What is patch management?
Patch management is the process of distributing and applying updates to software, such as operating systems (OS), platforms, and applications. It involves identifying out-dated software within your infrastructure, applying patches to that software, and validating the installation of those patches. These patches are often necessary to fix errors in the software, which are often referred to as vulnerabilities or bugs.
Why is patch management important?
Patch management is important for three main reasons:
- Security: Patch management fixes vulnerabilities in your software (OS, platform, application) that are susceptible to exploitation. It helps your organization to reduce the risk of cyberattacks.
- Compliance: Organizations are often required by regulators to follow strict guidelines because of the constant increase in cyberattacks. Patch management is a necessary part of complying to certain standards, such as PCI-DSS, HIPAA, SOC2, ISO27001, or BSI.
- System uptime: Patch management ensures your software is kept up-to-date and running smoothly without errors causing system downtime.
Finding missing patches with Mondoo
As a part of its full-stack security solution, Mondoo identifies what important patches are missing from your systems. For this blog post, I set up some vagrant Linux machines with out-of-date operating systems. I’ll use them to walk through some different ways that Mondoo shows you the patches needed.
config.vm.define "debian9" do |debian9|
debian9.vm.box = "bento/debian-9"
debian9.vm.network :private_network, ip: "192.168.56.237"
end
config.vm.define "ubuntu2004" do |ub2004|
ub2004.vm.box = "ubuntu/focal64"
ub2004.vm.box_version = "20211021.0.0"
ub2004.vm.network :private_network, ip: "192.168.56.251"
end
config.vm.define "rhel8" do |rhel8|
rhel8.vm.box = "generic/rhel8"
rhel8.vm.box_version = "3.6.13"
rhel8.vm.network :private_network, ip: "192.168.56.242"
end
Prerequisite: Please create a free account on console.mondoo.com.
Mondoo offers different options for scanning a Linux vagrant system:
Option 1: Install Mondoo Client on the Linux system
Option 2: Use vagrant transporter
Option 3: Use SSH transporter
Option 1: Find missing patches with Mondoo
1. Login to the vagrant Debian 9 system:
atomic111:..vagrant-test-boxen ∅> vagrant ssh debian9
Linux debian-9 4.9.0-17-amd64 #1 SMP Debian 4.9.290-1 (2021-12-12)
x86_64
This system is built by the Bento project by Chef Software
More information can be found at https://github.com/chef/bento
The programs included with the Debian GNU/Linux system are free
software; the exact distribution terms for each program are
described in the individual files in /usr/share/doc/*/copyright.
config.vm.define "ubuntu2004" do |ub2004|
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
vagrant@debian-9:~$ sudo -i
root@debian-9:~#
2. Install Mondoo Client:
