
Sometimes when you're running Kubernetes workloads in AWS using EKS, it feels like Amazon is doing your job for you. EKS abstracts away much of the complexity in day-to-day Kubernetes infrastructure management.
Tasks like configuring, tuning, and even securing the Kubernetes control plane become an Amazon problem and not a you problem. Unfortunately, when it comes to security, you’re not off the hook. While Amazon's team of security experts are managing your control plane, the rest of your cluster security is still your responsibility.
Full-stack Kubernetes security: beyond the control plane
Just like you wouldn't consider your cloud infrastructure safe just because you've secured an ALB, your Kubernetes infrastructure isn't safe either. Securing etcd and other control plane components is not enough to guarantee safety. Security always comes down to the weakest link in the system. It is therefore critical to safeguard the control plane, cluster nodes, workloads, and even running containers.
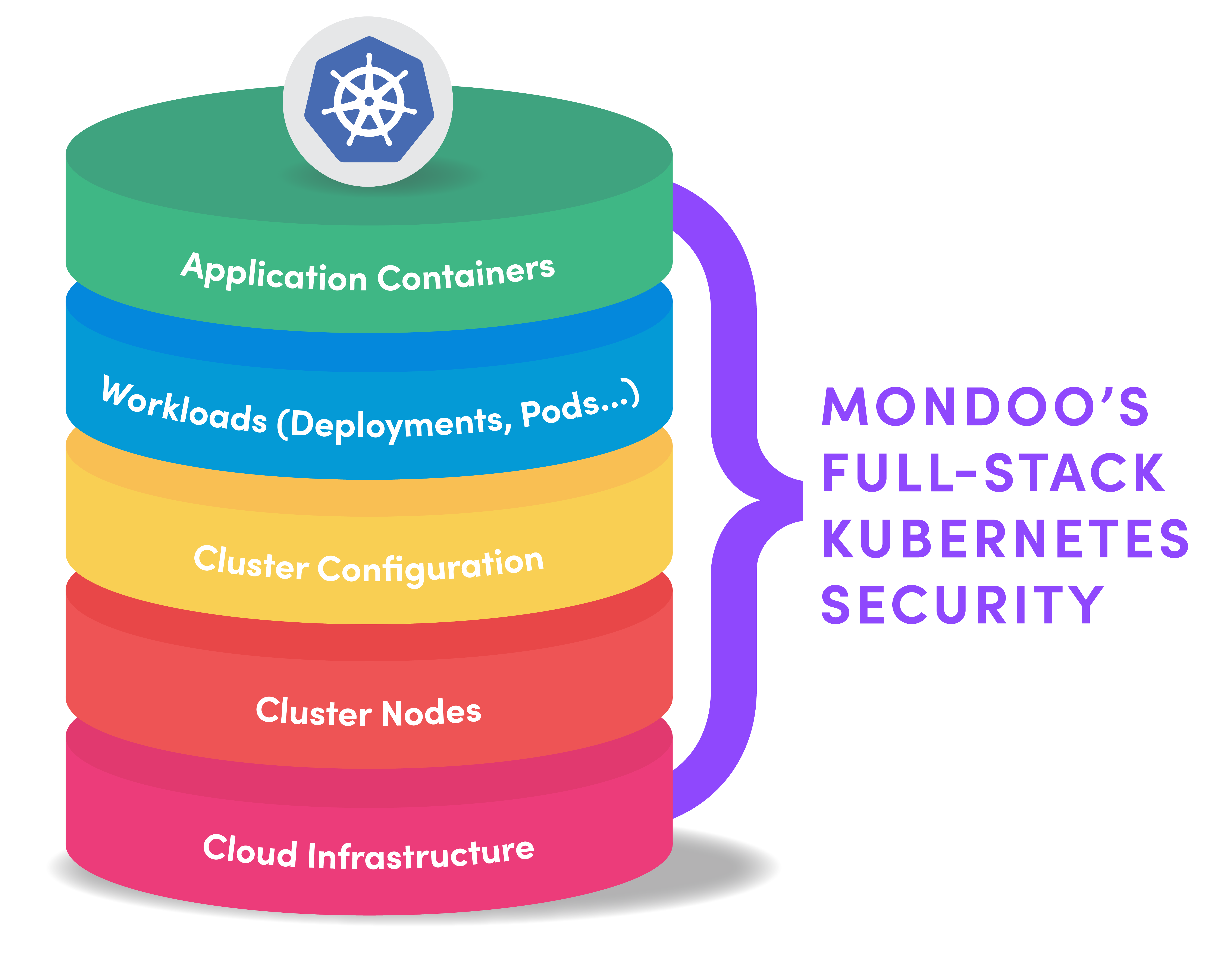
At Mondoo we’ve built a layered approach to Kubernetes protection that we call full-stack Kubernetes security. We monitor:
- Containers
- Workloads (deployments, pods, and more)
- Cluster configuration
- Cluster nodes
- The infrastructure your cloud runs on
Only with this layered approach can you ensure that your application infrastructure is truly secure.
