
Introducing cnquery and cnspec
Maintaining real-time insights into the current state of your infrastructure is essential for both platform engineering and security. Over the past decade, projects like Osquery demonstrated the value of accessing your operating system like you would a database. Since then, the space has evolved beyond the OS with tools that inspect cloud, Kubernetes, or interconnected SaaS services.
We open sourced our next generation of real-time, GraphQL-based asset inventory and security assessment: cnquery and cnspec. These remove past limitations and integrate with everything you want: clouds, containers, servers, Kubernetes, APIs - even a wild horde of Raspberry Pi-powered robots, if you like.
cnquery: asset inventory
Imagine accessing your entire infrastructure like a giant graph. You can touch any resource or configuration as you would an element in that graph. You extract information you care about and ignore the rest. Imagine you could take a node in that graph, for example a running container, and access its configuration through GraphQL:
processes {
command
pid
}
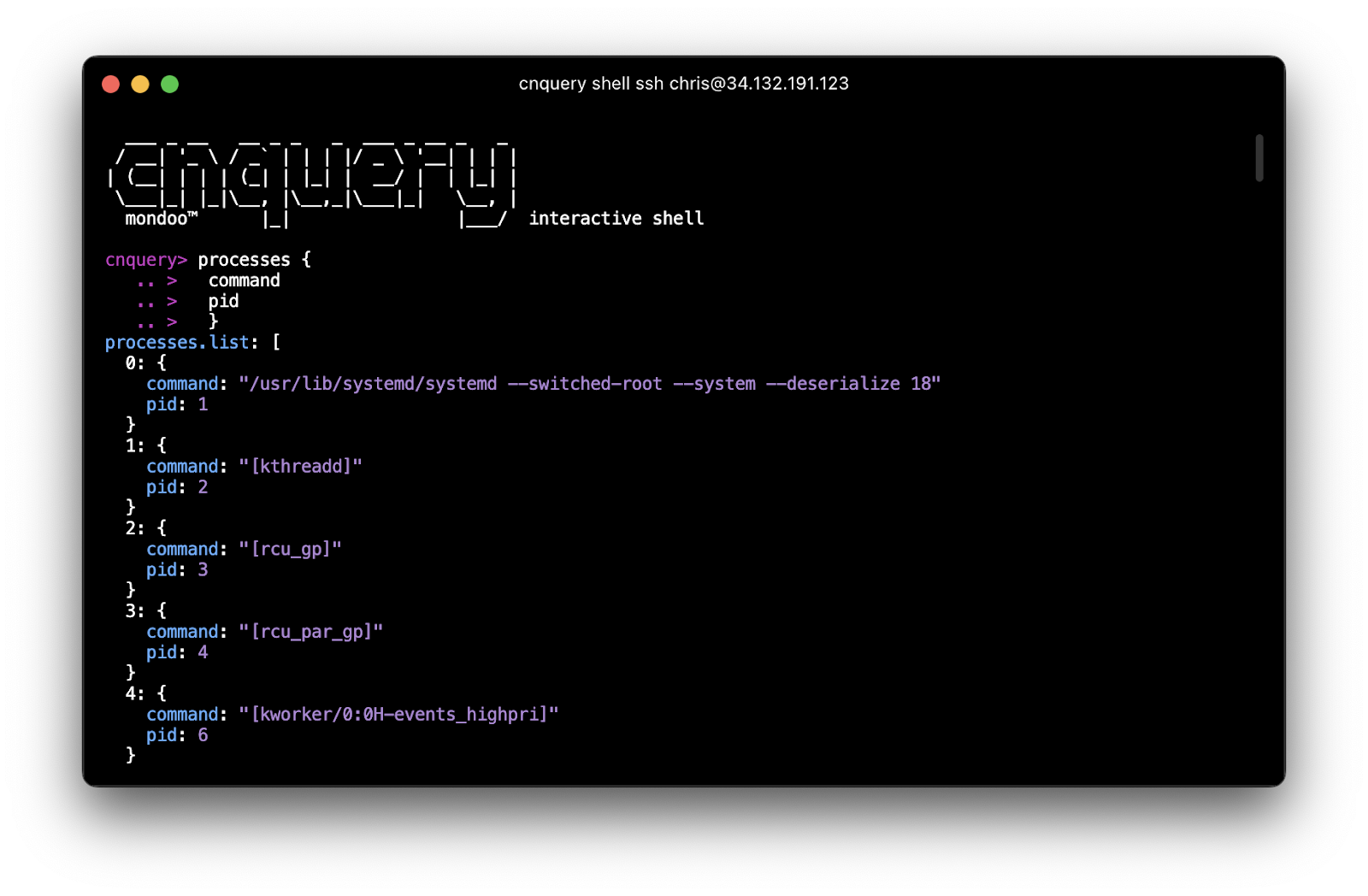
Unlike traditional data models, the advantage of this approach for asset inventory is that it can easily connect related resources for you. Gone are complicated join statements on unrelated data. Instead, you walk the graph of interconnected resources to discover the fields you are looking for:
ports.listening {
port
process {
command
pid
}
}
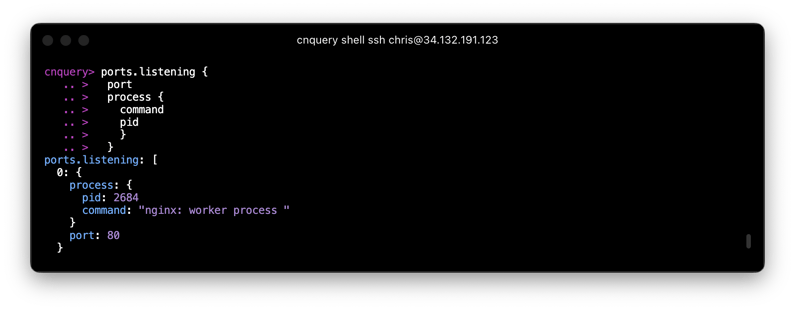
This interaction is easy and fun. You also can quickly add filters:
ports
.where( port > 1024 )
.where( process.command != "" ) {
port
process {*}
}
In this example we filter ports we don't care about and return the port number and everything we know about the process.