A. Log into your account at console.mondoo.com
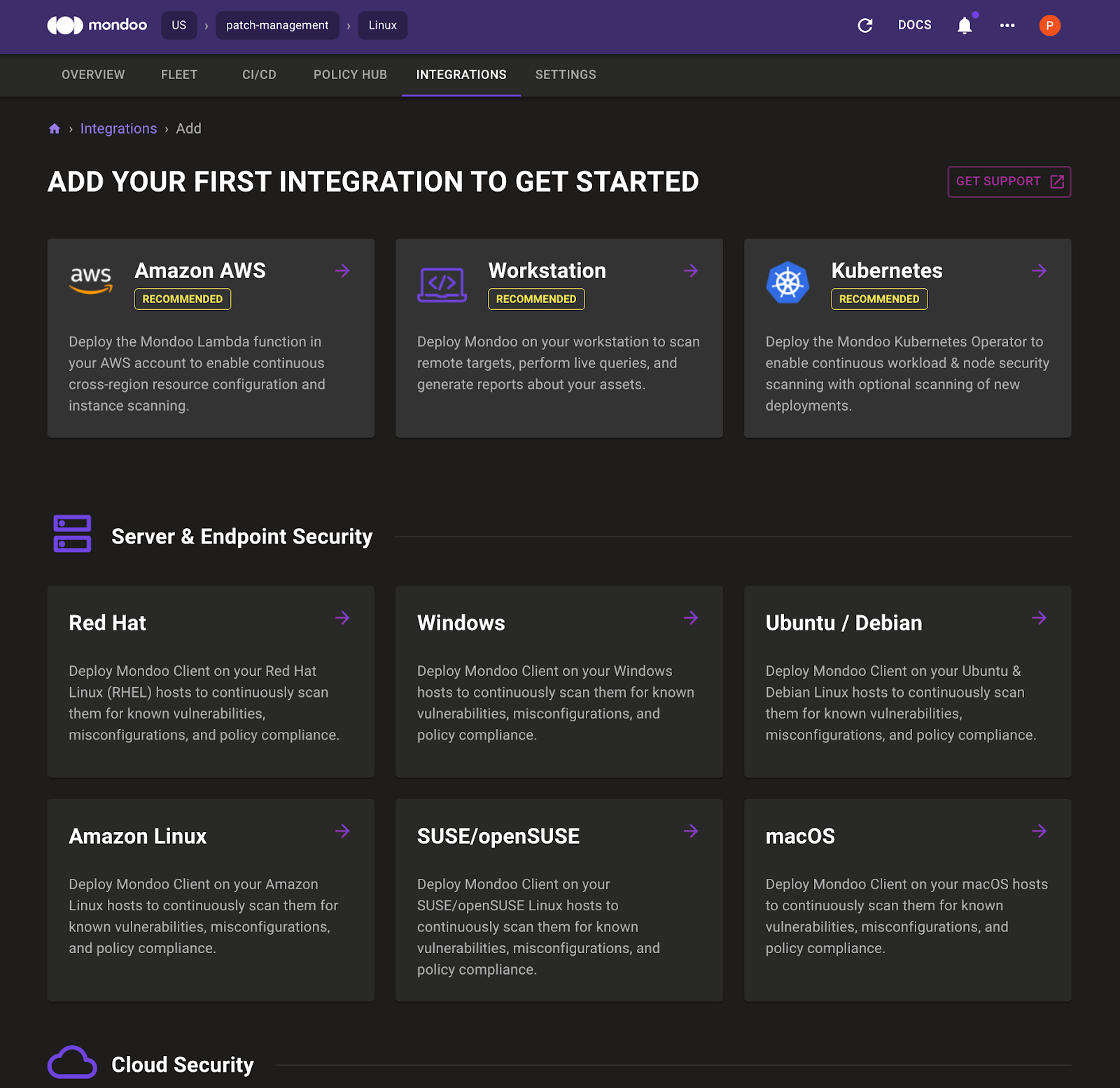
B. Go to the Integrations tab and select Ubuntu/Debian
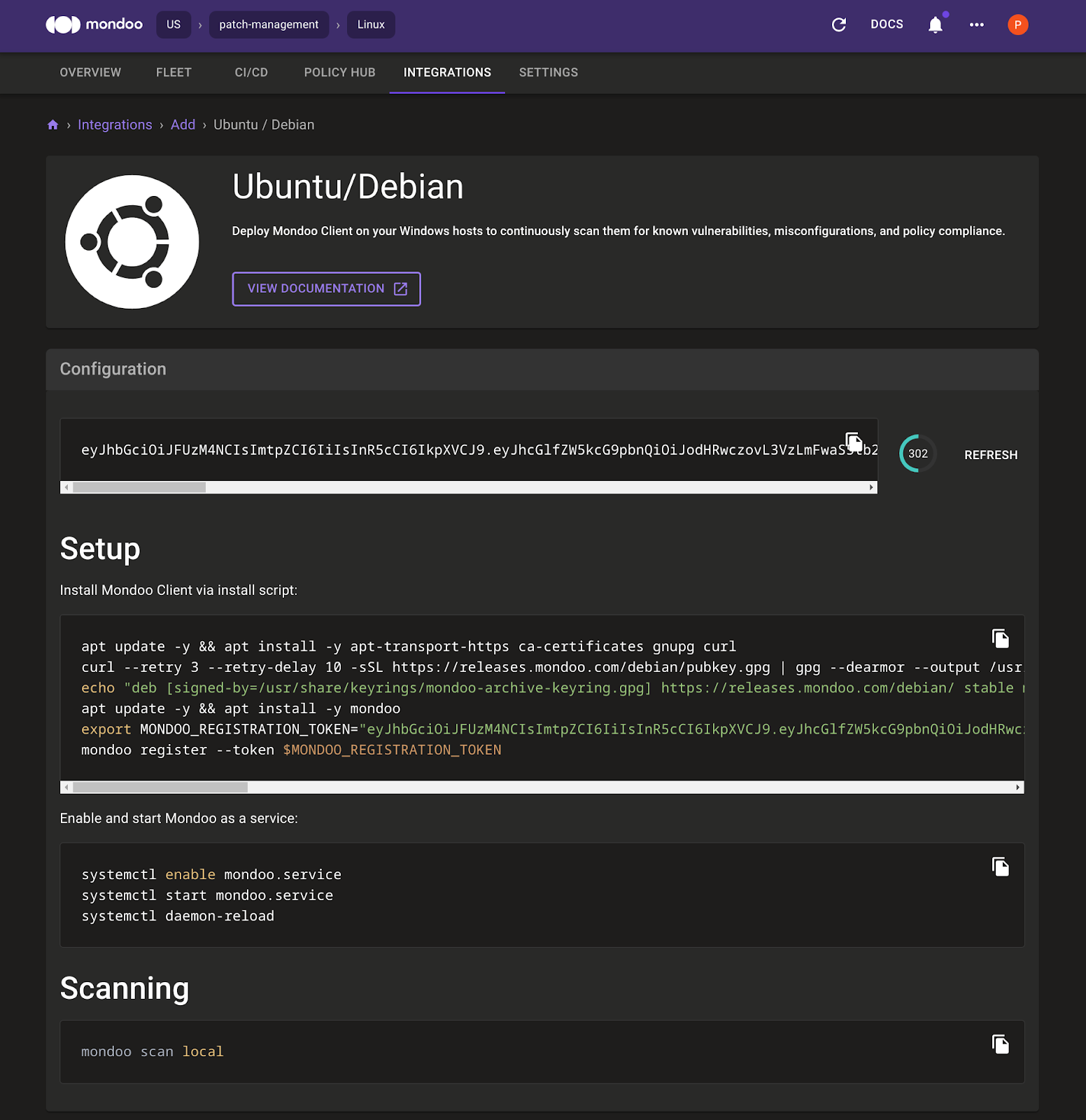
C. Copy the CLI commands provided and paste them in the Debian 9 root shell.
D. After the Mondoo Client installation, type mondoo status to verify that Mondoo Client is registered and working. It should look like this:
root@debian-9:~# mondoo status
→ loaded configuration from /etc/opt/mondoo/mondoo.yml using source
--config
→ Hostname: debian-9
→ IP: 10.0.2.15
→ Platform: debian
→ Release: 9.13
→ Time: 2022-07-01T08:38:09Z
→ Version: 6.4.0 (API Version: 6)
→ API ConnectionConfig: https://us.api.mondoo.com
→ API Status: SERVING
→ API Time: 2022-07-01T08:38:09Z
→ API Version: 6
→ Space: //captain.api.mondoo.app/spaces/keen-kowalevski-169528
→ Client: //agents.api.mondoo.app/spaces/keen-kowalevski-169528/
agents/2BKpZTDtSZFz0xOpHxWGMo5afz1
→ Service Account: //agents.api.mondoo.app/spaces/keen-kowalevski
-169528/serviceaccounts/2BKpZTQlGtWgoCHNyhjaPIa5PjG
→ client is registered
→ client authenticated successfully
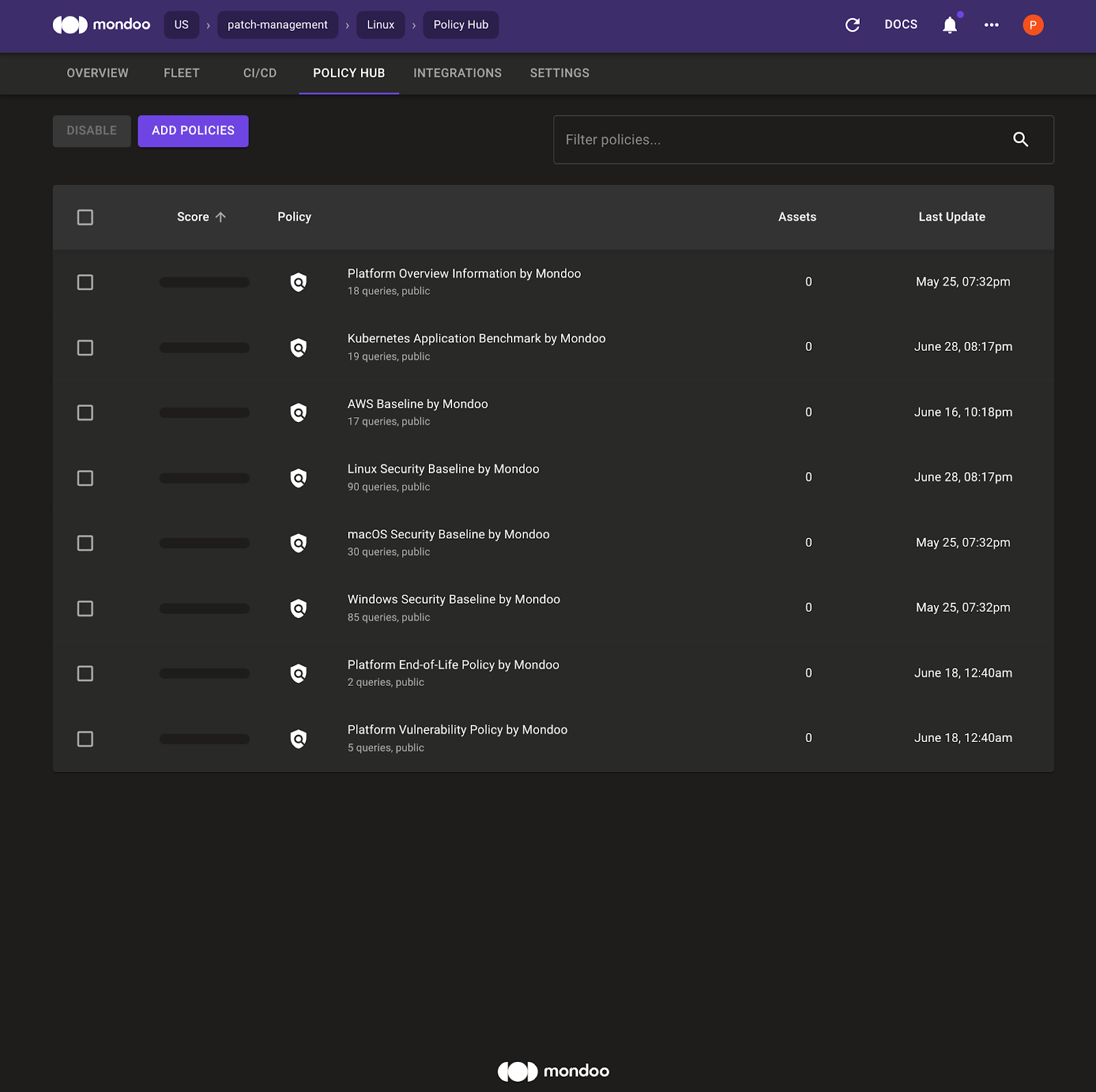
E. Quickly verify that the following policies are enabled for your space:
- Platform End-of-Life Policy by Mondoo
- Platform Vulnerability Policy by Mondoo
Your Policy Hub should look like this:
To scan the vagrant debian 9 system, just type mondoo scan local. Mondoo Client connects to the Mondoo backend and downloads the enabled policies. After the scan, Mondoo Client reports results back to the Mondoo backend:
root@debian-9:~# mondoo scan local
→ Mondoo 6.4.0 (Space: "//captain.api.mondoo.app/spaces/keen-kowalevski-169528",
Service Account: "2BKpZTQlGtWgoCHNyhjaPIa5PjG", Managed Client: "2BKpZTDtSZFz0xOpHxWGMo5afz1")
→ loaded configuration from /etc/opt/mondoo/mondoo.yml using source --config
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=1
→ establish connection to asset debian-9 (baremetal)
███████████████████████████████████████████████████████████████████████████ 100% debian-9
→ send all results asset=debian-9
Data queries:
"9.13"
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
platform.arch: "x86_64"
platform.eol.date: 2020-07-06 00:00:00 +0000 UTC
os.uptime: 2 hours 20 minutes 3 seconds
platform.title: "Debian GNU/Linux"
kernel.installed: [
0: {
name: "4.9.0-17-amd64"
running: true
version: "4.9.290-1"
}
1: {
name: "amd64"
running: false
version: "4.9+80+deb9u15"
... 2 more lines ...
platform.release: "9.13"
packages.list.length: 403
os.hostname: "debian-9"
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "DLA-3008-1"
Mrn: "//vadvisor.api.mondoo.app/advisories/DLA-3008-1"
affected: [
0: {
affected: true
arch: "amd64"
available: "1.1.0l-1~deb9u6"
... 7466 more lines ...
Controls:
✓ Pass: Ensure rsyslog is installed
✕ Fail: Ensure SSH LogLevel is appropriate
✕ Fail: Ensure audit is installed
