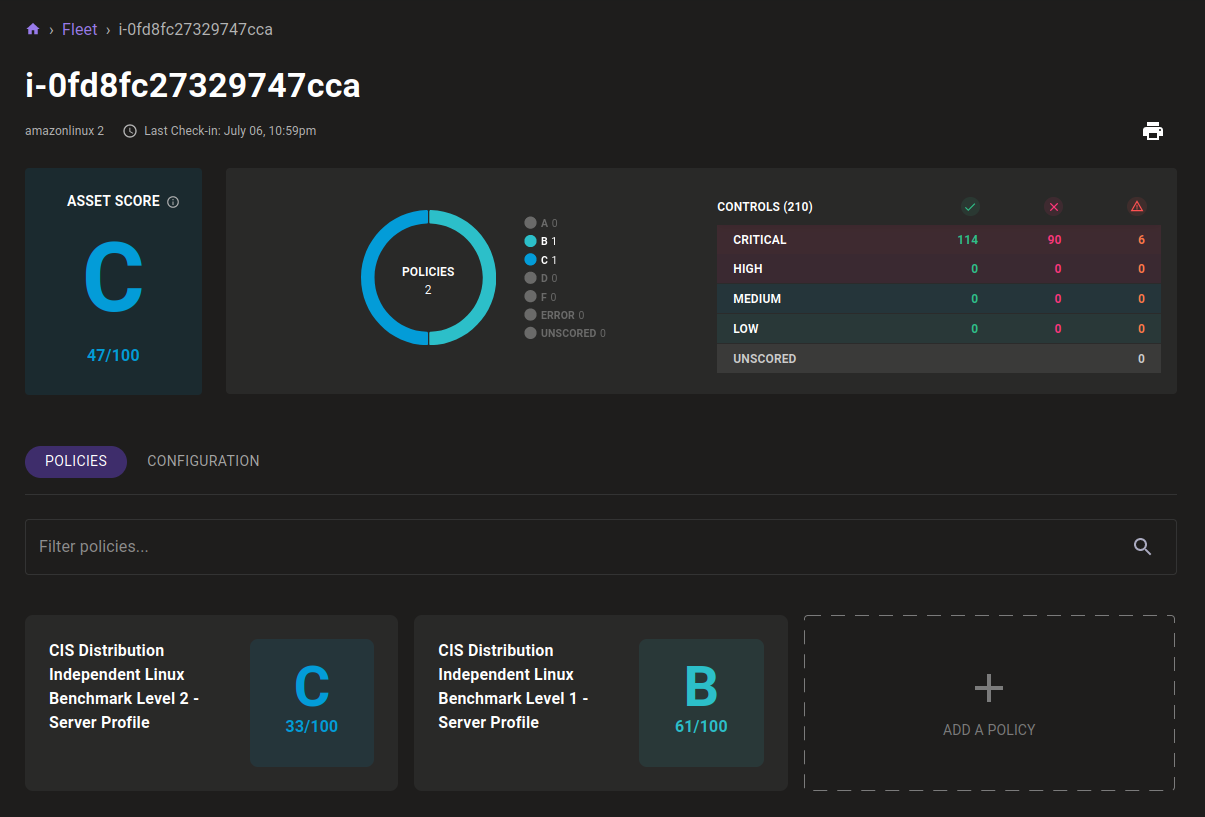
AWS Cross-Organization Queries
Problem
Users with many AWS accounts in an AWS Organization find it challenging to discover resources across these accounts. This often requires users to know about all of their infrastructure, regardless of the associated AWS account.
Solution
Using the Mondoo AWS integration, users can now search across every AWS account associated with an AWS Organization. It is easier to find abandoned or untagged resources, as well as locate resources tagged to a particular project or cost center.
Example
I need to find a particular S3 bucket, but I don't know in which AWS account it may be located. I only know part of the bucket name.
mondoo exec \
--integration-mrn //integration.api.mondoo.app/spaces/<SPACE_ID>/aws/<INTEGRATION_ID> \
'aws.s3.buckets.where(name.contains("lostbucket"))'
New GitHub Resources
Problem
Users want to keep their GitHub repositories and organizations secure. However, doing this manually via APIs is so much work. Can’t we do better?
Solution
Mondoo adds flashy new Github resources! These allow you to gather critical information about the security of your GitHub organization and any public repositories you wish to examine.
To get started you need your GitHub token to talk to the API. Here are two examples of connecting a Mondoo shell to a GitHub user and organization respectively:
mondoo shell -t github --option token=${GH_TOKEN} --option login=USERNAME
mondoo shell -t github --option token=${GH_TOKEN} --option organization=ORGANIZATIONNAME
Once connected to GitHub, you can easily query resources or write assertions:
github.organization { repositories }
github.repository("mondoohq/client") { files }
Keep an eye out for our Github Security Policy that will ship next month 🎉.
Kubernetes Scanning Enhancements
Problem
The Kubernetes admission controller scanning in the CI/CD tab could be quite busy, and it was often difficult to find new deployment scans in this UI, because of a flood of scan reports coming in.
Solution
We revamped how scanning occurs in the Mondoo Kubernetes Operator 0.5.0, with scans now only occurring on Kubernetes resources. This means you'll no longer see scans for each new pod generated during auto scaling, cron jobs, or otherwise. This makes it much easier to see the security status of new workloads entering the cluster.
Other improvements
- A new enterprise Mondoo MSI Installer (mondoo-enterprise.msi) has been added, which is great for MDM and management solutions. It requires a
REGISTRATIONTOKEN, which it uses to automatically register the system with Mondoo and start the service. - Optimized Kubernetes scans and reduced scan durations from 2min 10s to only 9s!
- Using the
processes.listMQL resource on a Docker container will no longer run the container out of file handles - Fleet-wide statistics now correctly include unscored assets
- The CVE view on the individual asset now shows the total number of packages scanned
- The Continuous Integration view now shows a timestamp for each branch scanned
- The installation and usage instructions for HashiCorp Packer & HashiCorp Terraform in the Integrations page is much more useful
- Scanning Microsoft Azure with the Mondoo client no longer requires a URL
- Container scans now properly set platform architecture
- Improved the readability of buttons on the SAML setup page
- Fix the Mondoo Client Windows service failing to stop
- Various fixes to the junit output from Mondoo Client
- Return actual asset error when scanning on CLI without policies set
- Improve the display of the Mondoo Console on mobile devices
- Display error messages when the AWS integrations fail to scan instances
- Add links to OpenShift and cert-manager on the K8s Integration setup page
Policy updates
Mondoo has added support for Amazon Linux 2022, which is currently in preview mode.
We updated the following policies: Linux Security Baseline (see 6.4 release notes and 6.5 release notes) Kubernetes Application Benchmark by Mondoo (see 6.4 release notes and 6.5 release notes)
You can find all of these policies in your Policy Hub: select Add Policies