Continuously scanning EKS with Mondoo
Mondoo provides full-stack Kubernetes security for your EKS clusters using our Mondoo Kubernetes Operator. The operator runs in the background on your EKS cluster to scan cluster nodes, cluster configuration, individual workloads, and running containers. This insight provides a layered security approach to help secure your EKS cluster. It also helps to secure the workloads that your application teams are deploying to the cluster.
The operator also includes an optional Kubernetes admissions controller that scans all new or updated workloads that enter your cluster. The admission controller gives you visibility into the security of newly deployed workloads in addition to the state of existing running cluster workloads.
Scan your cluster now
To start scanning your cluster, visit https://console.mondoo.com and create a free account. You can log in using your Google, Microsoft, or GitHub account. Once you’re logged in, our trusty mascot, Ada, will help you start scanning your infrastructure.
Select BROWSE INTEGRATIONS to see a list of integrations you can use to scan your infrastructure with Mondoo. Our top three recommended integrations help you get started securing your AWS and EKS infrastructure.
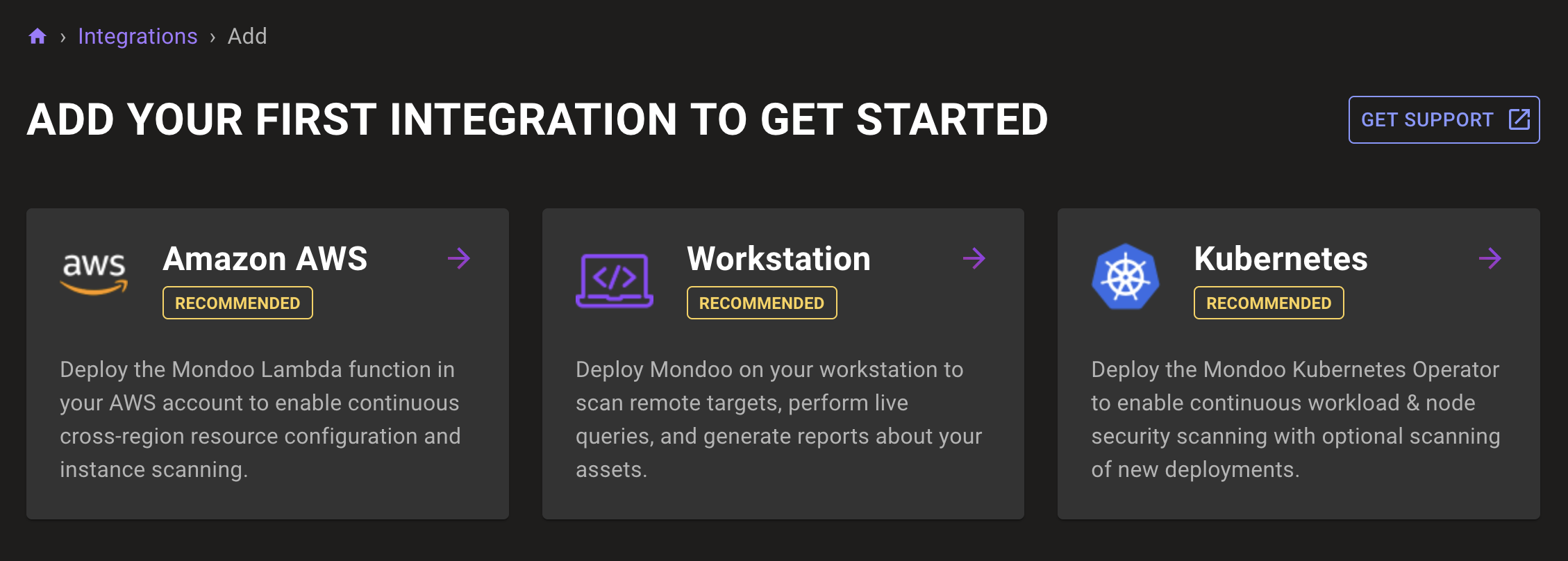
- The Amazon AWS integration runs a Lambda function in your AWS account. This function discovers and scans services and EC2 instances without the need to deploy agents. → Learn more about our AWS integration
- The Workstation installation includes the Mondoo binary for use on your local development workstation. The Mondoo CLI allows you to remotely scan servers over SSH/WinRM. It can also scan cloud accounts, Kubernetes clusters, and SaaS services without deploying additional infrastructure. You can also use this binary to locally scan Kubernetes manifests, Docker images/containers, and Terraform configs before deploying to staging or production environments.