This model works just as well for resources in AWS, Azure, GCP, Kubernetes, or other APIs, as we'll explore below. See a complete list of resources. All resources and providers are fully extensible and you can easily add entirely new targets.
aws.iam.credentialReport
.where( passwordEnabled == true ) {
user
mfaActive
passwordLastUsed
}
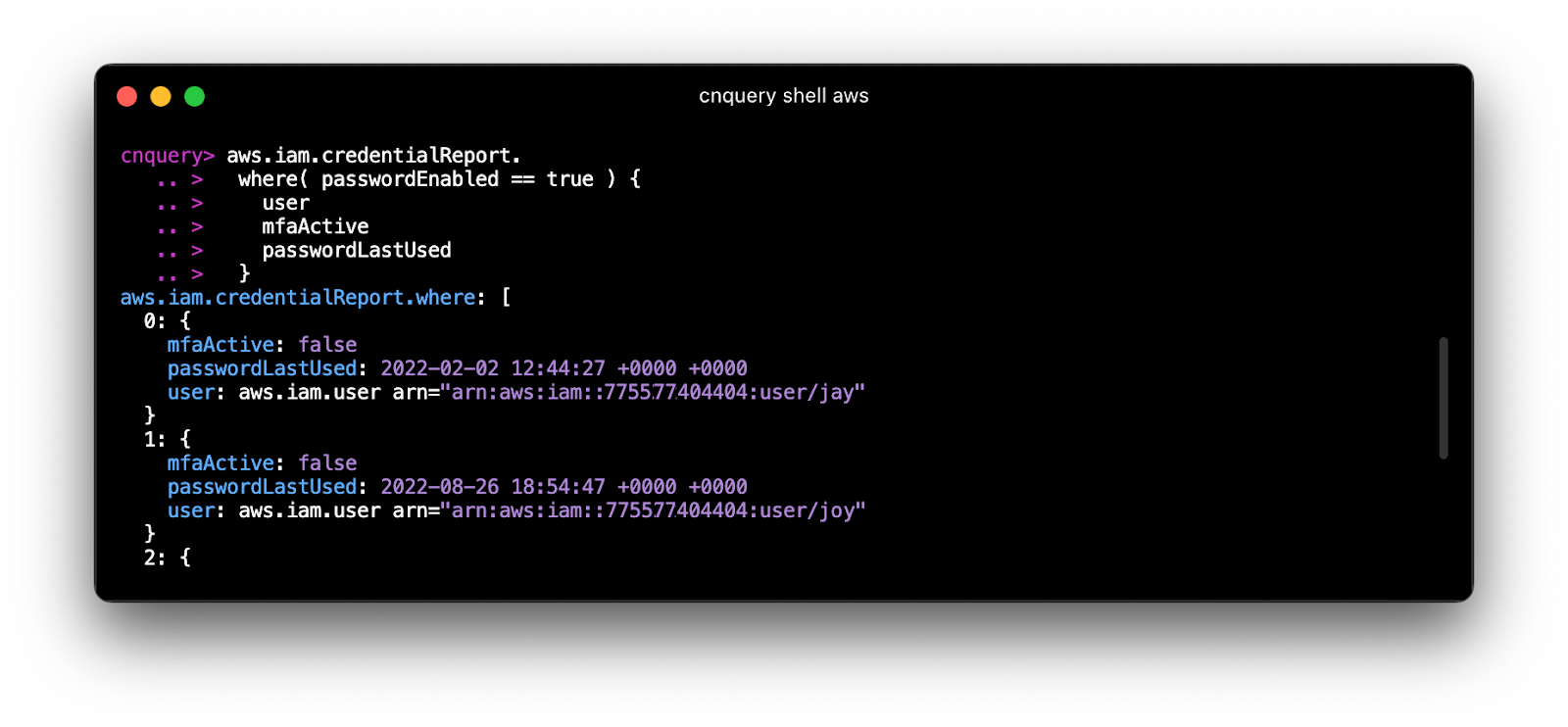
cnspec: security assessments
Once you have insights into your infrastructure, you're ready to add assessments. With cnspec we take the data that cnquery provides and we turn it into tests. For example, we can enforce that all listening ports are started only by sshd executable:
ports.listening.all(
process.executable == "sshd"
)
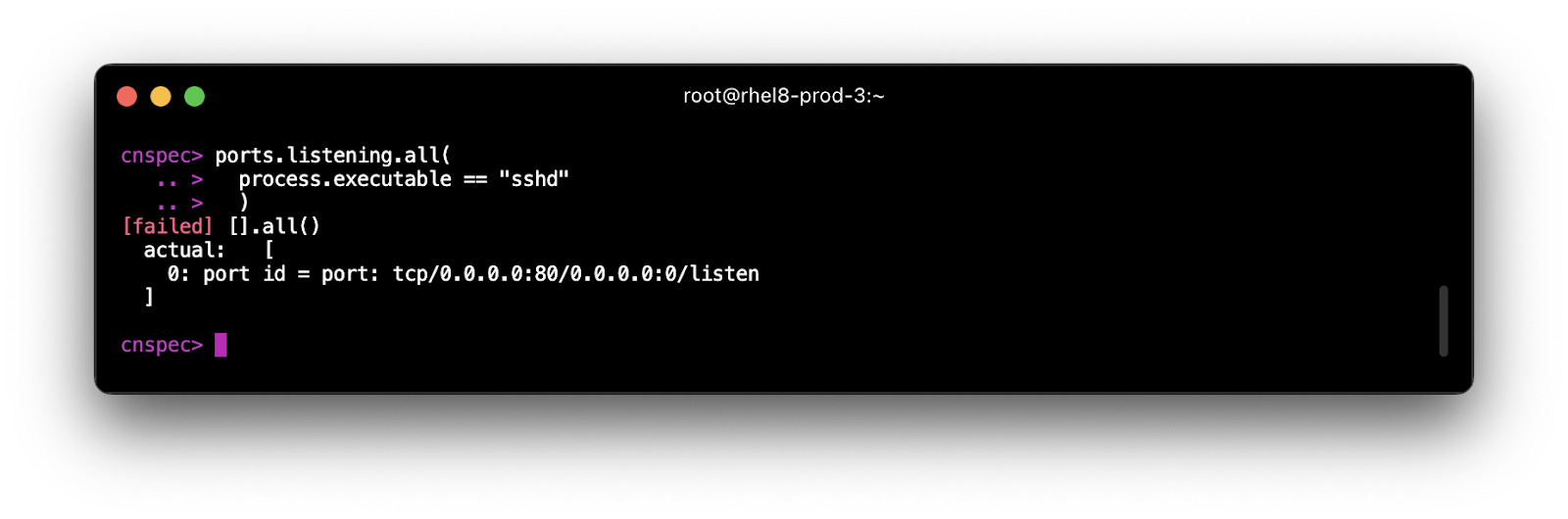 This statement is an assertion that can now be rolled out to all systems with open ports. The keyword all tells cnspec to ensure all ports are started by sshd executable (and print any ports that aren't).