✕ Fail: Ensure session initiation information is collected
✕ Fail: Ensure the platform is not End-of-Life
✓ Pass: Ensure HTTP Proxy server is stopped and not enabled
✕ Fail: Ensure IPv6 router advertisements are not accepted
✓ Pass: Ensure core dumps are restricted
✓ Pass: Ensure Avahi server is stopped and not enabled
✓ Pass: Ensure rsh server is stopped and not enabled
✕ Fail: Ensure discretionary access control permission modification events are collected
✓ Pass: Ensure talk server is stopped and not enabled
✓ Pass: Ensure X Window System is not installed
✕ Fail: Ensure Reverse Path Filtering is enabled
✕ Fail: Ensure system administrator actions (sudolog) are collected
✓ Pass: Ensure permissions on /etc/gshadow are configured
✓ Pass: Ensure telnet server is stopped and not enabled
✕ Fail: Ensure kernel module loading and unloading is collected
✕ Fail: Ensure SSH PermitEmptyPasswords is disabled
✓ Pass: Ensure permissions on SSH private host key files are configured
✓ Pass: Ensure permissions on SSH public host key files are configured
✓ Pass: Ensure permissions on /etc/passwd are configured
✕ Fail: Ensure events that modify the system's network environment are collected
✕ Fail: Platform is not end-of-life
✕ Fail: Ensure ICMP redirects are not accepted
✕ Fail: Ensure changes to system administration scope (sudoers) is collected
✕ Fail: Ensure SSH X11 forwarding is disabled
✕ Fail: Ensure journald is configured to compress large log files
✓ Pass: Ensure address space layout randomization (ASLR) is enabled
✓ Pass: Ensure permissions on /etc/group- are configured
✓ Pass: Ensure SNMP server is stopped and not enabled
✓ Pass: Ensure HTTP server is stopped and not enabled
✓ Pass: Ensure tftp server is stopped and not enabled
✕ Fail: Ensure AIDE is installed
✓ Pass: Ensure mail transfer agent is configured for local-only mode
✕ Fail: Ensure login and logout events are collected
✓ Pass: Ensure permissions on /etc/group are configured
✕ Fail: Ensure only strong MAC algorithms are used
✕ Fail: Ensure only strong ciphers are used
✓ Pass: Ensure LDAP server is stopped and not enabled
✕ Fail: Ensure journald is configured to send logs to rsyslog
✕ Fail: Ensure SSH IgnoreRhosts is enabled
✓ Pass: Ensure permissions on /etc/shadow are configured
✓ Pass: Ensure rsyslog Service is enabled
✕ Fail: Ensure SSH HostbasedAuthentication is disabled
✕ Fail: Ensure SSH root login is disabled
✕ Fail: Ensure auditing for processes that start prior to audit is enabled
✓ Pass: Ensure CUPS is not enabled
✕ Fail: Ensure secure ICMP redirects are not accepted
! Error: Ensure SSH LoginGraceTime is set to one minute or less
! Error: Ensure system is disabled when audit logs are full
✕ Fail: Ensure journald is configured to write logfiles to persistent disk
✕ Fail: Ensure no known platform advisories exist
✓ Pass: Ensure DHCP server is stopped and not enabled