- The Kubernetes operator is what we’ll be using today to secure our EKS cluster and workloads. Select Kubernetes to set up the operator integration.
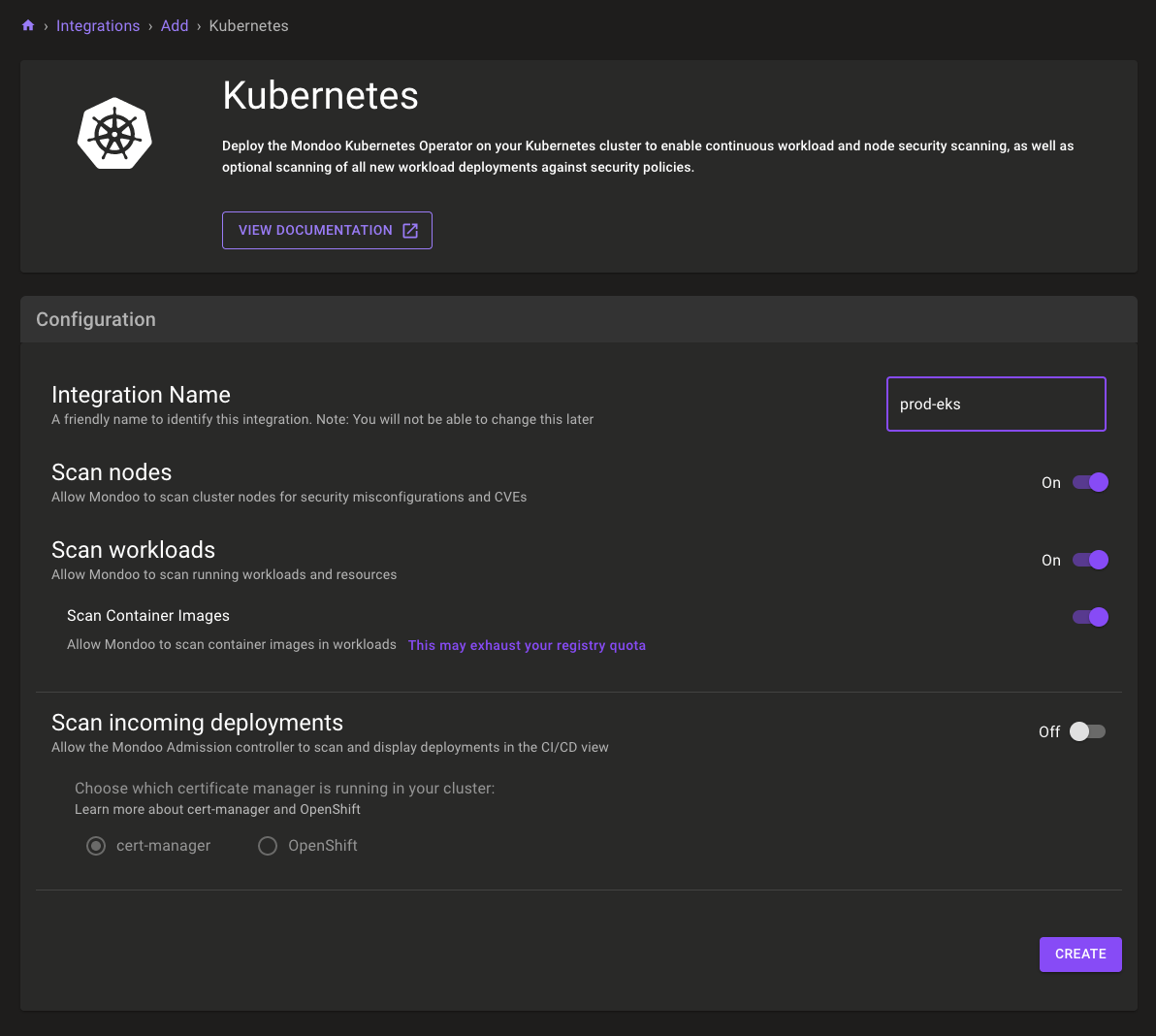
To configure the integration, we’ll provide a name and select which components of our cluster we want to scan. Since we’re interested in securing the complete cluster, we’ll leave the defaults for our prod-eks integration.
Selecting CREATE, You’ll receive a command to run to install the operator and create a Kubernetes secret to store Mondoo platform credentials.
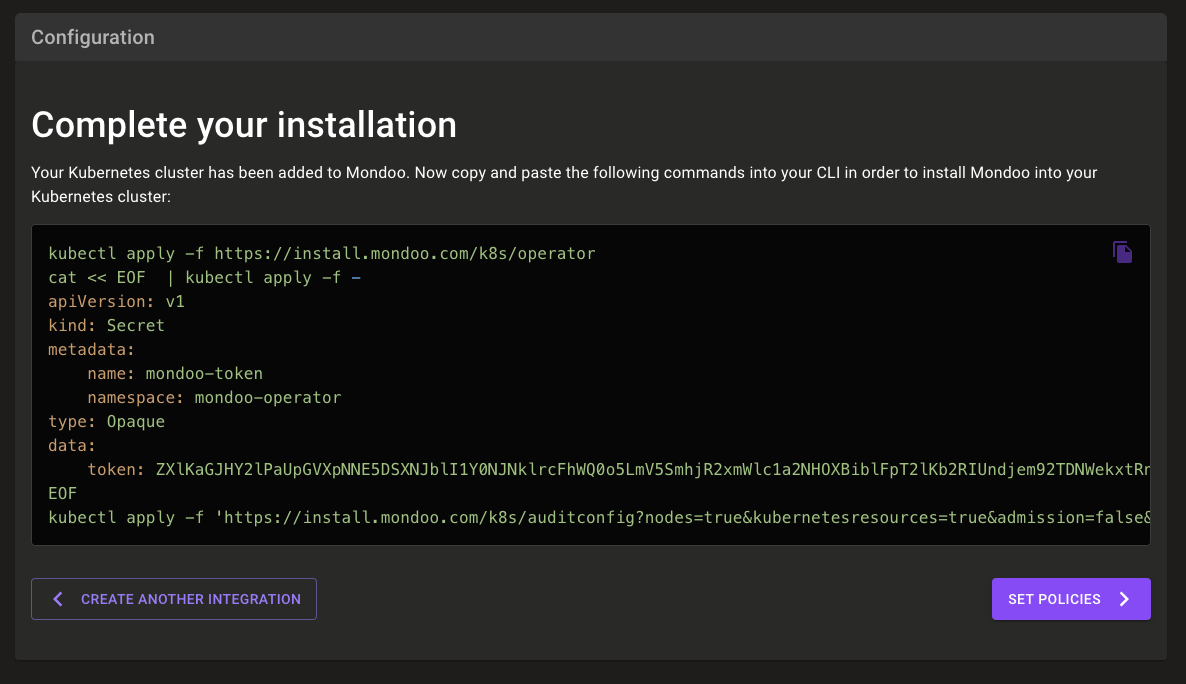
Once set up, Mondoo will also recommend policies to help you secure your systems. By default, Mondoo applies our out-of-the box cluster/workload security and best practice policies. You can also enable Center for Internet Security (CIS)-certified EKS policies and NSA security policies.