This statement is an assertion that can now be rolled out to all systems with open ports. The keyword all tells cnspec to ensure all ports are started by sshd executable (and print any ports that aren't).
Since a collection of these tests without context wouldn't be very helpful, cnspec allows you to create policies with much needed metadata. Policy metadata communicates audit and remediation steps and indicates which checks are more important than others.
- uid: enforce-only-ssh-port-open
title: Enforce only SSH port is listening
docs:
desc: Only the SSH port is open and listening for incoming connections. This is because...
query: |
ports.listening.all(
process.executable == "sshd"
)
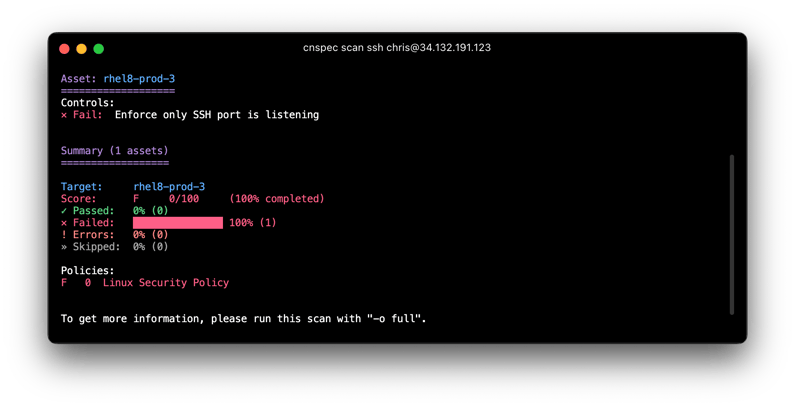 This makes cnspec the first policy-as-code engine that provides full, graph-based access to underlying data and asset relationships. We designed cnspec to be used by non-developers, which makes it far more accessible to a broader group of practitioners.
This makes cnspec the first policy-as-code engine that provides full, graph-based access to underlying data and asset relationships. We designed cnspec to be used by non-developers, which makes it far more accessible to a broader group of practitioners.
cnspec fulfills countless use cases, including security analysis, vulnerabilities, compliance, and operational best practices and validation. The possibilities are endless.
Features
Both cnquery and cnspec are built around MQL, a GraphQL-based approach to gathering and extracting information about your fleet. MQL excels at rapidly traversing related resources, filtering, and picking the data fields you care about.
Resource packs
To connect to as many assets and technologies as possible, cnquery and cnspec come with a large collection of resources out of the box. Our resource packs provide access to over 400 resources across AWS, Azure, Google Cloud, Kubernetes, containers, Microsoft 365, Terraform, GitLab, GitHub, and many more technologies.
See a complete list of resources. They're easily extensible through the cnquery open source project.