✕ Fail: Ensure file deletion events by users are collected
✓ Pass: Ensure permissions on /etc/passwd- are configured
✓ Pass: Ensure DNS server is stopped and not enabled
✓ Pass: Ensure broadcast ICMP requests are ignored
✕ Fail: Ensure packet redirect sending is disabled
✓ Pass: Ensure rsyslog default file permissions configured
✕ Fail: Ensure unsuccessful unauthorized file access attempts are collected
✓ Pass: Ensure IMAP and POP3 server is stopped and not enabled
✕ Fail: Ensure permissions on all logfiles are configured
✕ Fail: Ensure events that modify the system's Mandatory Access Controls are collected
✓ Pass: Ensure bogus ICMP responses are ignored
✓ Pass: Ensure TCP SYN Cookies is enabled
✕ Fail: Ensure the audit configuration is immutable
! Error: Ensure SSH MaxAuthTries is set to 4 or less
✓ Pass: Ensure FTP server is stopped and not enabled
✕ Fail: Ensure that strong Key Exchange algorithms are used
✕ Fail: Ensure SSH access is limited
✓ Pass: Ensure rsync service is not enabled
✕ Fail: Ensure filesystem integrity is regularly checked
✕ Fail: Ensure SSH Protocol is set to 2
✕ Fail: Ensure suspicious packets are logged
✕ Fail: Ensure events that modify date and time information are collected
✕ Fail: Ensure NFS and RPC are not enabled
✓ Pass: Ensure NIS server is stopped and not enabled
✕ Fail: Ensure SSH PermitUserEnvironment is disabled
✕ Fail: Ensure events that modify user/group information are collected
✕ Fail: Ensure successful file system mounts are collected
✕ Fail: Ensure SSH warning banner is configured
✕ Fail: Ensure permissions on /etc/ssh/sshd_config are configured
✓ Pass: Ensure prelink is disabled
✓ Pass: Ensure IP forwarding is disabled
✕ Fail: Ensure no known platform CVEs exist
! Error: Ensure SSH Idle Timeout Interval is configured
! Error: Ensure audit logs are not automatically deleted
✕ Fail: Ensure source routed packets are not accepted
✓ Pass: Ensure Samba is not enabled
! Error: Ensure audit log storage size is configured
✓ Pass: Ensure permissions on /etc/shadow- are configured
✓ Pass: Ensure permissions on /etc/gshadow- are configured
✕ Fail: Ensure audit service is enabled
Vulnerabilities:
■ SCORE PACKAGE INSTALLED
FIXED AVAILABLE
■ 0 tzdata 2021a-0+deb9u2
2021a-0+deb9u4 2021a-0+deb9u4
■ 0 debian-archive-keyring 2017.5+deb9u1
2017.5+deb9u2 2017.5+deb9u2
■ 4.6 udev 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 systemd-sysv 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 systemd 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libudev1 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libsystemd0 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libpam-systemd 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libavahi-common3 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 4.6 libavahi-common-data 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 4.6 libavahi-client3 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 4.6 avahi-autoipd 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 5 zlib1g 1:1.2.8.dfsg-5