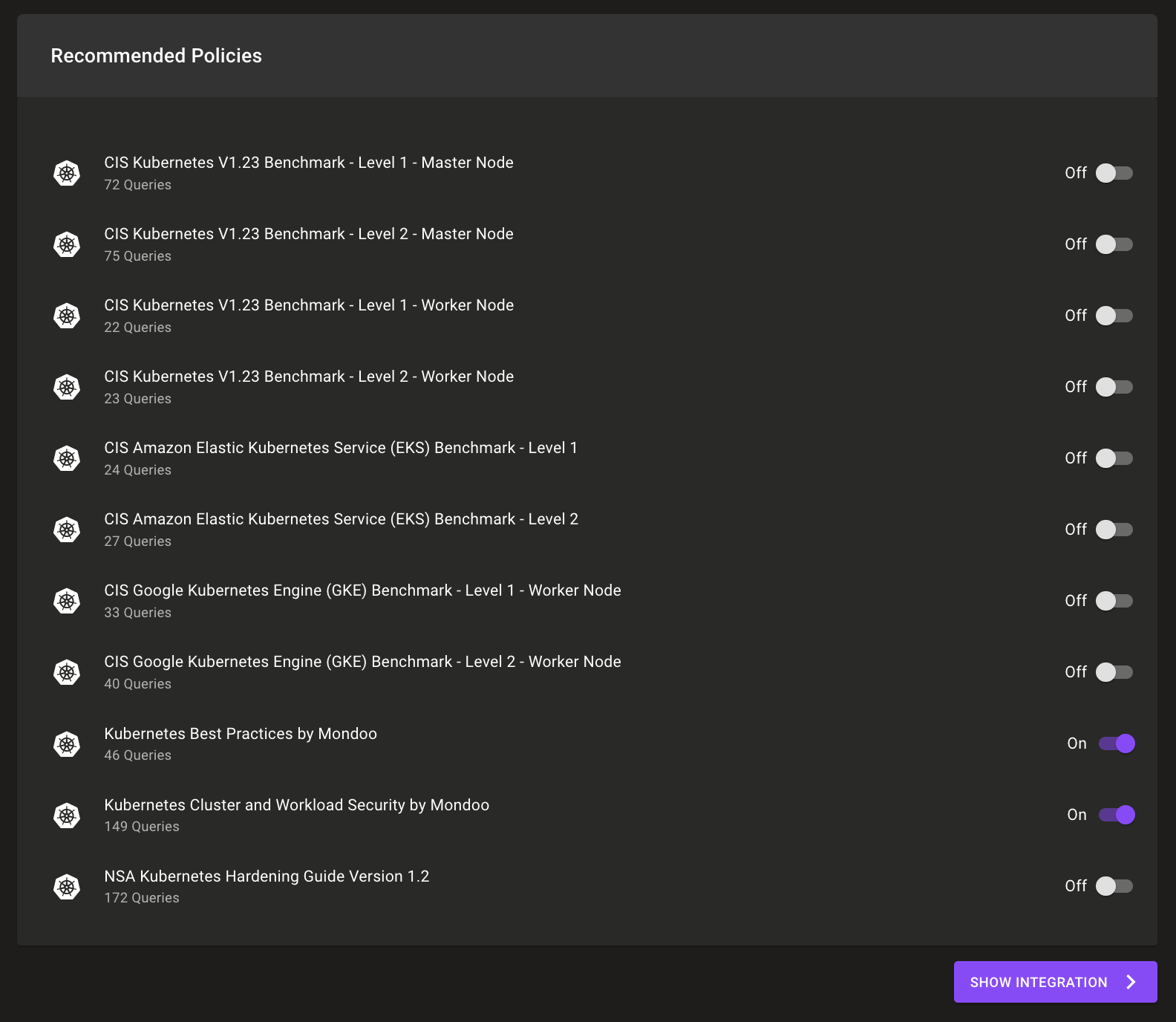
With your policies enabled, Mondoo will now scan your cluster and report cluster and workload security results.