Open source policies and query packs
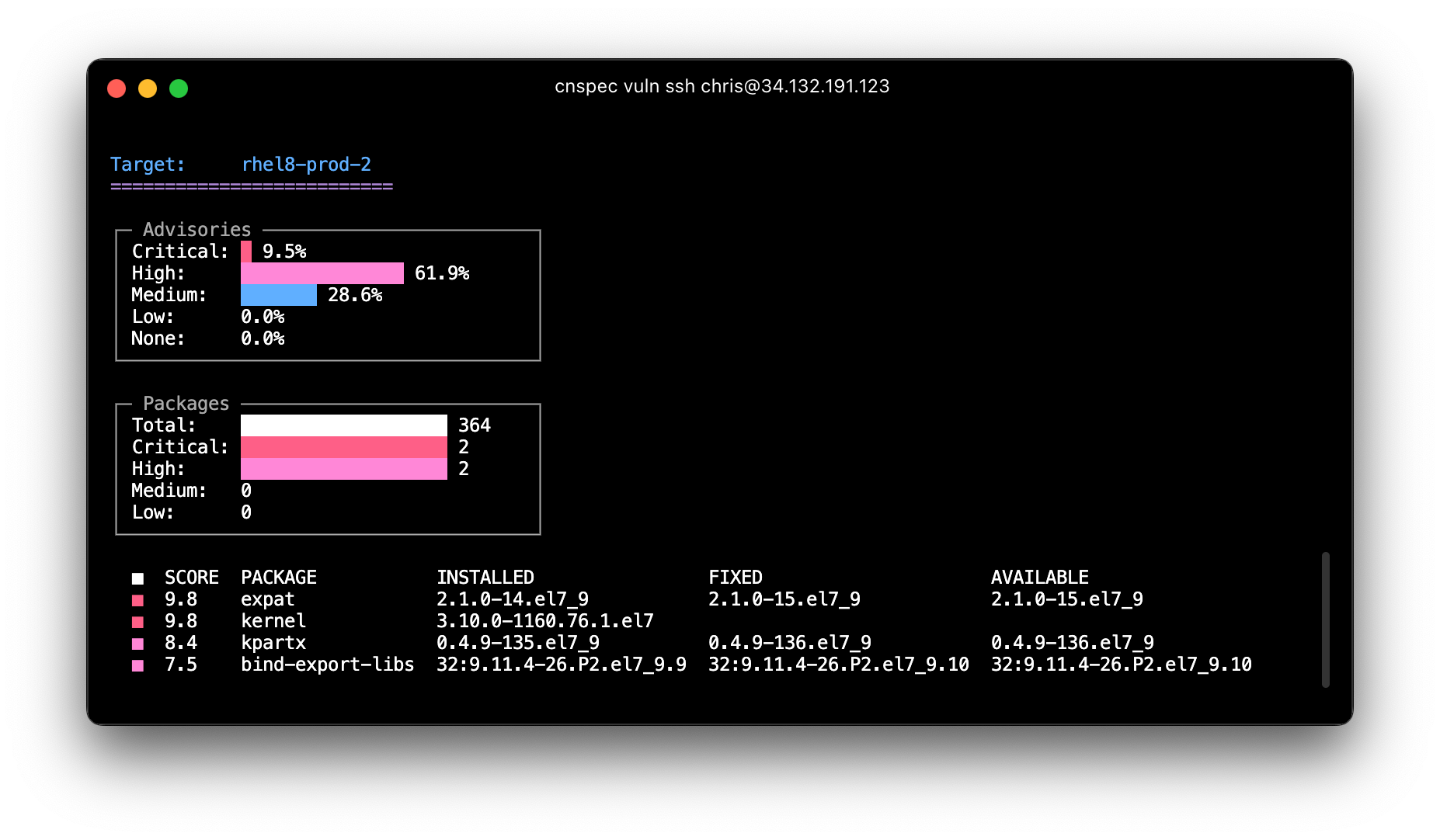
When you scan a target with cnspec, by default it uses one of the matching policies from the open source project cnspec-policies. These are common security checks that help establish a solid security baseline. The project is continuously expanding to include new systems and additional checks. If you authenticate with Mondoo, you can also benefit from vulnerability assessments.
cnquery applies the same principle to data collection: By default it uses a set of query packs that gather useful information about the target system.
Interactive shell
Both projects ship with an interactive shell, which makes it easy to query systems on the fly and interrogate them—without setting up a database. You just specify a target and open the shell. This example uses the system's default AWS configuration:
> cnspec shell aws
cnquery and cnspec shells come with built-in autocomplete, a help menu, and history. Once connected, you can enter any queries and assertions supported by the target:
> aws.ec2.instances { * }
Vulnerability management
> cnspec vuln
Open Source
When we founded Mondoo, we wanted to make sure everyone has access to the right security tools. Having built popular open source projects in the past, we know that an open source solution is the best way to democratize access to security automation.
We're excited to announce that we are open sourcing cnquery and cnspec today. You can check out both projects on GitHub.
We look forward to partnering with you on these game-changing projects. We trust that you’ll see the potential of cnquery and cnspec and build something amazing with us!