1:1.2.8.dfsg-5+deb9u1 1:1.2.8.dfsg-5+deb9u1
■ 5 libssl1.0.2 1.0.2u-1~deb9u6
1.0.2u-1~deb9u7 1.0.2u-1~deb9u7
■ 5 liblwres141 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisccfg140 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisccc140 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisc160 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisc-export160 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libglib2.0-data 2.50.3-2+deb9u2
2.50.3-2+deb9u3 2.50.3-2+deb9u3
■ 5 libglib2.0-0 2.50.3-2+deb9u2
2.50.3-2+deb9u3 2.50.3-2+deb9u3
■ 5 libdns162 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libdns-export162 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libbind9-140 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 host 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 dnsutils 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 bind9-host 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 6.5 libsasl2-modules-db 2.1.27~101-g0780600+dfsg-3+deb9u1
2.1.27~101-g0780600+dfsg-3+deb9u2 2.1.27~101-g0780600+dfsg-
3+deb9u2
■ 6.5 libsasl2-modules 2.1.27~101-g0780600+dfsg-3+deb9u1
2.1.27~101-g0780600+dfsg-3+deb9u2 2.1.27~101-g0780600+dfsg-
3+deb9u2
■ 6.5 libsasl2-2 2.1.27~101-g0780600+dfsg-3+deb9u1
2.1.27~101-g0780600+dfsg-3+deb9u2 2.1.27~101-g0780600+dfsg-
3+deb9u2
■ 7 libfribidi0 0.19.7-1+deb9u1
0.19.7-1+deb9u2 0.19.7-1+deb9u2
■ 7.1 xz-utils 5.2.2-1.2+b1
5.2.2-1.2+deb9u1 5.2.2-1.2+deb9u1
■ 7.1 liblzma5 5.2.2-1.2+b1
5.2.2-1.2+deb9u1 5.2.2-1.2+deb9u1
■ 7.1 gzip 1.6-5+b1
1.6-5+deb9u1 1.6-5+deb9u1
■ 7.2 libcups2 2.2.1-8+deb9u7
2.2.1-8+deb9u8 2.2.1-8+deb9u8
■ 7.2 cifs-utils 2:6.7-1
2:6.7-1+deb9u1 2:6.7-1+deb9u1
■ 7.5 rsyslog 8.24.0-1+deb9u1
8.24.0-1+deb9u2 8.24.0-1+deb9u3
■ 7.5 python2.7-minimal 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 python2.7 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libpython2.7-stdlib 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libpython2.7-minimal 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libpython2.7 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libldap-common 2.4.44+dfsg-5+deb9u8
2.4.44+dfsg-5+deb9u9 2.4.44+dfsg-5+deb9u9
■ 7.5 libldap-2.4-2 2.4.44+dfsg-5+deb9u8
2.4.44+dfsg-5+deb9u9 2.4.44+dfsg-5+deb9u9
■ 7.5 libexpat1 2.2.0-2+deb9u3
2.2.0-2+deb9u5 2.2.0-2+deb9u5
■ 7.5 libdpkg-perl 1.18.25
1.18.26 1.18.26
■ 7.5 dpkg 1.18.25
1.18.26 1.18.26
■ 8.8 libxml2 2.9.4+dfsg1-2.2+deb9u5
2.9.4+dfsg1-2.2+deb9u7 2.9.4+dfsg1-2.2+deb9u7
■ 9 linux-image-4.9.0-17-amd64 4.9.290-1
4.9.320-2
■ 9.3 xxd 2:8.0.0197-4+deb9u3
2:8.0.0197-4+deb9u7 2:8.0.0197-4+deb9u7
■ 9.3 vim-tiny 2:8.0.0197-4+deb9u3
2:8.0.0197-4+deb9u7 2:8.0.0197-4+deb9u7
■ 9.3 vim-common 2:8.0.0197-4+deb9u3
