Apple’s Kernel Vulnerability: A Wake-Up Call
Cybersecurity is integral to managing our digital infrastructure in an ever-evolving digital world. Even Apple, known for its robust security measures, is not invulnerable to exploits. A recent issue, CVE-2023-32434, significantly threatens the kernel of macOS Big Sur, Monterey, and Ventura as well as iOS and iPadOS - the heart and brain of any operating system - revealing a vulnerability that could allow a malicious application to execute arbitrary code with kernel-level privileges.
The Threat Unveiled: Understanding CVE-2023-32434
This vulnerability has attracted much attention due to the potential severity of its impact. As defined, an application that exploits this vulnerability could obtain kernel privileges, which could take control of your system, modifying or accessing any data without restrictions. This level of access could lead to data theft, unauthorized system modifications, privacy invasion, and other serious consequences.
Real World Implications: Exploits in the Wild
The kernel vulnerability, as reported, has been potentially exploited in the wild, specifically against versions of iOS released before iOS 15.7. Cybercriminals may have already used this exploit, emphasizing the urgency of addressing this issue.
Behind the Bug: An Integer Overflow
The root cause of the problem is an integer overflow, a common type of software vulnerability. It occurs when an arithmetic operation attempts to create a numeric value outside the range that is representable within the available storage space. This overflow was addressed with improved input validation, a way to check and cleanse the data input to an application.
The Discovery Team: Kaspersky's Role
This specific issue was discovered by Georgy Kucherin (@kucher1n), Leonid Bezvershenko (@bzvr_), and Boris Larin (@oct0xor) of Kaspersky, a multinational cybersecurity and anti-virus provider.
Action Required: Kernel Update
Apple has released a kernel update for macOS, iOS, and iPadOS to patch this vulnerability. Users should install this update promptly to protect their systems from potential threats. Updates like these play a vital role in device security and are a crucial line of defense against the ever-present threat of cyber-crime.
Detect if you are vulnerable with cnspec
We updated our cnspec macOS vulnerability policy to include a detection for CVE-2023-32434. You can run the following script with our open-source cnspec tool.
bash -c "$(curl -sSL https://install.mondoo.com/sh)"
cnspec scan local --policy mondoohq/mondoo-macos-vulnerability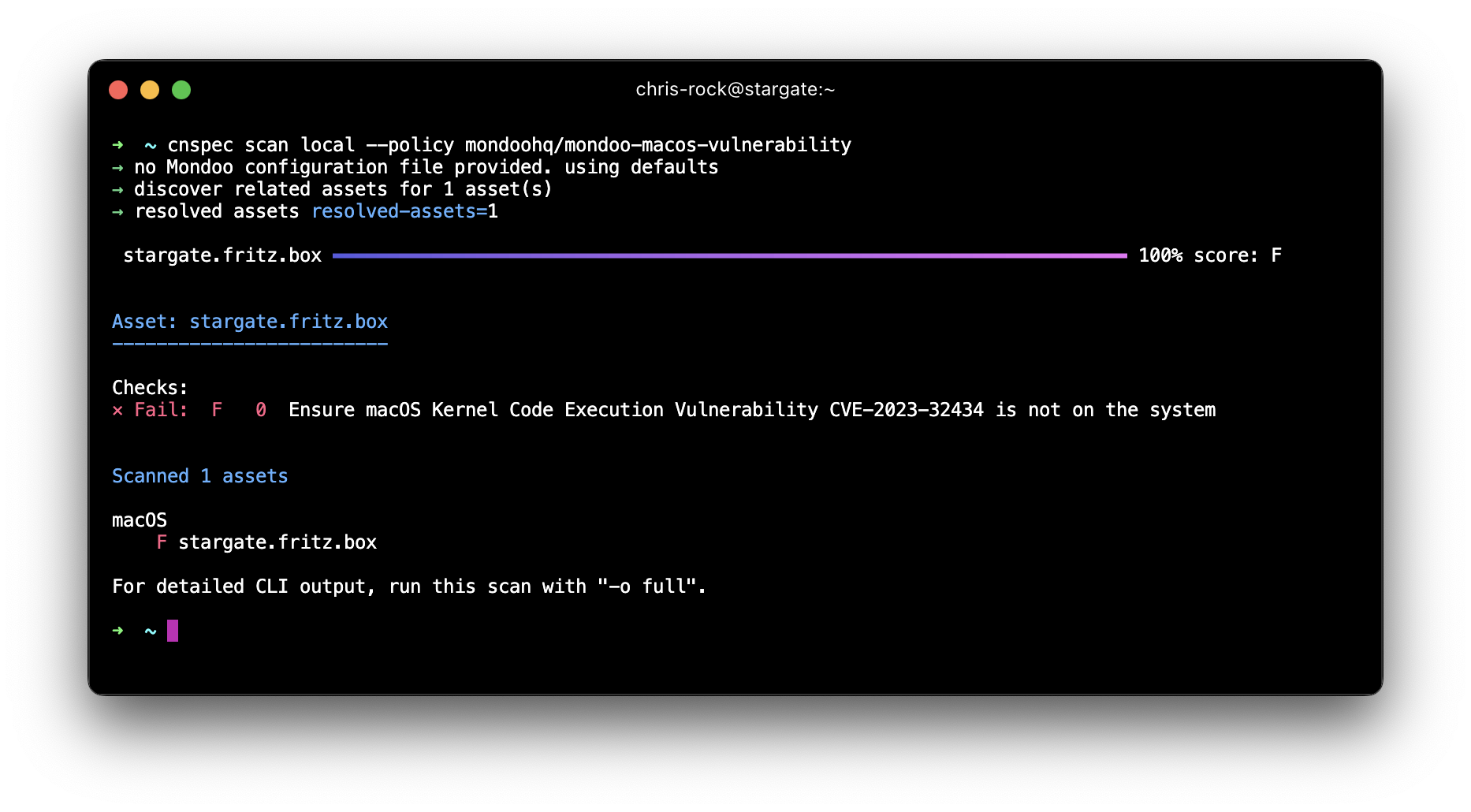
Conclusion: The Necessity of Vigilance
This discovery underscores the constant battle between cybersecurity and cybercriminals. Despite Apple's well-regarded security measures, vulnerabilities happen. The incident reminds all tech users to keep their systems up-to-date and maintain good cybersecurity hygiene. In this digital era, cybersecurity is a shared responsibility. Let's all play our part in maintaining a safer digital space for everyone.
Secure Your Digital Infrastructure Today
Don't leave your systems exposed to threats like CVE-2023-32434. With our open-source solution, cnspec, you can effectively detect and address these vulnerabilities.
Head to our GitHub page to download cnspec and run the macOS vulnerability policy update.