Viewing cluster security
Once the operator has scanned your cluster, you’ll find a number of assets in the Fleet tab.
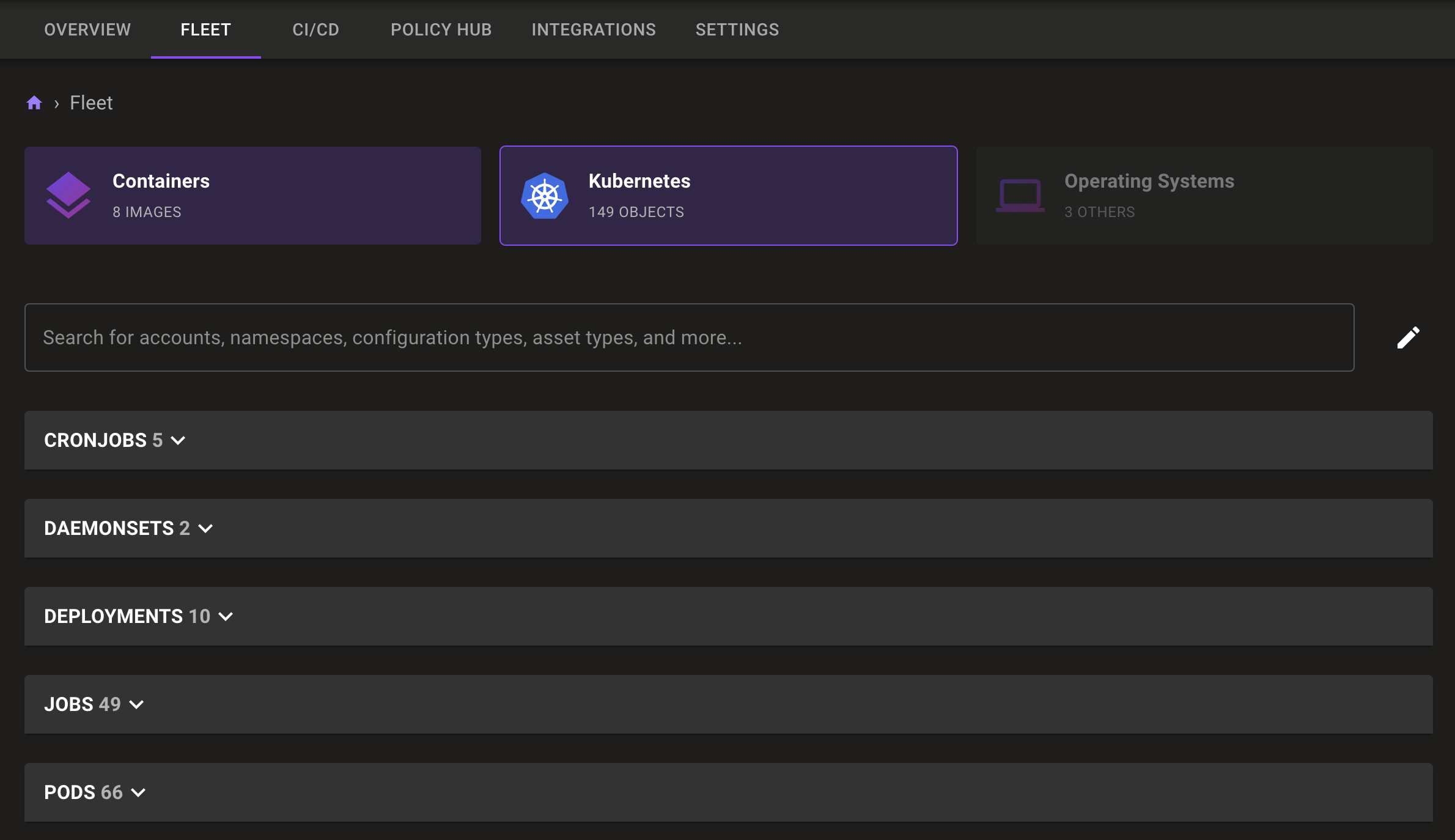
These assets include the Kubernetes cluster itself (and workloads), the operating systems that run your cluster, and the containers running in the cluster. You can dive deeper into each of these high-level categories to see different groups of scanned assets.