2:8.0.0197-4+deb9u7 2:8.0.0197-4+deb9u7
■ 9.8 libgc1c2 1:7.4.2-8
1:7.4.2-8+deb9u1 1:7.4.2-8+deb9u1
■ 10 openssl 1.1.0l-1~deb9u4
1.1.0l-1~deb9u6 1.1.0l-1~deb9u6
■ 10 libssl1.1 1.1.0l-1~deb9u4
1.1.0l-1~deb9u6 1.1.0l-1~deb9u6
Overall CVSS score: 10.0
Summary
========================
Target: debian-9
Score: D 15/100 (100% completed)
✓ Passed: ██████ 41% (39)
✕ Failed: ████████ 52% (49)
! Errors: █ 6% (6)
» Skipped: 0% (0)
Policies:
F 0 Platform End-of-Life Policy by Mondoo
F 0 Platform Vulnerability Policy by Mondoo
. .. Platform Overview Information by Mondoo
C 46 Linux Security Baseline by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2BKtQFRnpaTBMJGKomPvtRN4vSS?spaceId=keen-kowalevski-169528
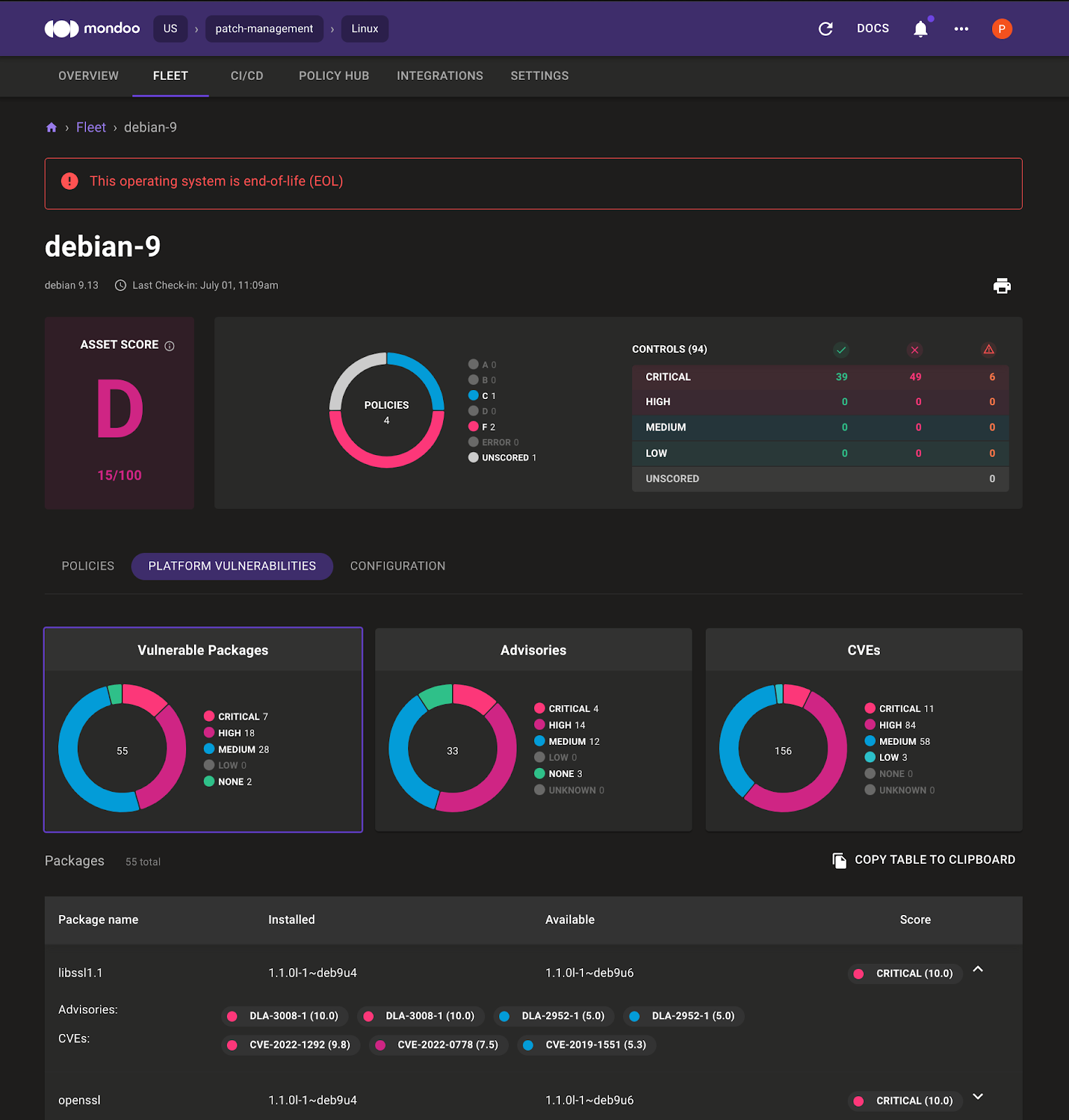
Now you can see the outdated packages on the machine and which package version you must install to fix the specific vulnerability. You can view results in the Mondoo Dashboard:
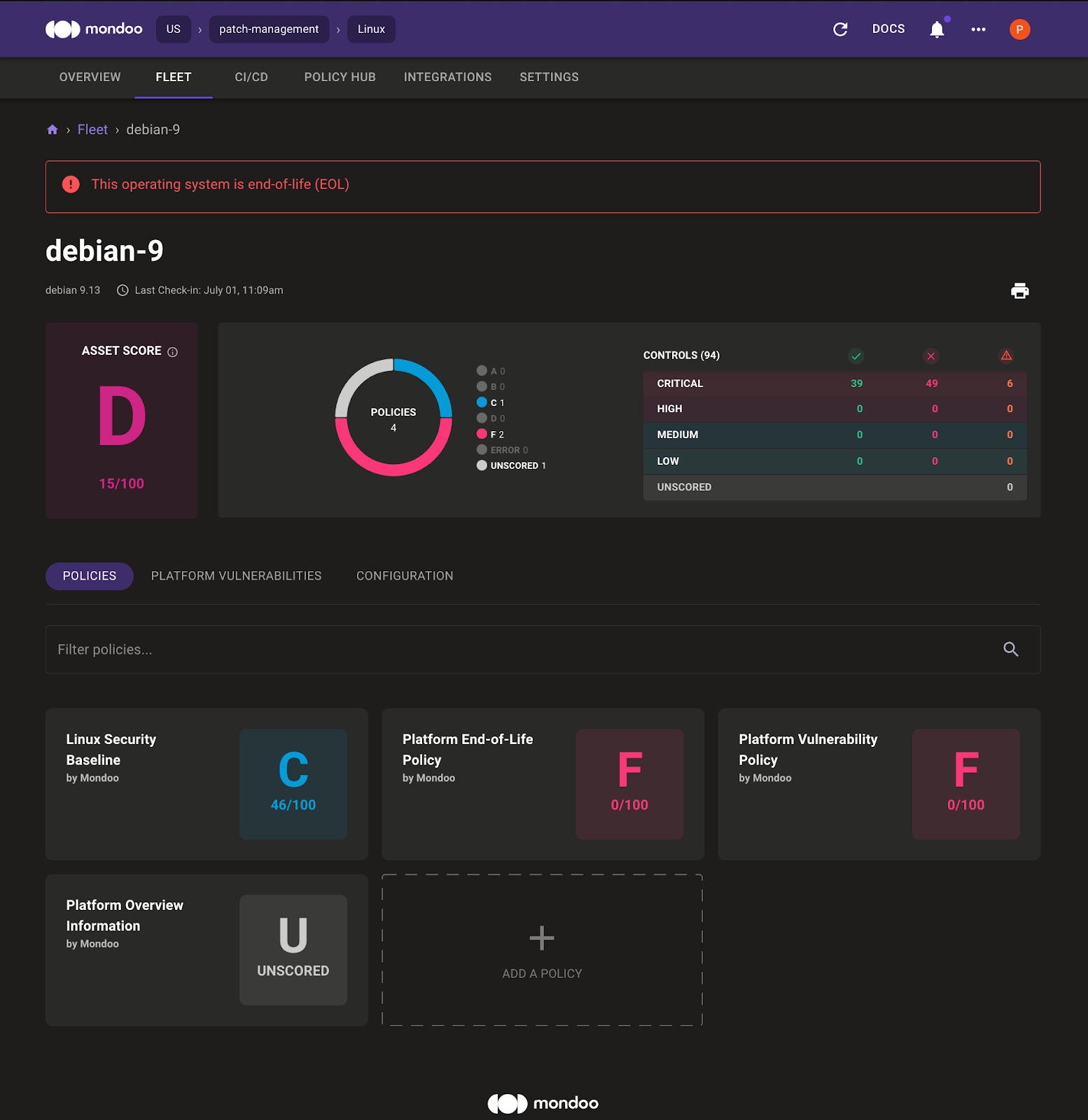
In the system overview, the Mondoo Dashboard highlights that the Debian 9 operating system is end-of-life. By default there is also a Linux Security Baseline enabled. Select Platform Vulnerabilities to see the vulnerable packages. Mondoo shows:
- Outdated packages
- CVEs that belong to the package
- Which package version you must install to fix the vulnerability
- How critical the vulnerability is
- An overview of the advisories and CVEs
Option 2: Scan a Linux vagrant machine via vagrant transporter
Install and register Mondoo Client on your host system running the vagrant Debian 9 system and then run the following command:
atomic111:..vagrant-test-boxen ∅> mondoo scan ssh vagrant@192.168.56.237 -p 'vagrant' --sudo
→ Mondoo 6.4.0 (Space: "//captain.api.mondoo.app/spaces/keen-kowalevski-169528",
Service Account: "2BKpZTQlGtWgoCHNyhjaPIa5PjG", Managed Client: "2BKpZTDtSZFz0xOpHxWGMo5afz1")
→ loaded configuration from /home/user/.config/mondoo/mondoo-patch.yml using source --config
→ discover related assets for 1 asset(s)
→ resolved assets resolved-assets=1
→ establish connection to asset debian-9 (unknown)
███████████████████████████████████████████████████████████████████████████ 100% debian-9
→ send all results asset=debian-9
Data queries:
mondoo.jobEnvironment: {
id: "client.mondoo.com"
name: "Mondoo Client"
}
platform.arch: "x86_64"
platform.vulnerabilityReport: {
advisories: [
0: {
ID: "DLA-3008-1"
Mrn: "//vadvisor.api.mondoo.app/advisories/DLA-3008-1"
affected: [
0: {
affected: true
arch: "amd64"
available: "1.1.0l-1~deb9u6"
... 7466 more lines ...
os.uptime: 3 hours 17 minutes 3 seconds
packages.list.length: 403
platform.eol.date: 2020-07-06 02:00:00 +0200 CEST
platform.release: "9.13"
"9.13"
os.hostname: "debian-9"
kernel.installed: [
0: {
name: "4.9.0-17-amd64"
running: true
version: "4.9.290-1"
}
1: {
name: "amd64"
running: false
version: "4.9+80+deb9u15"
... 2 more lines ...
platform.title: "Debian GNU/Linux"
Controls:
✕ Fail: Ensure permissions on /etc/ssh/sshd_config are configured
✕ Fail: Ensure no known platform CVEs exist
✕ Fail: Ensure system administrator actions (sudolog) are collected
✓ Pass: Ensure mail transfer agent is configured for local-only mode
✕ Fail: Ensure SSH IgnoreRhosts is enabled
✕ Fail: Ensure successful file system mounts are collected
✕ Fail: Ensure SSH LogLevel is appropriate
✕ Fail: Ensure journald is configured to write logfiles to persistent disk
✕ Fail: Ensure unsuccessful unauthorized file access attempts are collected
✕ Fail: Ensure SSH PermitEmptyPasswords is disabled
✓ Pass: Ensure talk server is stopped and not enabled
! Error: Ensure audit logs are not automatically deleted
✓ Pass: Ensure DNS server is stopped and not enabled
✕ Fail: Ensure journald is configured to compress large log files
✕ Fail: Ensure source routed packets are not accepted
✓ Pass: Ensure Samba is not enabled
✕ Fail: Ensure changes to system administration scope (sudoers) is collected
✓ Pass: Ensure permissions on SSH public host key files are configured
✓ Pass: Ensure IMAP and POP3 server is stopped and not enabled
✓ Pass: Ensure rsh server is stopped and not enabled
✕ Fail: Ensure kernel module loading and unloading is collected
✕ Fail: Ensure filesystem integrity is regularly checked
✓ Pass: Ensure DHCP server is stopped and not enabled
✕ Fail: Ensure events that modify user/group information are collected
! Error: Ensure SSH MaxAuthTries is set to 4 or less
✓ Pass: Ensure HTTP Proxy server is stopped and not enabled
! Error: Ensure audit log storage size is configured
✕ Fail: Ensure AIDE is installed
✕ Fail: Ensure the platform is not End-of-Life
✕ Fail: Ensure that strong Key Exchange algorithms are used
✕ Fail: Ensure Reverse Path Filtering is enabled
✓ Pass: Ensure bogus ICMP responses are ignored
✓ Pass: Ensure permissions on SSH private host key files are configured
✓ Pass: Ensure TCP SYN Cookies is enabled
✓ Pass: Ensure IP forwarding is disabled
✓ Pass: Ensure permissions on /etc/gshadow are configured
✕ Fail: Ensure auditd is installed
✓ Pass: Ensure tftp server is stopped and not enabled
✕ Fail: Ensure ICMP redirects are not accepted
✓ Pass: Ensure broadcast ICMP requests are ignored
✕ Fail: Ensure NFS and RPC are not enabled
✕ Fail: Ensure events that modify date and time information are collected
✓ Pass: Ensure X Window System is not installed
✓ Pass: Ensure rsync service is not enabled
✕ Fail: Ensure SSH Protocol is set to 2
✕ Fail: Ensure SSH warning banner is configured
✕ Fail: Ensure SSH root login is disabled
✕ Fail: Ensure suspicious packets are logged
✕ Fail: Ensure SSH access is limited
✕ Fail: Ensure session initiation information is collected
✓ Pass: Ensure permissions on /etc/group are configured
✕ Fail: Ensure secure ICMP redirects are not accepted
✕ Fail: Ensure IPv6 router advertisements are not accepted
✕ Fail: Ensure auditing for processes that start prior to auditd is enabled
✕ Fail: Ensure events that modify the system's Mandatory Access Controls are collected
✓ Pass: Ensure permissions on /etc/group- are configured
✕ Fail: Ensure SSH PermitUserEnvironment is disabled
✕ Fail: Ensure journald is configured to send logs to rsyslog
✓ Pass: Ensure address space layout randomization (ASLR) is enabled
✓ Pass: Ensure NIS server is stopped and not enabled
✕ Fail: Ensure events that modify the system's network environment are collected
✓ Pass: Ensure telnet server is stopped and not enabled
✕ Fail: Ensure permissions on all logfiles are configured
✕ Fail: Ensure packet redirect sending is disabled
✕ Fail: Platform is not end-of-life
✓ Pass: Ensure FTP server is stopped and not enabled
✓ Pass: Ensure HTTP server is stopped and not enabled
✕ Fail: Ensure discretionary access control permission modification events are collected
✓ Pass: Ensure core dumps are restricted
! Error: Ensure SSH Idle Timeout Interval is configured
✓ Pass: Ensure permissions on /etc/shadow- are configured
✓ Pass: Ensure permissions on /etc/passwd- are configured
✕ Fail: Ensure file deletion events by users are collected
✕ Fail: Ensure only strong MAC algorithms are used
✕ Fail: Ensure login and logout events are collected
! Error: Ensure system is disabled when audit logs are full
✓ Pass: Ensure permissions on /etc/passwd are configured
✓ Pass: Ensure permissions on /etc/gshadow- are configured
✕ Fail: Ensure auditd service is enabled
✓ Pass: Ensure prelink is disabled
✓ Pass: Ensure permissions on /etc/shadow are configured
✕ Fail: Ensure only strong ciphers are used
✓ Pass: Ensure rsyslog Service is enabled
✕ Fail: Ensure SSH X11 forwarding is disabled
✕ Fail: Ensure no known platform advisories exist
✓ Pass: Ensure SNMP server is stopped and not enabled
✓ Pass: Ensure rsyslog default file permissions configured
✓ Pass: Ensure Avahi server is stopped and not enabled
✓ Pass: Ensure rsyslog is installed
✓ Pass: Ensure CUPS is not enabled
✕ Fail: Ensure the audit configuration is immutable
! Error: Ensure SSH LoginGraceTime is set to one minute or less
✕ Fail: Ensure SSH HostbasedAuthentication is disabled
✓ Pass: Ensure LDAP server is stopped and not enabled