For example, under Kubernetes, you can view all deployments to get a quick snapshot of your deployment security.
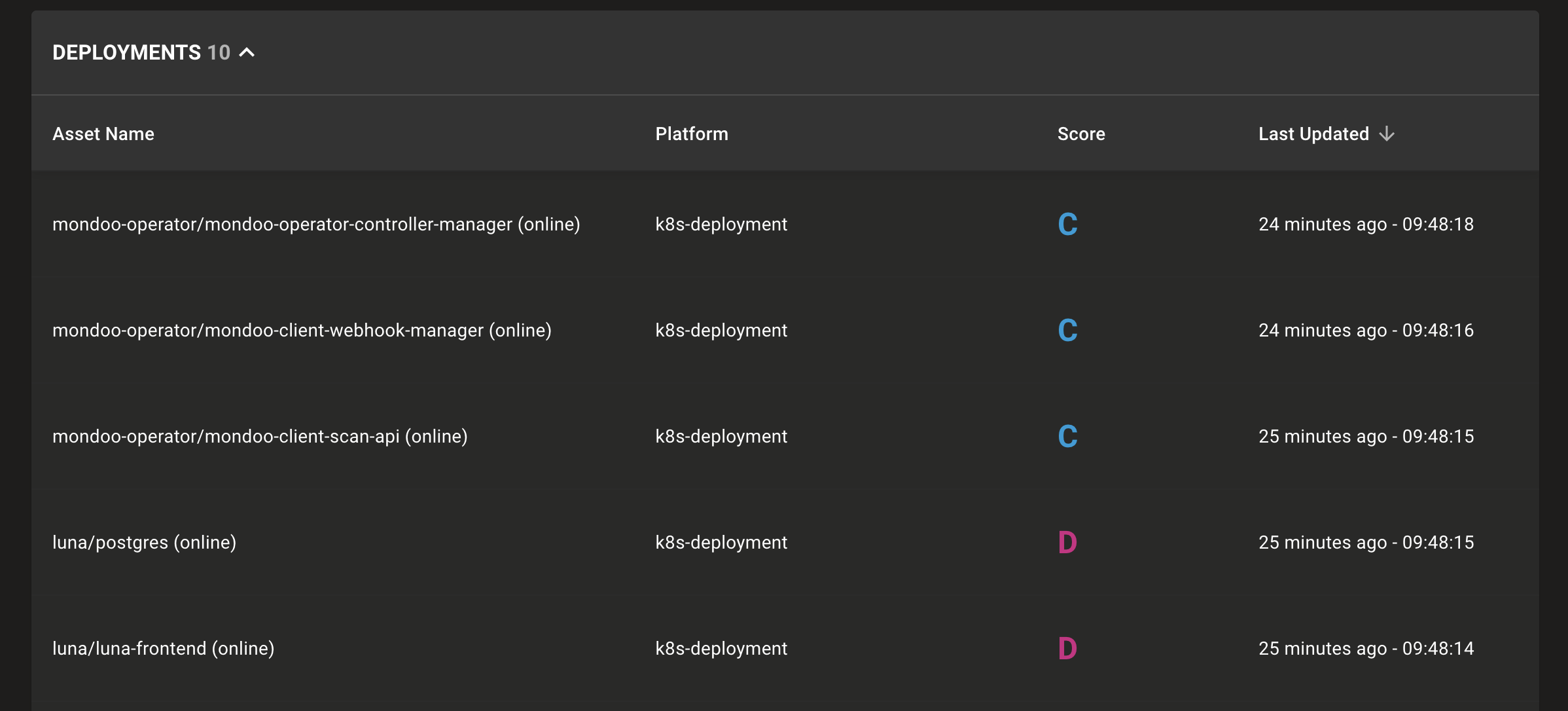
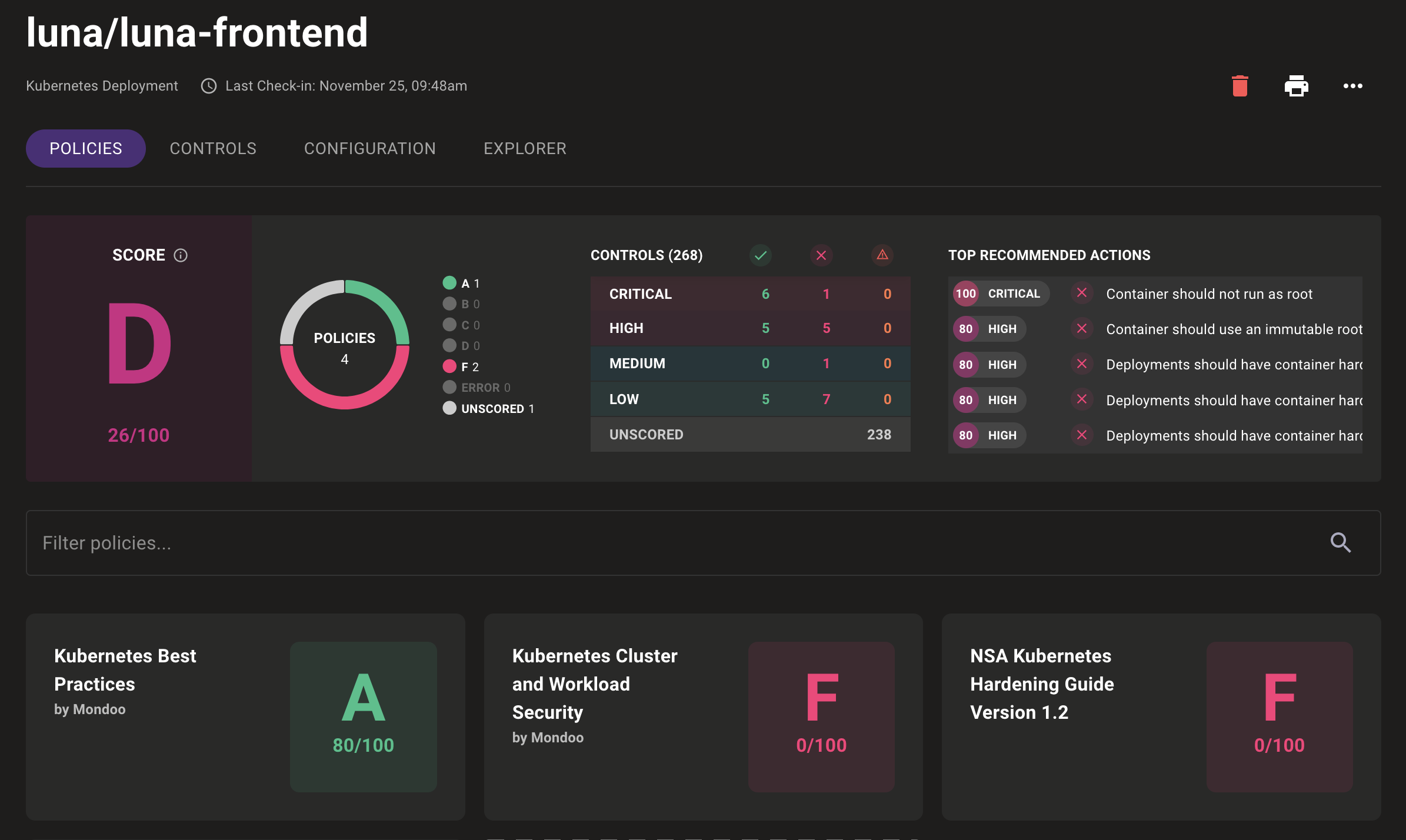
Select any of these deployments for a detailed view. This view will include the asset's security, such as the top vulnerabilities, policy scores, and individual controls. Our example luna/frontend deployment has several critical issues such as the container running as root, which could be used as part of a container escape attack. Each control details the workload security violation and instructions on securing the workload.
Security, compliance, and vulnerabilities
Rely on Mondoo to secure all aspects of your Amazon cloud environment. From instances to Kubernetes, from buckets to APIs, Mondoo finds vulnerabilities and misconfigurations that put your organization at risk.