Vulnerabilities:
■ SCORE PACKAGE INSTALLED
FIXED AVAILABLE
■ 0 tzdata 2021a-0+deb9u2
2021a-0+deb9u4 2021a-0+deb9u4
■ 0 debian-archive-keyring 2017.5+deb9u1
2017.5+deb9u2 2017.5+deb9u2
■ 4.6 udev 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 systemd-sysv 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 systemd 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libudev1 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libsystemd0 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libpam-systemd 232-25+deb9u13
232-25+deb9u14 232-25+deb9u14
■ 4.6 libavahi-common3 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 4.6 libavahi-common-data 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 4.6 libavahi-client3 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 4.6 avahi-autoipd 0.6.32-2
0.6.32-2+deb9u1 0.6.32-2+deb9u1
■ 5 zlib1g 1:1.2.8.dfsg-5
1:1.2.8.dfsg-5+deb9u1 1:1.2.8.dfsg-5+deb9u1
■ 5 libssl1.0.2 1.0.2u-1~deb9u6
1.0.2u-1~deb9u7 1.0.2u-1~deb9u7
■ 5 liblwres141 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisccfg140 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisccc140 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisc160 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libisc-export160 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libglib2.0-data 2.50.3-2+deb9u2
2.50.3-2+deb9u3 2.50.3-2+deb9u3
■ 5 libglib2.0-0 2.50.3-2+deb9u2
2.50.3-2+deb9u3 2.50.3-2+deb9u3
■ 5 libdns162 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libdns-export162 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 libbind9-140 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 host 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 dnsutils 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 5 bind9-host 1:9.10.3.dfsg.P4-12.3+deb9u10
1:9.10.3.dfsg.P4-12.3+deb9u12 1:9.10.3.dfsg.P4-12.3+deb
9u12
■ 6.5 libsasl2-modules-db 2.1.27~101-g0780600+dfsg-3+deb9u1
2.1.27~101-g0780600+dfsg-3+deb9u2 2.1.27~101-g0780600+dfsg-
3+deb9u2
■ 6.5 libsasl2-modules 2.1.27~101-g0780600+dfsg-3+deb9u1
2.1.27~101-g0780600+dfsg-3+deb9u2 2.1.27~101-g0780600+dfsg-
3+deb9u2
■ 6.5 libsasl2-2 2.1.27~101-g0780600+dfsg-3+deb9u1
2.1.27~101-g0780600+dfsg-3+deb9u2 2.1.27~101-g0780600+dfsg-
3+deb9u2
■ 7 libfribidi0 0.19.7-1+deb9u1
0.19.7-1+deb9u2 0.19.7-1+deb9u2
■ 7.1 xz-utils 5.2.2-1.2+b1
5.2.2-1.2+deb9u1 5.2.2-1.2+deb9u1
■ 7.1 liblzma5 5.2.2-1.2+b1
5.2.2-1.2+deb9u1 5.2.2-1.2+deb9u1
■ 7.1 gzip 1.6-5+b1
1.6-5+deb9u1 1.6-5+deb9u1
■ 7.2 libcups2 2.2.1-8+deb9u7
2.2.1-8+deb9u8 2.2.1-8+deb9u8
■ 7.2 cifs-utils 2:6.7-1
2:6.7-1+deb9u1 2:6.7-1+deb9u1
■ 7.5 rsyslog 8.24.0-1+deb9u1
8.24.0-1+deb9u2 8.24.0-1+deb9u3
■ 7.5 python2.7-minimal 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 python2.7 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libpython2.7-stdlib 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libpython2.7-minimal 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libpython2.7 2.7.13-2+deb9u5
2.7.13-2+deb9u6 2.7.13-2+deb9u6
■ 7.5 libldap-common 2.4.44+dfsg-5+deb9u8
2.4.44+dfsg-5+deb9u9 2.4.44+dfsg-5+deb9u9
■ 7.5 libldap-2.4-2 2.4.44+dfsg-5+deb9u8
2.4.44+dfsg-5+deb9u9 2.4.44+dfsg-5+deb9u9
■ 7.5 libexpat1 2.2.0-2+deb9u3
2.2.0-2+deb9u5 2.2.0-2+deb9u5
■ 7.5 libdpkg-perl 1.18.25
1.18.26 1.18.26
■ 7.5 dpkg 1.18.25
1.18.26 1.18.26
■ 8.8 libxml2 2.9.4+dfsg1-2.2+deb9u5
2.9.4+dfsg1-2.2+deb9u7 2.9.4+dfsg1-2.2+deb9u7
■ 9 linux-image-4.9.0-17-amd64 4.9.290-1
4.9.320-2
■ 9.3 xxd 2:8.0.0197-4+deb9u3
2:8.0.0197-4+deb9u7 2:8.0.0197-4+deb9u7
■ 9.3 vim-tiny 2:8.0.0197-4+deb9u3
2:8.0.0197-4+deb9u7 2:8.0.0197-4+deb9u7
■ 9.3 vim-common 2:8.0.0197-4+deb9u3
2:8.0.0197-4+deb9u7 2:8.0.0197-4+deb9u7
■ 9.8 libgc1c2 1:7.4.2-8
1:7.4.2-8+deb9u1 1:7.4.2-8+deb9u1
■ 10 openssl 1.1.0l-1~deb9u4
1.1.0l-1~deb9u6 1.1.0l-1~deb9u6
■ 10 libssl1.1 1.1.0l-1~deb9u4
1.1.0l-1~deb9u6 1.1.0l-1~deb9u6
Overall CVSS score: 10.0
Summary
========================
Target: debian-9
Score: D 15/100 (100% completed)
✓ Passed: ██████ 41% (39)
✕ Failed: ████████ 52% (49)
! Errors: █ 6% (6)
» Skipped: 0% (0)
Policies:
. .. Platform Overview Information by Mondoo
F 0 Platform Vulnerability Policy by Mondoo
F 0 Platform End-of-Life Policy by Mondoo
C 46 Linux Security Baseline by Mondoo
Report URL: https://console.mondoo.com/space/fleet/2BKtQFRnpaTBMJGKomPvtRN4vSS?spaceId=keen-kowalevski-169528
Scan other operating systems
You can also scan the Red Hat 8 and Ubuntu 20.04 systems I set up for this blog post. Use the installed Mondoo Client, ssh transporter, or vagrant transporter:
Scan via vagrant transporter:
mondoo scan vagrant rhel8
mondoo scan vagrant ubuntu2004
Scan via ssh transporter:
mondoo scan ssh vagrant@192.168.56.242 -p 'vagrant' --sudo --insecure
-i .vagrant/machines/rhel8/virtualbox/private_key
mondoo scan ssh vagrant@192.168.56.251 -p 'vagrant' --sudo --insecure
-i .vagrant/machines/ubuntu2004/virtualbox/private_key
Don’t stop at scanning the machines I set up for this exercise! You can follow the same steps to scan your own infrastructure.
Mondoo’s full-stack security solution identifies vulnerabilities and provides steps to fix the problems. Keep scanning! If you have questions, we’d love to help you on Slack.




